Differential Search
Differential reports allow you to monitor changes between two scan events for an organization. This functionality allows you to track performance in terms of:
- The actions taken to address vulnerabilities
- The amount of time that elapses before vulnerabilities are addressed
Creating a differential report
To create a Differential report, do the following:
-
Log in to beSECURE with administrative privileges.
-
In the upper-left corner of the Home page, select DevOps.
-
Select Results > Differential.
-
In the Organization box, select an organization to create a report for.
-
In the Scans box, select a scan to include in the report.
-
In the Current Results From and Previous Results From boxes, select two scans to compare.
-
Select Show. If any results meet your criteria, the Vulnerability Scan Differential Results page will display the results.
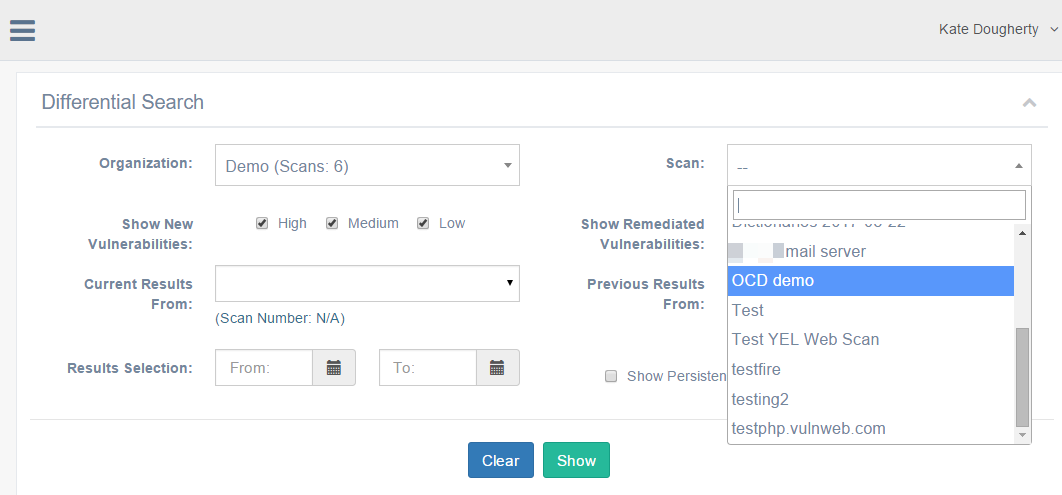
Running a differential search
- Click Results > Differential in the sidebar.
- Fill out the following search fields (from left to right):
- Choose your Organization from the drop-down list. The number of saved scans available appears in parentheses next to the Organization name. The Scan field on the right will populate with the available scans for that Organization.
- Choose a Scan from the drop-down list.
- The High, Medium, and Low boxes for the Show New Vulnerabilities field are selected by default. Disable if desired.
- The High, Medium, and Low boxes for the Show Remediated Vulnerabilities field are selected by default. Disable if desired.
- In the Current Results From box, select the date of a recently run scan.
- In the Previous Results From box, select the date of an earlier scan.
- In the Results Selection box, choose a date range to narrow the results to a shorter period between the scan dates you selected in steps e and f above.
- Check the checkbox for Show Persistent Vulnerabilities, if desired.
- Check the checkbox for Show Open Ports, if desired.
- Select Show to view the results, or Clear to start over.
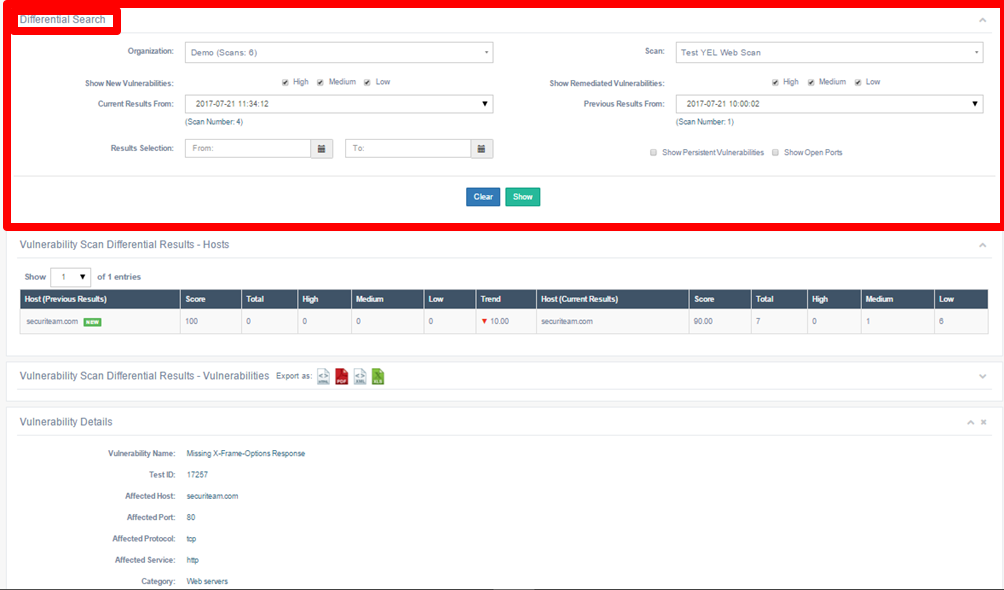
The Differential Search page.
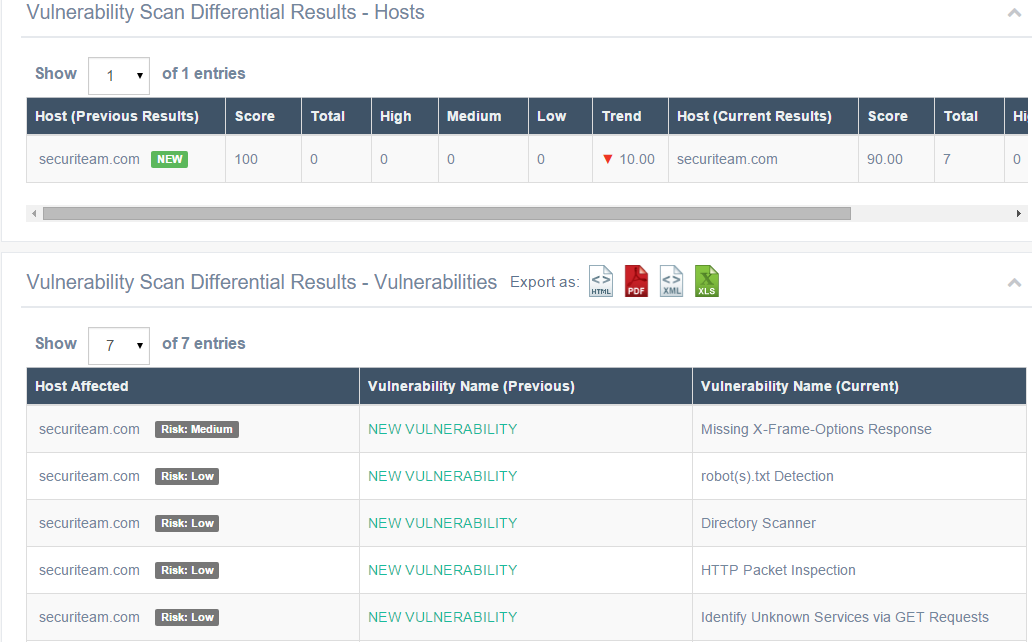
The results screen shows results by Host and results by Vulnerability.
The Differential Search results page.
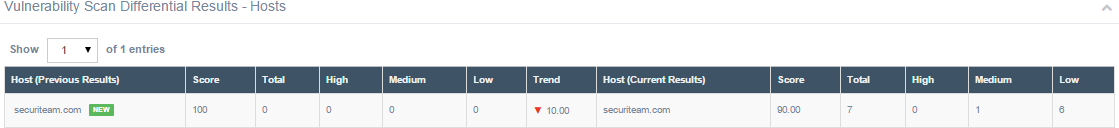
The Vulnerability Scan Differential Results – Hosts section displays the following information:
| Field | Description |
|---|---|
| Host (Previous Results) | The host scanned during the previous scan. |
| Score | The host’s overall score. |
| Total | The total number of vulnerabilities found. |
| High | The number of high-risk vulnerabilities found. |
| Medium | The number of medium-risk vulnerabilities found. |
| Low | The number of low-risk vulnerabilities found. |
| Trend | Indicates whether the target is becoming more or less secure, based on a comparison of the Scores for the current and previous scans. |
| Host (Current Results) | The host scanned during the current scan. |
| Score | The host’s overall score. |
| Total | The total number of vulnerabilities found. |
| High | The number of high-risk vulnerabilities found. |
| Medium | The number of medium-risk vulnerabilities found. |
| Low | The number of low-risk vulnerabilities found. |
In the image below, for example, secureiteam.com was the host or target in the previous and current scans. The previous results show a perfect overall score of 100, with no vulnerabilities found. In the current results, however, beSECURE found a total of seven vulnerabilities, and the host’s overall score fell to 90. The Trend column reflects this 10-point drop. For more information on how beSECURE calculates scores, see the Scoring section of this document.
The Hosts section of the Vulnerability Scan Differential Results page.
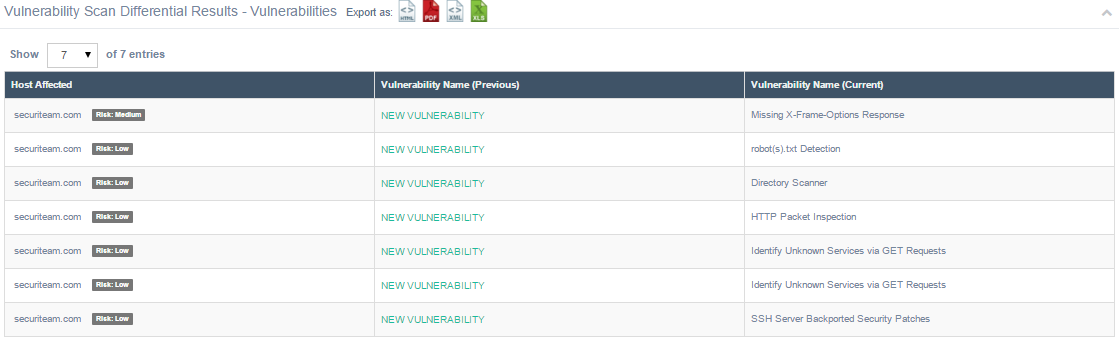
The Vulnerability Scan Differential Results – Vulnerabilities section displays the following information:
| Field | Description |
|---|---|
| Host Affected | The host scanned. A label for the vulnerability risk for the host appears next to the host name. |
| Vulnerability Name (Previous) | A descriptive name for the vulnerability found in the previous scan. The value “New Vulnerability” will appear if the vulnerability was not discovered in the previous scan. The value “Remediated” will appear if a vulnerability discovered during a previous scan does not appear in the current scan. |
| Vulnerability Name (Current) | A descriptive name for the vulnerability found in the current scan. |
To export the results in HTML, PDF, XML, or XLS format, click the icon for the format that appears above the results table.
The Vulnerabilities section of the Vulnerability Scan Differential Results page.
Click on a row to view the vulnerability details.
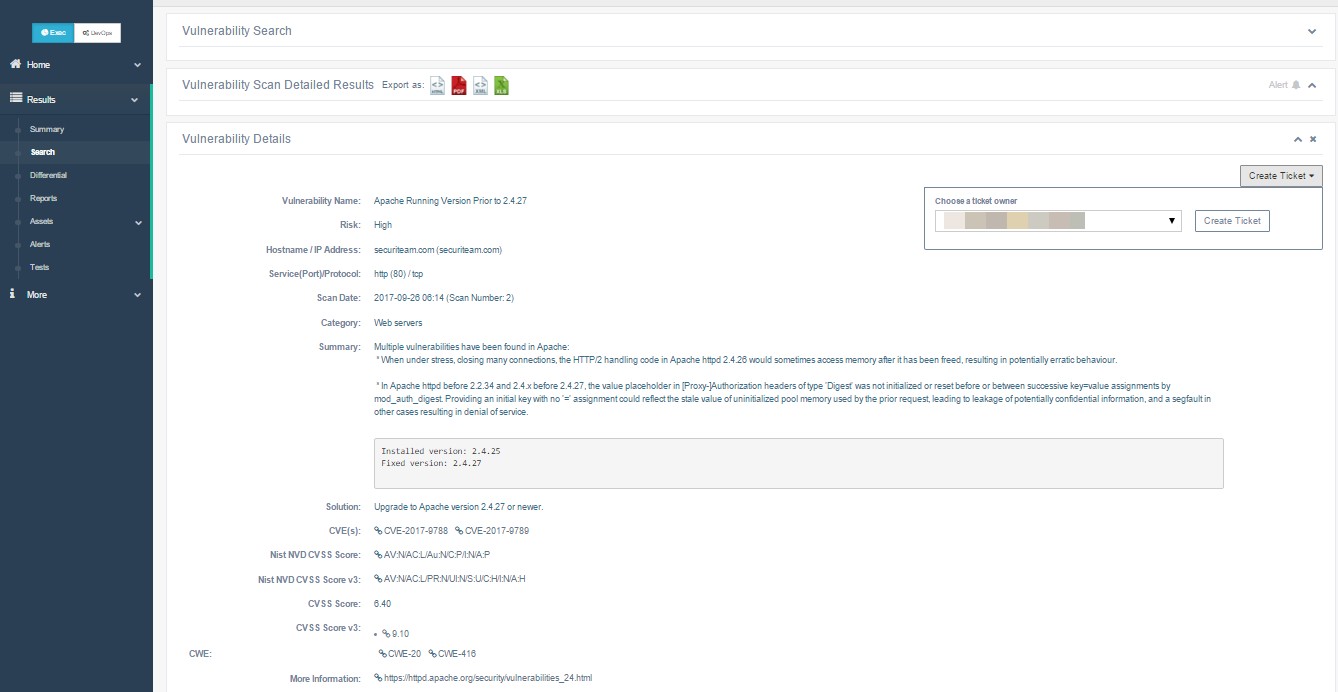
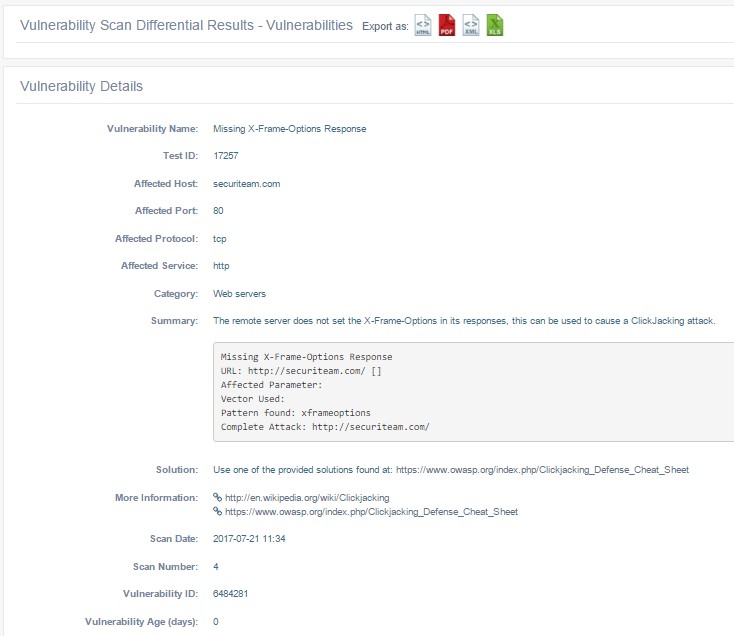
The Vulnerability Details page.
The links at the top of the page provide access other areas of the Differential Results section within the same page. For example, clicking Vulnerability Scan Differential Results – Hosts will open a panel containing the Host results. Clicking Differential Search will open another panel containing the search interface, so you can run another Differential Search within the same page.
The Vulnerability Scan Differential Results page, with the Differential Search panel expanded.
Click on a result to see the vulnerability details.
The Vulnerability Details page.
The Vulnerability Details page displays the following information:
| Field | Description |
|---|---|
| Vulnerability Name | The name of the vulnerability. |
| Test ID | The ID for the beSECURE test that detected the vulnerability during the scan. |
| Affected Host | The host scanned. |
| Affected Port | The affected port. |
| Affected Protocol | The affected protocol (for example, tcp). |
| Affected Service | The affected service (for example, http). |
| Category | The category the vulnerability falls under. |
| Summary | A descriptive summary of the vulnerability. |
| Solution | Provides suggestions for how to address the vulnerability. |
| More Information | Links to more information about the vulnerability. |
| Scan Date | The date of the scan. |
| Scan Number | The number assigned to the scan. The Scan Number for the first scan of a target will be 1, the second scan will have the Scan Number 2, and so on. |
| Vulnerability ID | The ID for the vulnerability. |
| Vulnerability Age (days) | The age of the vulnerability, as the number of days that have elapsed between the first and last time it was detected. |