beSTORM Walkthrough
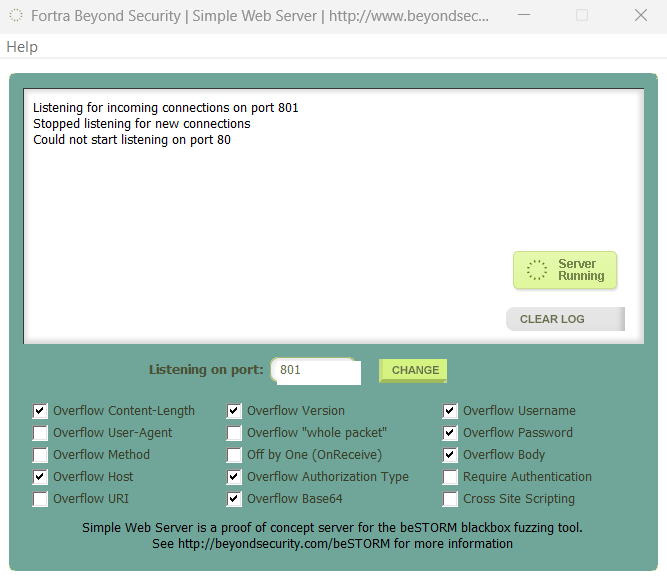
To demonstrate the initial stages of running beSTORM, the example below uses a web (HTTP) server that has been tainted with numerous vulnerabilities such as: Overflow by way of Method, Overflow by way of URI, Overflow by way of User-Agent, Off-by-One in Receive, Overflow in Base64 decoded content, and others.
To use the web server, launch the executable and the program automatically starts to listen on the desired port.
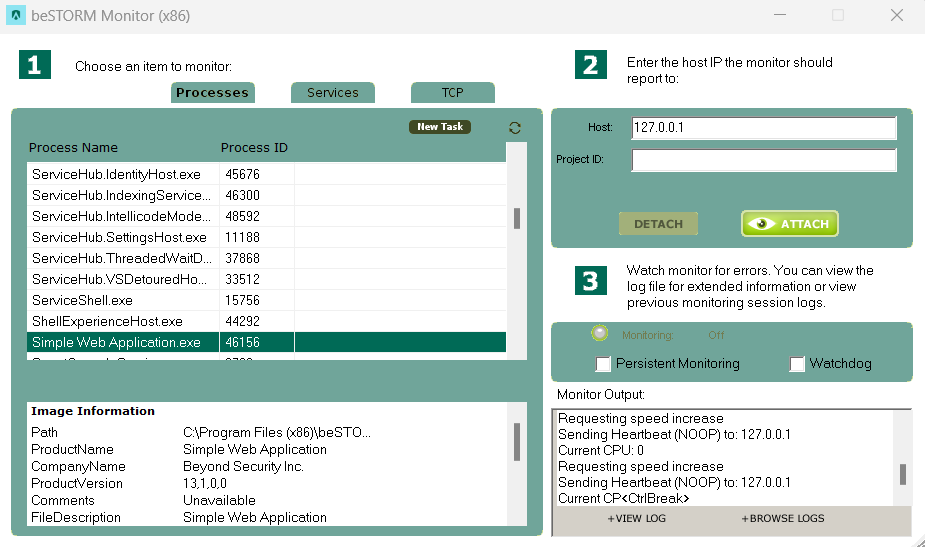
To monitor the port and its status, use the GUI version of the monitor, shown below:
The Simple Web Server process (Simple Web Server.exe) has been selected from the process list on the left side, and a host to report to on the right top side (127.0.0.1). To begin monitoring, select Attach. The Simple Web Server automatically begins answering incoming requests:
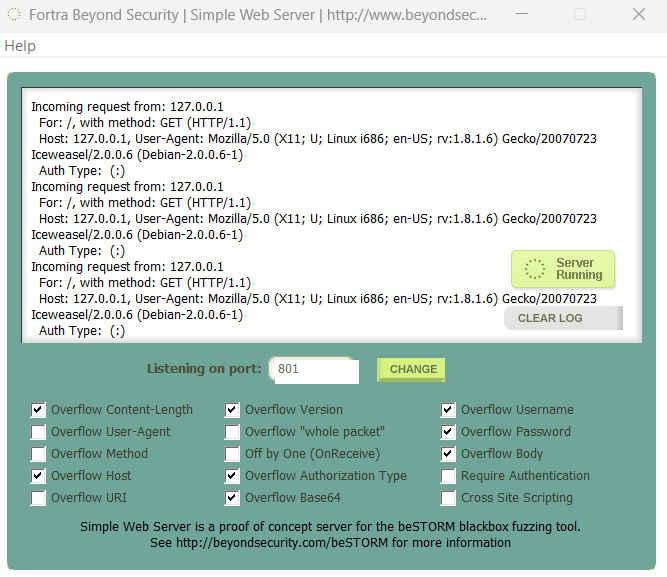
You can quickly test whether the program crashes by sending the following request:
http://AABBCCDDEEFFAABBCCDDEEFFAABBCCDDEEFFAABB:AABBCCDDEEFFAABBCCDDEEFFAABBCCDDEEFFAABB@ip_address/
If you inspect the traffic being sent using Google Chrome, you will see that this URL is sending a long Base64 authorization request:

The web server should crash, and if you inspect the log file of the monitor you should see something similar to the following:
[INFO] beSTORM Monitoring Agent version: 3.0.1
[INFO] setProgramName: C:\temp\Simple Web Server.exe
[INFO] CreateProcess was successful
[INFO] setProcessID: 1408
[INFO] OpenProcess successful
[INFO] OpenProcessToken successful
[INFO] LookupPrivilegeValue successful
[INFO] AdjustTokenPrivileges successful
[INFO] attachToProcess
[INFO] We created the process no need to re-debug it
[INFO] The process 1408 has been attached successfully
[INFO] EXCEPTION_BREAKPOINT
[INFO] Page fault on read access to 0x6846581d
[INFO] 00000580:000008f4: exception code=c0000005