Types of Audit Policies
Local Security Policy MMC
This interface is used to configure security settings that apply only to the local computer. It is accessed via the Administrative Tools menu in the Control Panel.
Local settings include: password policy, account lookout policy, audit policy, IPsec policy, user rights assignment as well as others. Local Security Policy is not used on domain controllers; they are governed by the Domain Controller Security Policy.
Default Domain Security Settings
This interface is used to set security policies for all computers in a domain. These settings override the Local Computer Policy settings for domain members if there is a conflict between the two. This interface is accessed via the Group Policy tab in the Properties of the domain node in Active Directory Users and Computers (administrative Tools menu).
Domain Controller Security Settings
This interface is used to configure security settings for the domain controllers in the domain. These settings take precedent over the Domain Security Policy for DCs. This interface is accessed by logging onto the domain controller as an admin user and selecting Domain Controller Security Policy from the Administrative Tools menu.
Regardless of the scope of the policy, the Audit Policy is the branch of the tree which allows the enabling of all the categories to be logged in the Event Log.
For Event Manager to be fully operational, you will only need to enable certain audit policies on all DCs and on each important member server, such as a sensitive File Server.
These audit policies are:
- Audit Account Management: Success/Failure
- Audit Logon Events: Success/Failure
- Audit Policy Change: Success/Failure
- Audit System Events: Success/Failure
How to Enable Windows File System Auditing
Step 1: Enable the Audit Policy
-
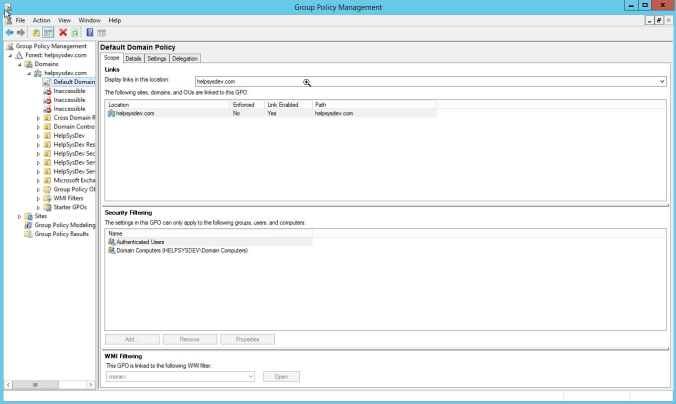
On the required Windows server, open the Domain Controller (DC) and update the Group Policy (GPO) to enable file auditing.
-
Right click on the Group Policy you want to update or create a new GPO for file auditing. In the right-click menu, select edit to go to the Group Policy Editor.
-
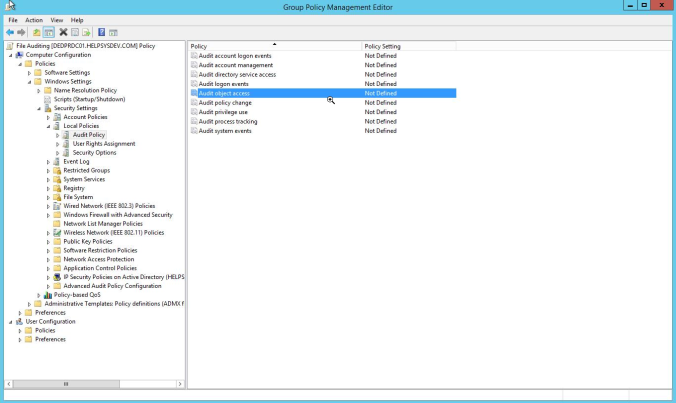
In the Group Policy editor, click through to Computer Configuration > Policies > Windows Settings > Local Policies. Click on Audit Policy.
-
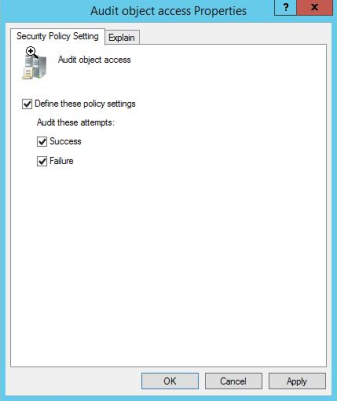
Double-click Audit object access and set it to both success and failure.
-
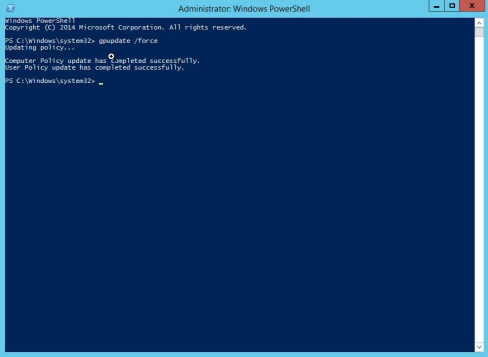
To enable your new GPO, go to a command line and run ‘gpupdate /force’.
-
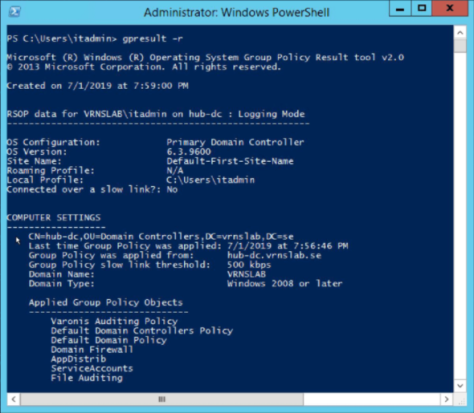
Verify that your policy is set correctly with the command ‘gpresult /r’ on the computer that you want to audit.
Step 2: Apply Audit Policy to Files and/or Folders
You now need to tell Windows exactly which files and/or folders that you want to audit. Here is the procedure to set auditing up for your folders.
-
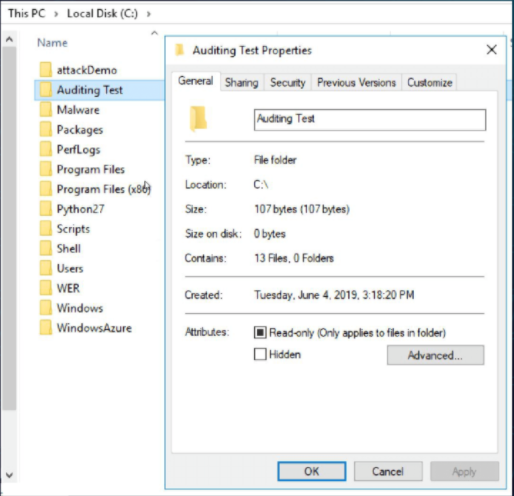
Right-click the file or folder in Windows Explorer. Select Properties.
-
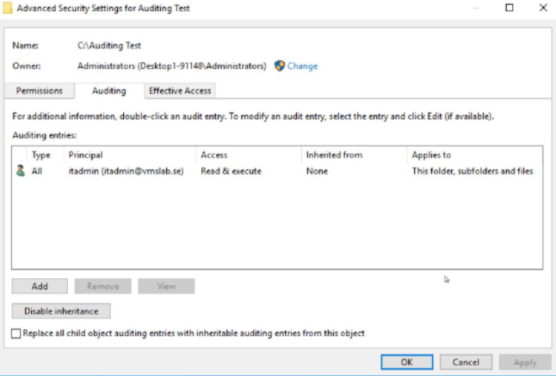
Change to the Security tab and click Advanced.
-
Click the Auditing tab and then Continue.
-
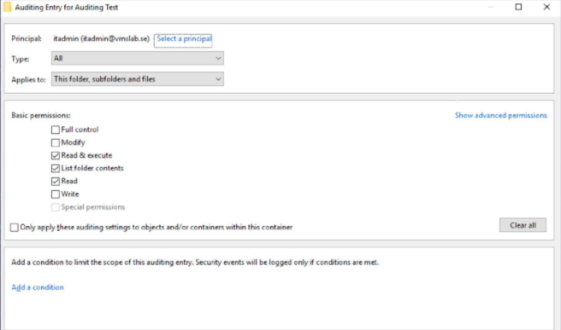
Add the Users or Groups that you want to audit and check all of the appropriate boxes.
Step 3: Open Event Viewer
Once you have enabled the Auditing GPO and set the file/folder auditing, you will see audit events in the Security Event Log in Windows Event Viewer.
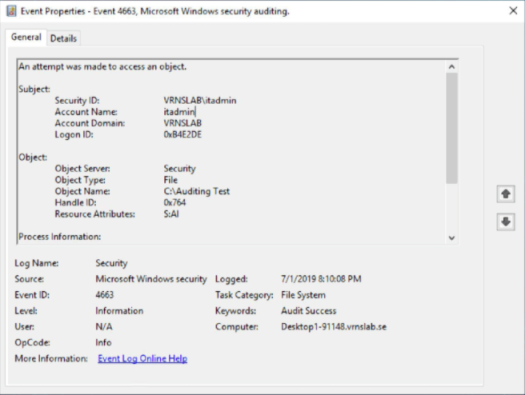
The events can now be monitored with the appropriate Event Manager Windows templates.