Parsing Validation
For Log Reader, Syslog, Syslog CEF and Windows Event Log custom datasources it is possible to validate the data parsing to ensure that you have the correct configuration. This process makes it easier to validate the data rather than relying on the specialized knowledge required for entering regular expression data.
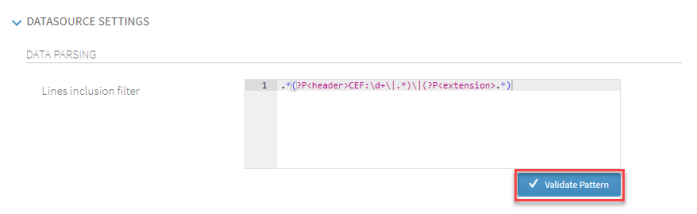
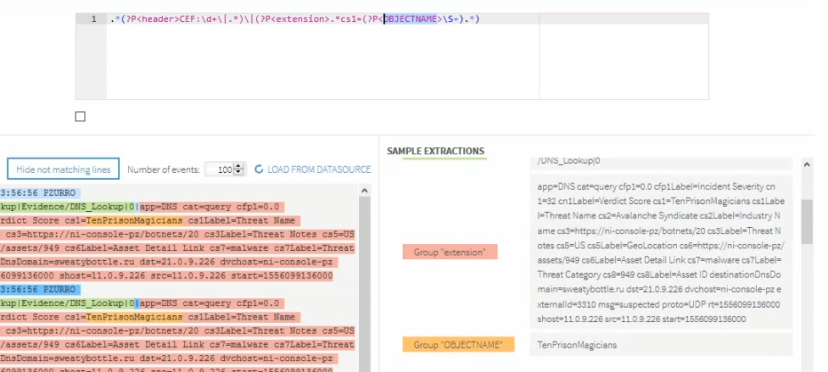
The default Data Parsing information, in this instance '.*(?<header>CEF:\d+\l.*)\|(?P<extension>.*)' is pre-entered in the Datasource Settings section. Click Validate Pattern.
Loading events directly from the Datasource (Syslog and Syslog CEF datasources only)
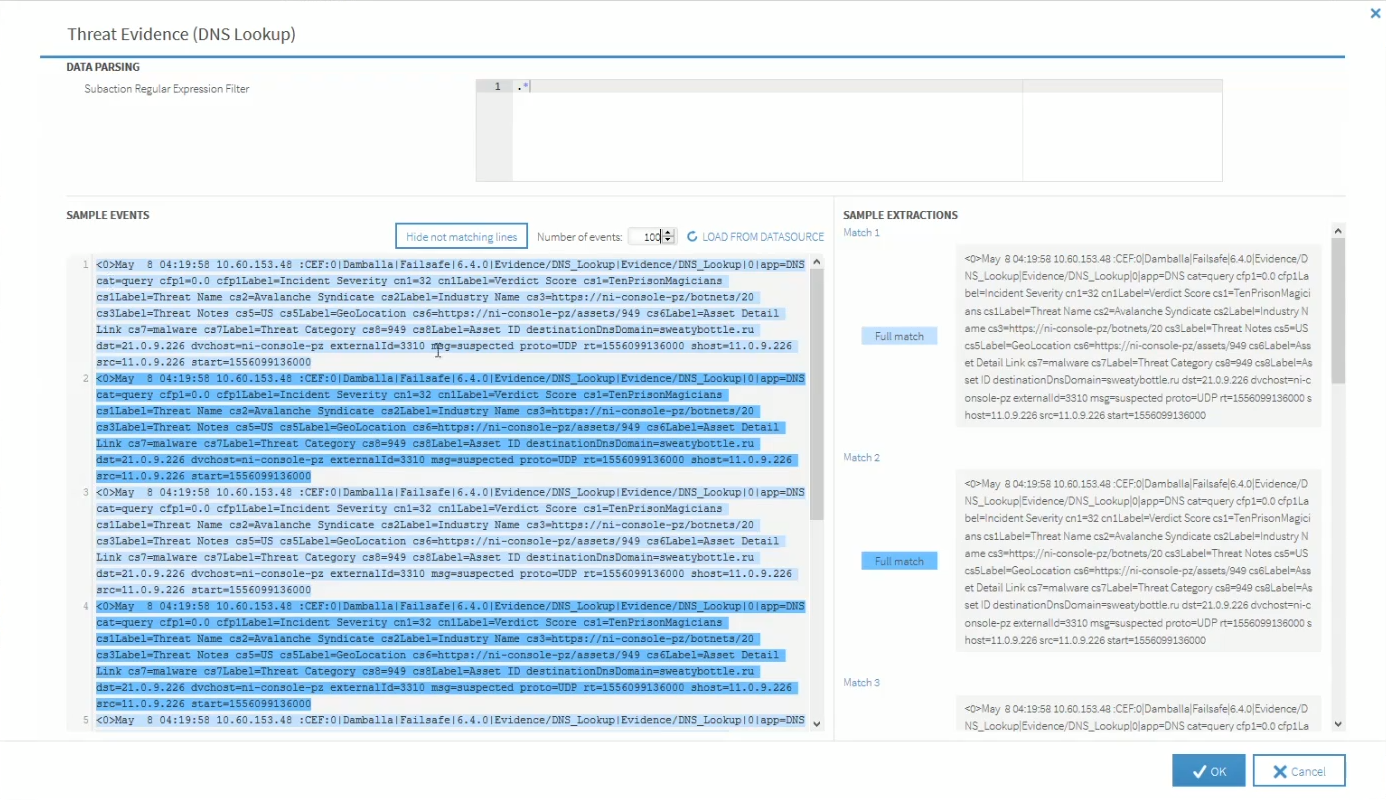
Click Load From Datasource to retrieve the events. A list of current events that match the data parsing from the selected datasource are displayed.
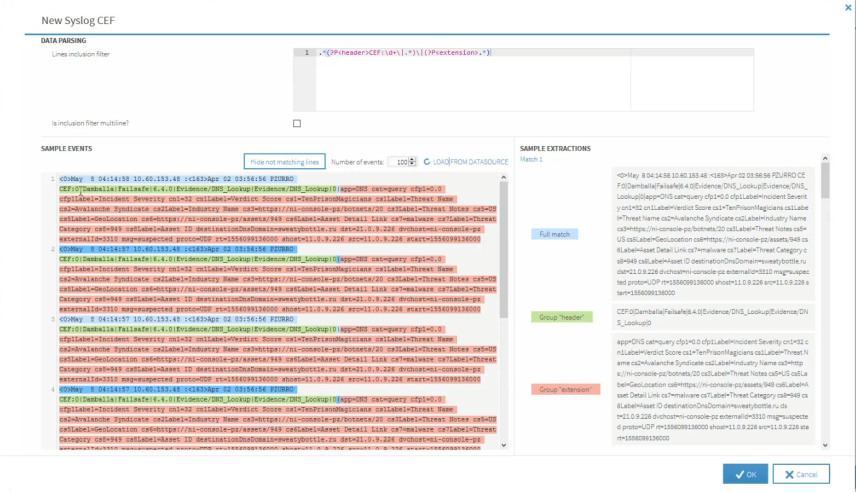
In the above example, each event is broken-down into a color co-ordinated display showing the text that fully matches the expression, the text that matches the Group 'header' and the text that matches the Group 'extension'.
This acts as a validation routine to ensure that the source is correctly configured and that the regular expressions and mappings are correctly defined.
Adding information to the Line Inclusion Filter
From the events that have been retrieved, it is possible to add further information to your line inclusion filter data parsing entry. This may 'fine-tune' the parsing entry so that less matching events are returned.
For example, if, in the retrieved data, you see an object (or any other element) that would be useful to include in the line inclusion filter, you can enter the regex detail directly from the retrieved data into the filter. It then becomes validated and appears in a new color in the sample extractions panel of the display.
For example, to include the cs1 object of 'TenPrisonMagicians' from the retrieved data into the Line Inclusion Filter, you would add the detail .cs1=(?P<OBJECTNAME>|S+).*) to the filter so that is now reads as:
'.*(?<header>CEF:\d+\l.*)\|(?P<extension>.cs1=(?P<OBJECTNAME>|S+).*)'
This returns the following display. Note the new group inclusion in the Sample Extractions panel, highlighted in Gold.
Manually adding events (Syslog, Syslog CEF, Log Reader and Windows EventLog datasources)
This is useful if you do not have access to the retrieved event directly from the datasource but know how the data is going to be formatted.
Copy and paste the example formatted event data from a third party application, for example, notepad, into the left hand data panel of the Validate Pattern display.
Data that then matches the regular expression is highlighted in the Sample Extractions panel and on the Line Inclusion Filter so you can be sure that your data parsing is correct.
Validating directly from the Retrieved Audited Actions
It is also possible to validate parsing information directly from the Retrieved Audited Actions section.
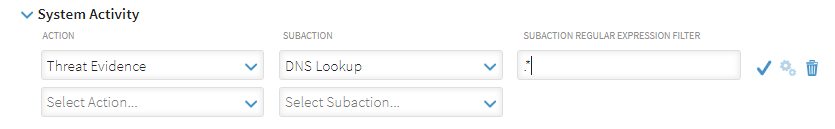
For example, using an example, of System Activity, an action of Threat Evidence, a subaction of DNS Lookup and a Subaction Regular Expression Filter as in the screen shot below:
Click the tick mark  to open the data parsing validation display for the action, subaction and subaction regular expression filter combination.
to open the data parsing validation display for the action, subaction and subaction regular expression filter combination.
You can then 'fine-tune' the result as specified in the section Adding information to the line inclusion filter.