Import Data from 3rd Party Vulnerability Scanner
To run the Network Information Gathering step, follow this procedure:
- Make sure that the Network RPT is active.
- Click on Network Information Gathering to open up the Information Gathering Wizard and press Next to start.
-
In the Target Discovery Method window, select the Import data from results of 3rd party scanner option.
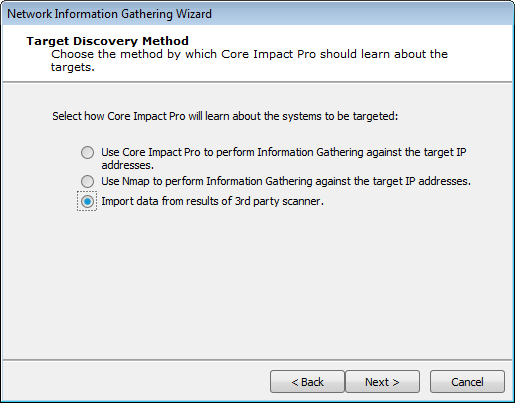
Press Next to continue.
-
Select the third-party scanner from which you have an output file: Frontline, beSECURE or Other.
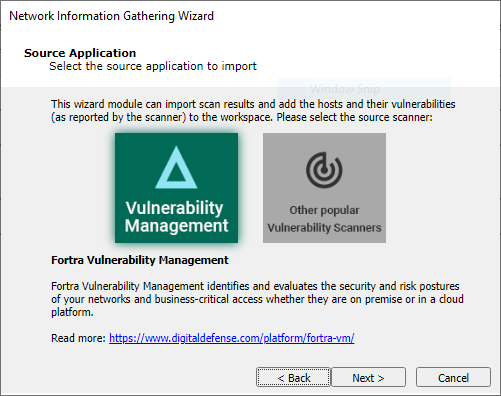
Select one of the two options shown and press Next to continue.
-
Vulnerability Management will prompt for an API Token
Visit https://digitaldefense.com/platform/frontline-vm/ for more information related to FrontlineVM.
-
Other will present the following panel:
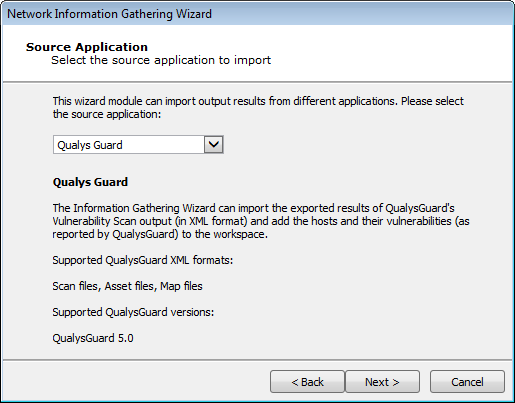
Select an item from the drop-down list, and click Next to continue.
-
-
Click the ellipsis (
 ) button and browse to and select the output file. The output format you are importing is dependent on the Vulnerability Scanner you selected in the previous step. Some scanners export their results to a file while others require you to access their data directly from the scanner's database.
) button and browse to and select the output file. The output format you are importing is dependent on the Vulnerability Scanner you selected in the previous step. Some scanners export their results to a file while others require you to access their data directly from the scanner's database.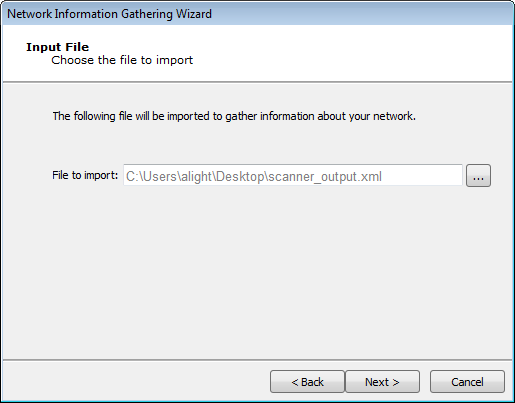
Press Next to continue.
-
The RPT will display a note about the results of external applications.
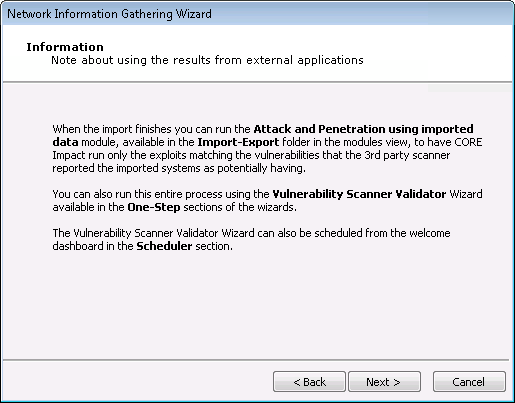
Once you've read the note and are ready to proceed, press Next to continue.
-
The RPT can check for Network Exposures in targeted hosts.
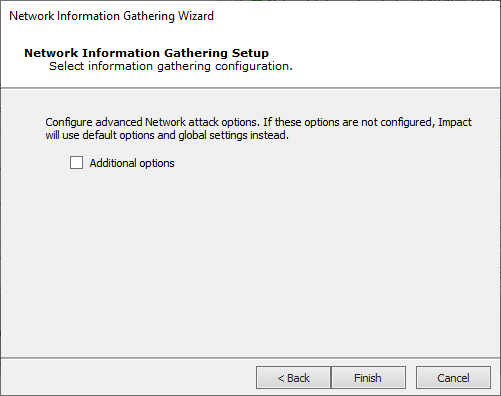
Press Finish to continue without these additional items or check the Additional Options box and press Next.
The Additional Options panel displays.
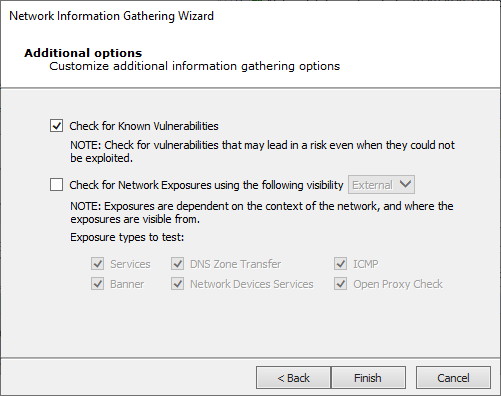
Check for Network Exposures: An information security exposure is a system configuration issue or a mistake in software that allows access to information or capabilities that can be used by a hacker as a stepping-stone into a system or network. Whereas an information security vulnerability is a mistake in software that can be directly used by a hacker to gain access to a system or network.
Press Finish and the module will run and information will be displayed on the Module Log Panel of the Console. You have now completed the first step of a Network Rapid Penetration Test.