Your
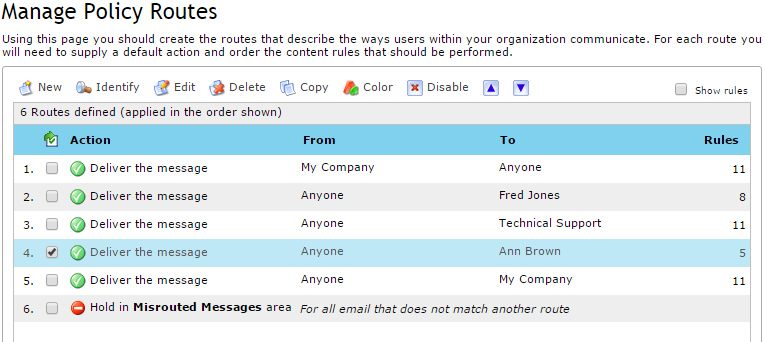
In this example, Fred Jones and Ann Brown belong to the company domain (the ‘My Company’ address list). In addition, both users are members of the address list defined as Technical Support. With this scenario, and because routes are checked from the top of the table to the bottom, the following is true:
- All outbound emails from within the company to external addresses will be subject to the assigned content rules defined in Route 1.
- Even though Fred Jones is a member of the Technical Support address list, his messages will be subject to the content rules defined in route 2 because it is higher in the table than the Technical Support Route 3, which defines a To endpoint of the Technical Support address list.
- Even though Fred Jones is a member of the My Company address list, his messages will be subject to the content rules defined in route 2 because it is higher in the table than Route 5, which defines a To endpoint of the My Company address list.
- Even though Ann Brown is explicitly set as a recipient To endpoint in route 4, messages sent to her will be subject to content rules on route 3 because she is a member of the Technical Support address list and this is higher in the table.
- Another user, John Doe, is a member of the Technical Support address list. His messages will be subject to content rules defined in route 3 because it is higher in the table than Route 5, which defines a To endpoint of the My Company address list.
- Another user, Andy Morris, is not a member of the Technical Support address list. His messages will be subject to content rules assigned to route 5 because this is the best match for his email address reading down the table.
General considerations
You should remember that when a route has been satisfied the remaining routes are ignored. For example, when considering the route list as described in the above section, email sent to Ann Brown will be subject to content rules for the route Anyone to Technical Support because she is a member of the Technical Support address list and this list is above her in the table, The route Anyone to Ann Brown will not be reached.
If you plan to develop a policy for individuals and groups within your organization, you need to ensure that the route Anyone to/from your organization contains the most stringent set of content rules. You can then create routes for individuals and groups that exempt them from certain rules, and place these routes higher in the policy table than the generic Anyone to/from the organization routes.