Client-side Phishing Architecture
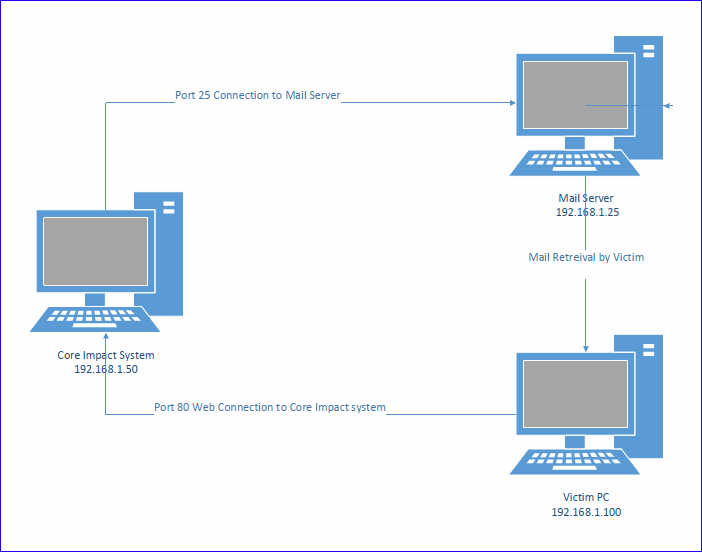
When performing Client-side testing with the Core Impact software there are two routing requirements.
- Core Impact must be able to successfully make a connection to the mail server and have the mail server accept the emails that are being sent. This usually is a port 25 connection to the mail server.
- Targeted users will be clicking on the links that were embedded in the emails. The click will attempt a port 80 web connection to the Core Impact system. Once the link has been clicked on and connects to the Core Impact system the phishing will be performed.
Internal Mail Server and Internal Targeted Users
This scenario performs a phishing campaign where both the mail server and the targeted users are internal to the network containing the Core Impact system.
Internal Mail Server and External Targeted Users
This scenario performs a phishing campaign where the mail server is internal and the targeted users are external to the network containing the Core Impact system.
In this Scenario email is sent (usually on port 25) to the mail server for the domain referenced in the “To” address.
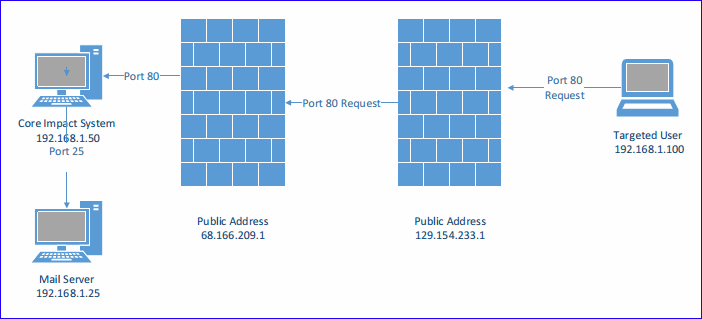
Emails are then read by the targeted users and an embedded link is clicked. For this connection to be successful two items (NAT and Firewall) need to be configured. See Configure Network Access Translation (NAT).
External Mail Server and Internal Targeted Users
In this scenario your mail server is outside your network. In this case you need to confirm that you can send the mail to the mail server on port 25 or the port the mail server is configured to use.
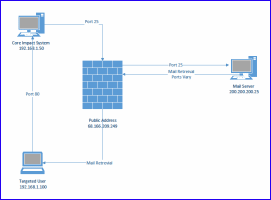
The targeted users retrieve the mail in their normal process and click on the link that is embedded in the emails which will make a port 80 connection back to the Core Impact system.
External Mail Server and External Targeted Users
This scenario performs a phishing campaign where both the mail server and the targeted users are external to the network containing the Core Impact system.
In this Scenario email is sent (usually on port 25) to the mail server for the domain referenced in the “To” address.
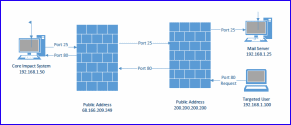
Emails are then read by the targeted users and an embedded link is clicked. For this connection to be successful two items (NAT and Firewall) need to be configured. See Configure Network Access Translation (NAT).
Symptoms
There are two possible issues here: Mail not being delivered and\or nothing happens when a link is clicked.
Mail Not Delivered
When mail is not delivered the Client-side Phishing (Web Page Redirect) or Client-side Phishing (Web Page Clone) module log may indicates the following:
Module "Client-side Phishing (Web Page Redirect)" (v203768) started execution on Tue Apr 23 11:46:25 2019
Web Browser Agent environment established Target: "Target Victim" <Victim@company.com> URL: http://192.168.1.154/rpt/983a67b986c6f530/ONLOADWINDOWUJaGC5f1hlr7gxejfBmCaQaa/list.html Trying to send mails using preferred SMTP server. Cannot login to server 192.168.1.25:25 Sending mails using preferred SMTP server failed. No attack was delivered
Troubleshooting Steps
You can use a tool like telnet to verify that you can make a connection to the mail server on port 25.
telnet smtp.company.com 25 or telnet 192.168.1.5 25
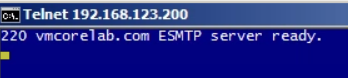
A successful connection will return a banner from the mail server. If it is not successfully you will see a message like connection refused or connection reset.
Link Fails to Connect
Clicking a link that fails to connect to the web server will usually display a page cannot be displayed message.
Troubleshooting Steps
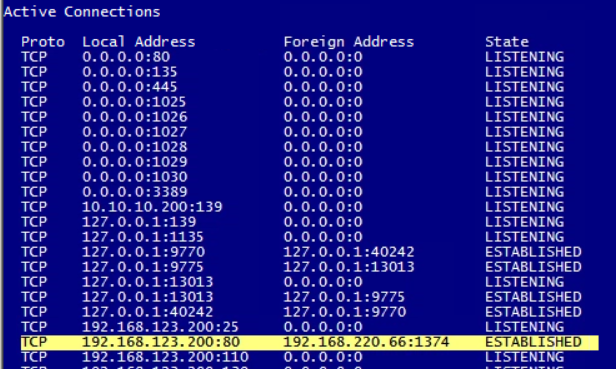
One way to see if click is making it back to the Core Impact system is to run netstat -an|more. This will display a list of the local and foreign IP addresses and ports used for each connection.
You should see the IP address of the system the clicked on the link list as a foreign address with the local system indicating that the connection was on port 80.
Additional Information
Even with internal networks there can be internal firewalls or port filtering device that segments off the different subnets. Make sure that there are no restrictions that will affect the ability of the Core Impact system to communicate successfully.
The person clicking on the link can use the site www.whatismyip.com or just google “what is my ip” and it will indicate the public IP address. If you do not see the public address the communication is not making it back to the Core Impact system.
If you are attempting to perform a phishing attack from your home, there is the possibility that your home internet service can be blocking port 25 preventing you from sending emails. The reason is most internet service providers will force you to pay for a business line and block port 25.
Configure Network Access Translation (NAT)
For connections to be successful two items need to be configured.
-
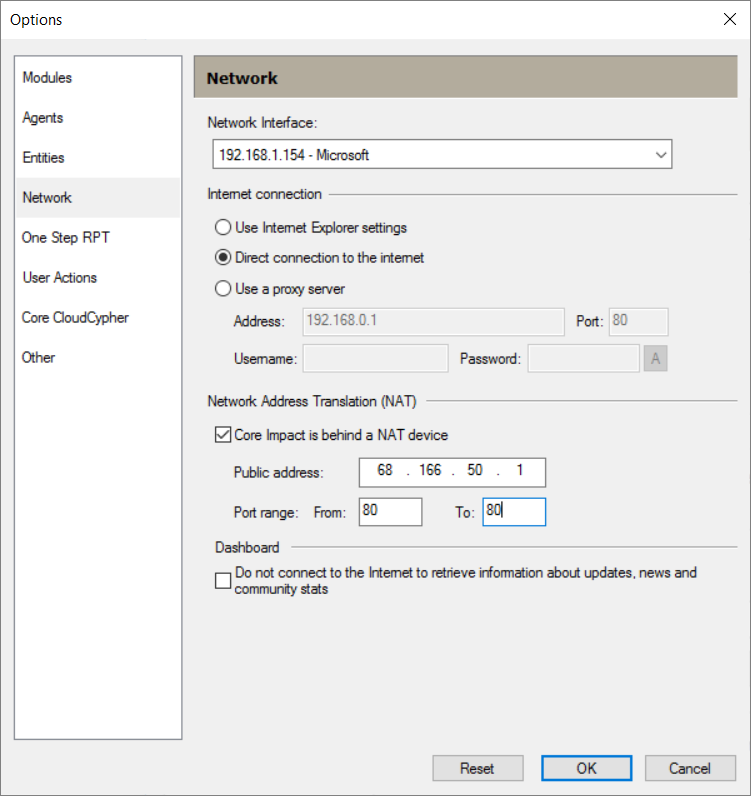
Core Impact NAT information must be configured. Select Tools->Options->Network from the main menu to open the Options screen.
On the Network tab, in the Network Address Translation (NAT) setting, specify the External Address of the firewall and the ports that will be open in this example a standard web port of 80.
-
Your firewall must be configured to allow port 80 inbound and forwarded to the Core Impact system.
If the NAT information is not filled in the links that are sent out will have the internal IP address of the Core Impact system which would never route back from an external network. With the NAT information filled in the internal IP address is replaced with the public address of the firewall allowing the successful communication to occur.