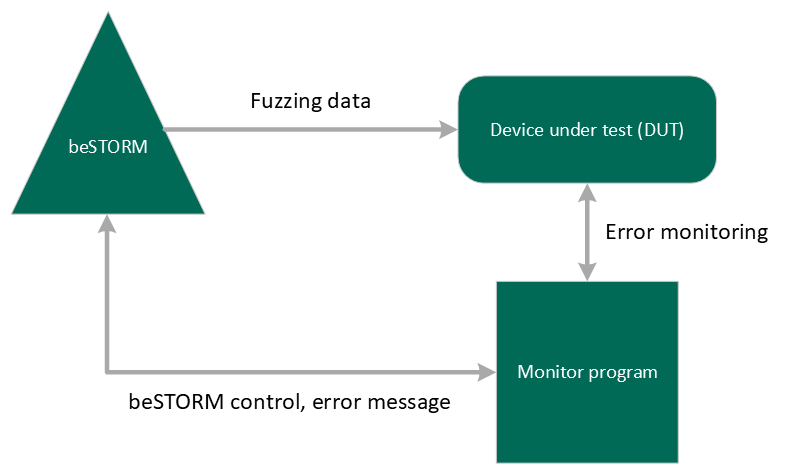
What is beSTORM?
beSTORM is an intelligent fuzzing tool that performs black box testing, which sends a large number of test cases to various devices to detect vulnerabilities in the devices. Fuzzing can be done easily by creating user-defined files not only for predefined protocols, but also for user-specific protocols and arbitrary interfaces such as APIs on platforms and driver layers. The figure below shows a general image of beSTORM usage.
Test case generation
beSTORM generates test cases according to the data structure and procedures defined in advance in XML format, which can be customized by the user. User-defined "data structures" allow for efficient and exhaustive test case generation.
Data origination algorithm
beSTORM can specify a buffer type for each data to be tested, which is defined in the XML module. beSTORM generates the data to be sent according to the buffer type.
The following is an example of a typical case of a beSTORM standard buffer type.
Repeated A
beSTORM inserts the string A into the specified region. The test data is generated while increasing the length of the string A to a predetermined number of bytes. For example, in the case of this buffer type, it attempts to raise an exception related to a buffer overflow.
(Example of data change in the data area where Repeated A is set)
A AA AAA AAA...A
Number generation
beSTORM assigns an integer in the representable range of up to 4 bytes (0 to 4294967295) for the specified region. For example, in the case of this buffer type, it attempts to raise an exception related to an integer overflow.
(Example of data change in the data area where Number Generating is set)
0 1 2 ... 4294967295
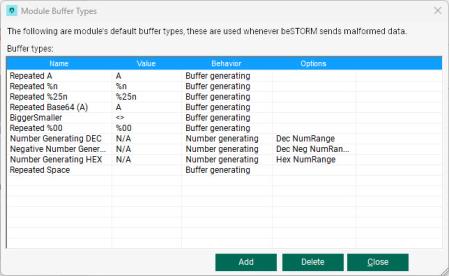
For reference, the following screen shows a list of standard buffer types.
Monitoring function
beSTORM has a monitor function to detect test cases in real-time when an exception occurs. When an error occurs, the monitor needs to send the error information to beSTORM's Exception Port (UDP Port) and beSTORM saves the received information. To use the monitoring function, it is necessary to implement a program that detects anomalies in the fuzzing target device and sends UDP to beSTORM. It is also possible to control the pause/resumption of beSTORM usage.