External Network Test Routing
When testing an external network there are routing requirements to consider for delivering the exploit code and for agent communication if the systems has an exploitable vulnerability.
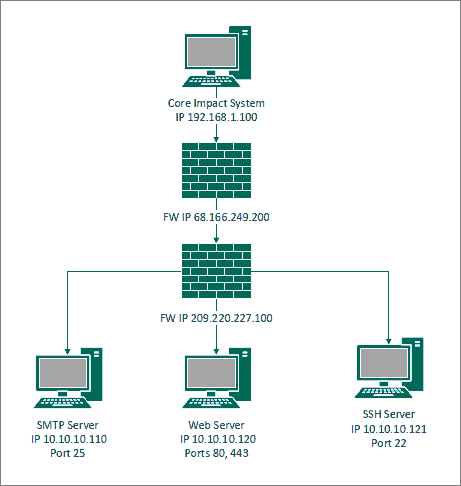
The first is the Core Impact software will be running an exploit attack on the exposed ports of a Firewall. Those exposed ports might point at one system behind the firewall or multiple systems.
The example below shows an attack against a firewall that leads to three systems behind the firewall. One is an SMTP Server on port 25, a second is a Web Server that uses both 80 and 443 and finally an SSH Server using port 22.
The Next part of the routing is the systems the exploit code is being run on must communicate back to the Core Impact system.
To do this you must configure the Network options for NAT information (Tools \ Options \ Network).
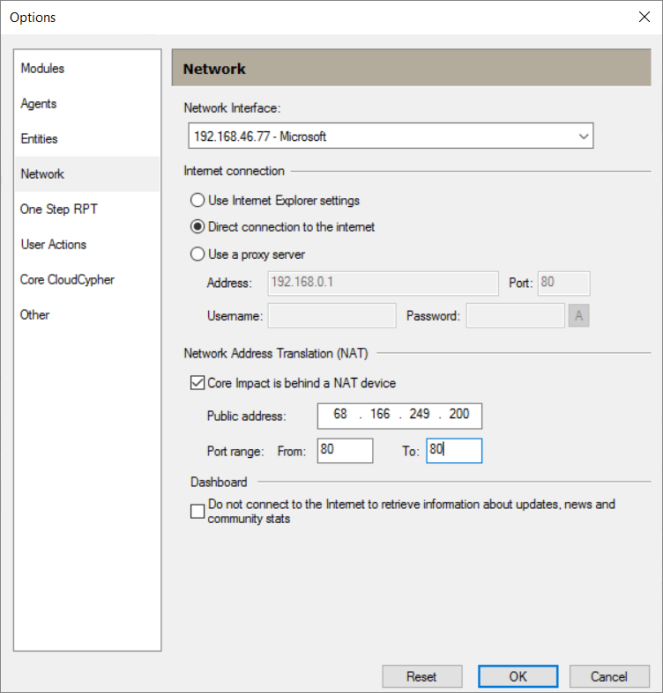
On the Network Options screen, configure the Public IP address of your firewall and a port or port range that is open on your firewall and port forwarded to the Core Impact system.
For the port we recommend choosing port 80 to 80 or 443 to 443 and choosing the “Connect From” communication method and the appropriate port. Ports 80 and 443 are generally allowed outbound from most networks so nothing would need to be configured on the remote side. Also, your firewall needs to be configured to allow ports 80 or 443 inbound to the Core Impact system.
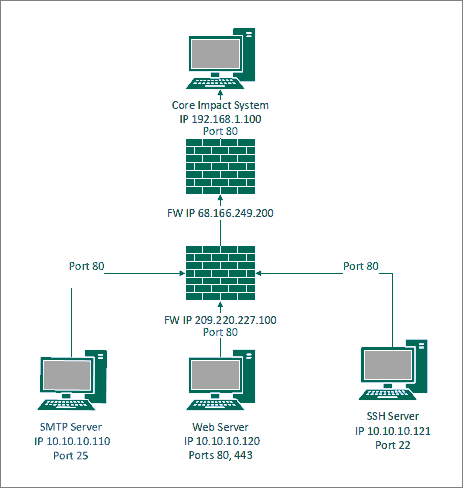
The example below shows the routing using the “Connect From” method using port 80.
Steps:
- Configure your Firewall to allow the desired inbound port to the Core Impact system.
- Configure your NAT information under Tools \ Options \ Network.
- Create a workspace.
- Run the Information gathering RPT against the External IP address(s).
- Run the Attack and Penetration RPT or individual exploits against the discovered hosts.
Additional Information
When testing against external systems that are behind a firewall you may receive false positives on the OS and Architecture of the systems that are behind the firewall. This is due to packets sometimes being rewritten by the firewall. Make sure the information discovered in the Information gathering phase is accurate. If you need to correct any information you can right click-on the system and choose Properties.