SOCKSProxy Client
Core Impact has added the ability to tunnel traffic through a SOCKSServer Proxy. This means that we can run Impact modules, tunneling them through any SOCKSServer configured by the customer.
The basic process involves:
- Spinning up a SOCKSProxy Server in Cobalt Strike.
- Configuring the SOCKSProxy tunnel in Core Impact for a given agent.
- Running Impact modules as if they were triggered from Cobalt Strike.
Two new modules have been created:
- Create Tunnel via SOCKS with Cobalt Strike beacon
- Create Tunnel via SOCKS with SOCKS Proxy Server
Parameters for both modules are the same:
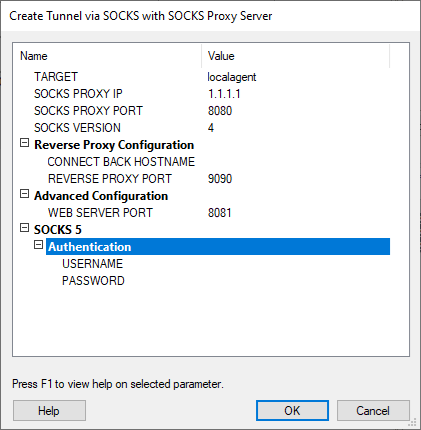
Name
TARGET - Agent on which the tunnel will be created.
SOCKS PROXY IP - IP of the SOCKSProxy server configured.
SOCKS PROXY PORT - Port where the SOCKSServer is listening.
SOCKS VERSION - SOCKS protocol version. v4 or v5.
Reverse Proxy Configuration
CONNECT BACK HOSTNAME - IP address of the last hop in the chain. Defaults to SOCKS_IP when not configured.
REVERSE PROXY PORT - TCPport that agents will use when connecting back to their host.
Advanced Configuration
WEB SERVER PORT - Some modules require an extra port to fully work ok (ie: exploits that require to connect to a WebServer to download needed files from Impact). This parameter specifies which is this port the agent will send HTTP requests to. (A tunnel should be configured in the SOCKSServer host to the Impact host for this to work).
SOCKS 5
Authentication - Only applicable in SOCKS5 that have configured authentication.
USERNAME - username to authenticate with the SOCKSServer.
PASSWORD - password to authenticate with the SOCKSServer.
After running the Module
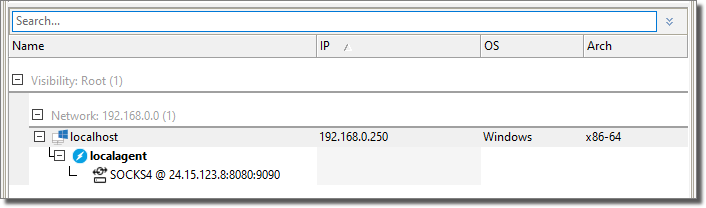
With a right-click you can Activate or Deactivate the tunnel like so:
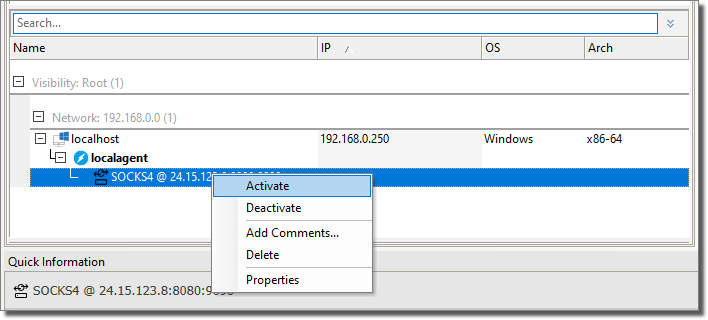
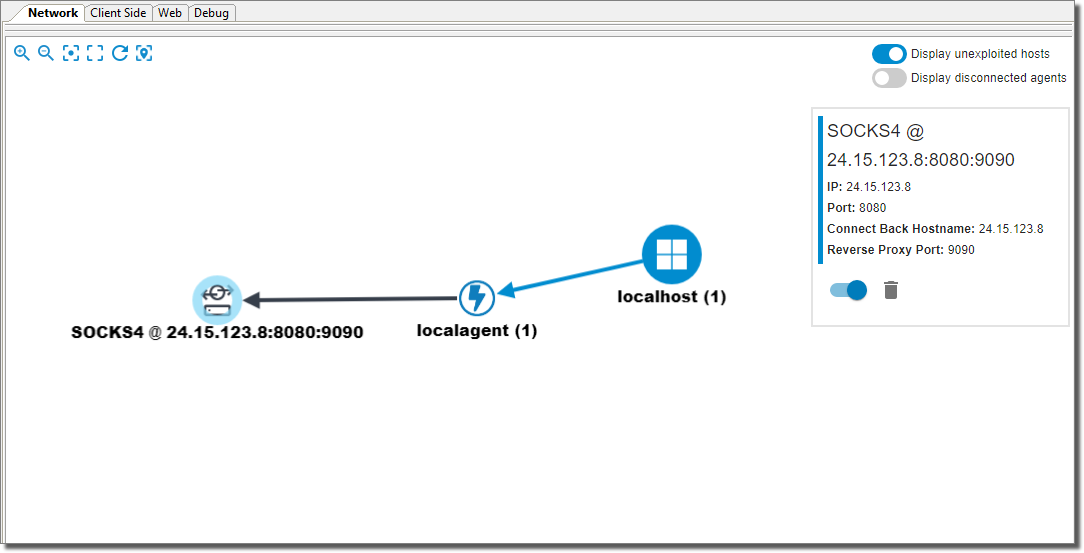
When it’s Active, it is shown bold. And traffic generated from that agent is tunneled through the SOCKSServer. This is a per-agent configuration.
Users can also interact with this new entity type from the AttackMap view.
Interoperate Between Cobalt Strike and Core Impact
Steps
- Start SOCKS from the desired CobaltStrike pwned host
- Choose desired Proxy Server Port.
- Select SOCKS Version.
- Configure Authentication or leave it NoAuth.
-
Configure Proxy Pivots of type reverse port forwarding for both Impact parameters:
- REVERSE_PROXY_PORT
- AUXILIARY_PORT
- Run Create Tunnel via SOCKS with Cobalt Strike beacon on the desired agent from Impact. Fill parameters with values configured in previous steps.
Core Impact traffic will now be tunneled through Cobalt Strike’s SOCKS.