Assets
Overview
Assets are hostnames or IP addresses. Asset groups are used as a filtration option. An asset group can be created using hosts from multiple scans or from the same scan.
An Asset represents the hostname or IP address entered into beSECURE. Each asset is assigned a value to represent its the hostname or IP address has on the score for the network that contains the asset, as well as the score of the Organization containing the Network.
By default, all assets are given a Value of Normal. However, changing the Value assigned to an asset gives you greater control over weighting and scores. Valid Values range from 0 (Ignore) to 100 (High). A value of Normal represents the median value of 50, and gives no special weight to the host in question.
-
Example 1: If a scan is running for a Linux server, Windows server, and desktop IP addresses, you can create an asset group just for the Linux server. This creates an option for a “filtered” report only for the Linux server.
-
Example 2: There are five different scans running. The asset group allows data from different scans to be combined into groups to show vulnerabilities.
beSECURE can display vulnerability information in two different views:
-
IT Assets - Designed for IT personnel
-
Displays Organization, Scan Name, Host, Risk, Vulnerability Name, Service and Port, and Scan Date information.
-
The hyperlinks in the data table go directly to the specific Vulnerability Details page in beSECURE.
-
-
OT Assets - Operational Technology
-
Displays Organization, Scan Name, Operating System, Host, Net BIOS, Log, Manager, and Scan Date information.
-
The hyperlink for the hosts shows the specific ports the vulnerabilities were found on.
-
The Manager option allows you assign assets to a person and creates a log displaying who the manager switched to, and what notes the manager kept.
-
The “Previous Findings” option compares past data to with current data.
-
Creating an Asset Group
To create an asset group, do the following:
-
Log in to beSECURE.
-
Select Results > Assets > Groups.
-
Select the New button.
-
In the Name box, enter a name for the group.
-
Select Apply.
-
On the Asset Group List page, select the group you just created.
-
On the Asset Group Details page, you can set the following options:
-
Settings tab - Assign a parent group if there’s a group hierarchy, assign a color to differentiate this group from others, and see which hosts are in the group.
-
Automations tab- Allows an asset group to be configured with specific information using filters such as Hosts, Port, High, or Medium Risk.
-
Select Select one to add multiple automation options. For example, you can add a filter for hosts with more than one medium or high risk or vulnerabilities from a specific vulnerability category.
-
The Primary Search Criteria is a general filter including the Organization and Scan Name.
-
The Secondary Search Criteria allows you to add more specific filters.
-
-
Permissions tab - You can assign a user to the “owned by” category giving that them control over the asset group.
-
-
Select Save and Test to show how many matches are returned up for the asset group you are creating.
-
Select Save and Run to save your changes and activate the asset group.
-
If are making changes to an existing asset group, select Modify.
To generate an HTML, PDF, CSV, or XML formatted report of the asset group, select the corresponding icon from the upper-right corner of the page.
Generating a report using the Asset Group option
To generate a report using the Asset Group option, do the following:
-
Log in to beSECURE.
-
Select Results > Reports.
-
On the Report Download page, select Generate Report. The Generate report dialog appears.
-
Select an Organization.
-
Select a Scan name.
-
Select a Scan Date.
-
Select an Asset Group.
-
Select a Report Type.
-
Select Generate.
Searching for asset groups
To search for a specific asset group, do the following:
-
Log in to beSECURE.
-
Select Results > Assets > Search.
-
On the Assets Search page, use the provided filters to search assets groups based on Scan Name, Operating System, Organizations, and Host Name.
Searching for vulnerabilities by asset group
To search for vulnerabilities by asset group, do the following:
-
Log in to beSECURE.
-
Select Results > Search.
-
On the Vulnerability Search page, in addition to other filters, make a selection from the Asset Group box.
Viewing IT Assets
The IT Assets list contains a list of assets focused on vulnerabilities per asset. To view the IT Assets List, do the following:
-
Log in to beSECURE.
-
Select Results > Assets > IT Assets.
-
Select an Asset Group, Organization, and/or Scan.
-
Select Show.
-
Your list of assets will appear. You can select a vulnerability to view its details.
-
Select Export to generate an Excel report of these details.
Viewing OT Assets
The OT Assets list contains a list of assets focused on ports and operating systems. This list is designed to help with fixing issues per node, rather than per vulnerability. To view the OT Assets list, do the following:
-
Log in to beSECURE.
-
Select Results > Assets > OT Assets.
-
Select an Asset Group, Organization, and/or Scan.
-
Select Show.
-
Your list of assets will appear. You can select an asset to see a list of its ports that have vulnerabilities, or a port to see a list of its vulnerabilities.
-
Select Export to generate an Excel report of these details.
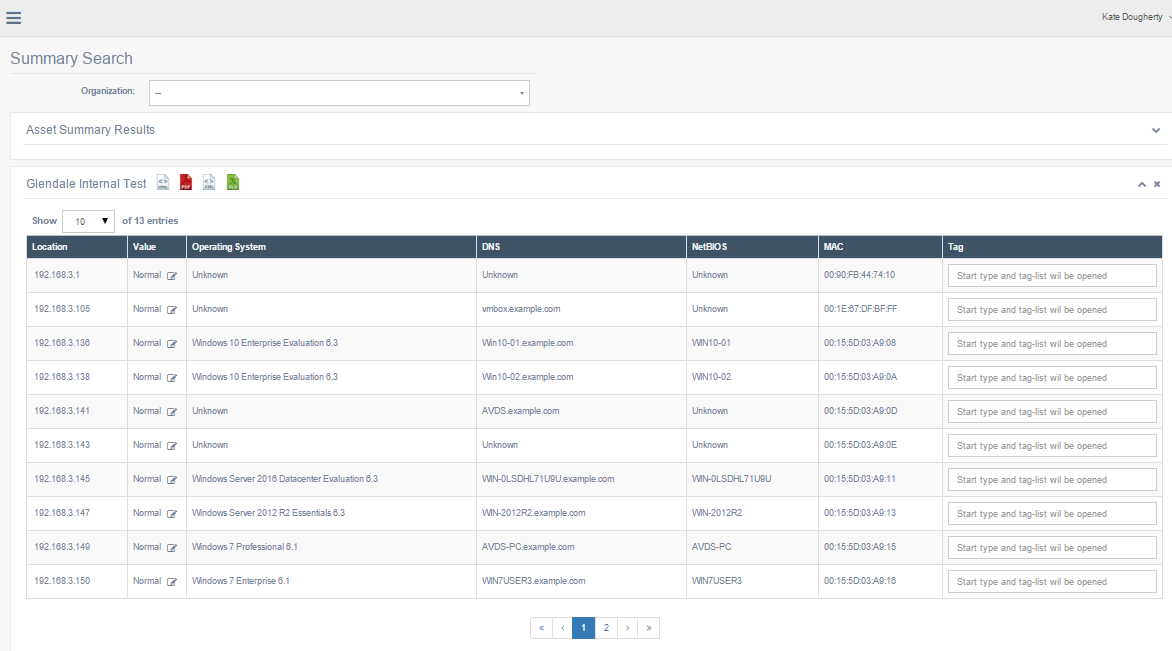
Searching for Assets
The Asset Summary Results page.
All of the assets in the image above have the default Value of Normal. They affect the Network and Organization score equally.
To change the Value for an asset in order to adjust its weight in the scoring process, click the edit icon that appears next to the Value, and then choose a new Value from the box.
The Assets Search page allows you to locate a specific asset more efficiently. To search assets:
- Click Results > Assets > Search.
-
Enter search parameters. The Assets Search page contains the following fields:
Field Description Organization The organization associated with the asset. Scan The scan associated with the asset. Note: An organization must be selected first. Hostname/IP Address The name or IP address range for the host scanned. Operating System Filters by the target’s operating system. DNS The FQDN or Internet Host name of the target. NetBIOS The NetBIOS name. MAC The hardware address of the target machine. Recursively Whether to search recursively. While a standard search occurs at the main organization level, a recursive search examines the selected organization and all of the sub-organizations under it. Hide No-Results Whether to hide targets with no vulnerabilities. -
Click the Search button.