Testing Active Directory
Active Directory (also know as AD) is a directory service that Microsoft developed for the Windows domain network. Using it you can control domain computers and services that are running on every node of your domain.
This section covers how to use Core Impact to exercise several techniques commonly used in the context of Active Directory attacks, where domain accounts are harvested and leveraged to move through the network and try to retrieve more information, and accounts with additional privileges.
Windows Domain Information Gathering
The first step is reconnaissance of the target Domain. With the domain name, and an Agent running with a domain user, it is possible to gather information that will help us in the next steps of the attack.
This scenario assumes a breach to the Active Directory client, that is, we've somehow obtained a foothold into the domain's network (for example, through a remote exploit to the client host, a client-side attack targeting the user of the client host, obtained credentials from a previously compromised host, performed a dictionary attack on weak credentials through identity verifiers, etc.).
Inspect the Domain
-
Set the OS agent of the logged on user as source by right-clicking on the agent and selecting Set as source.
-
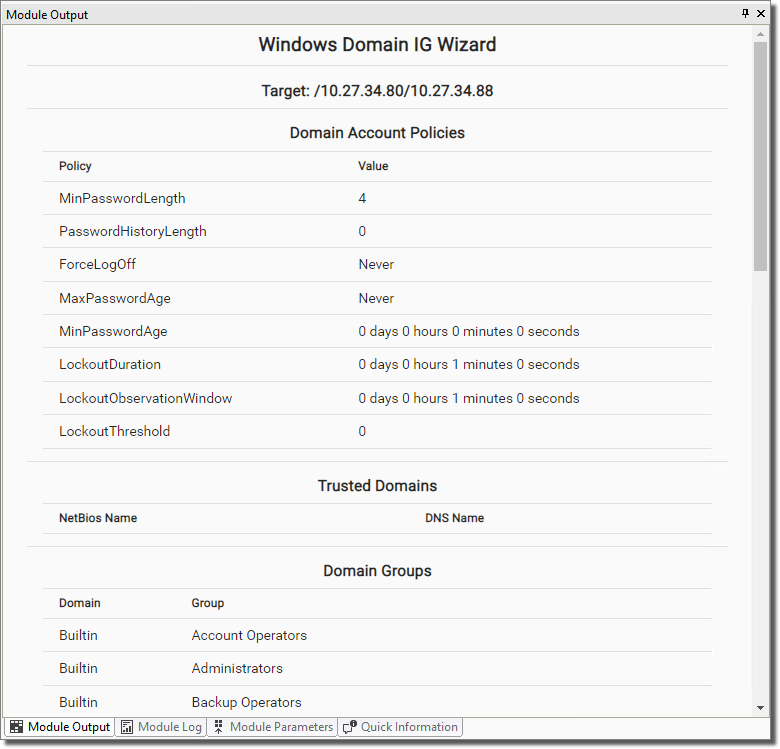
In the Modules view, go to the Information Gathering category and launch the module Windows Domain IG Wizard .
-
Click Next.
-
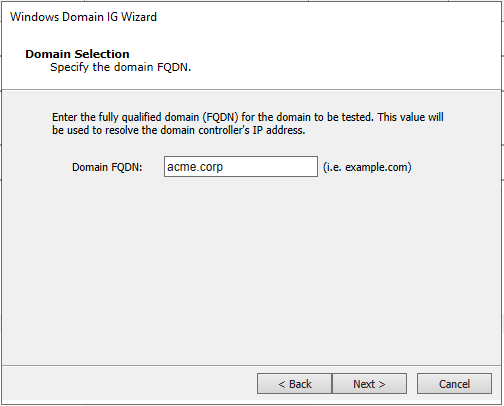
Enter the domain name (in this example, acme.corp) and click Next.
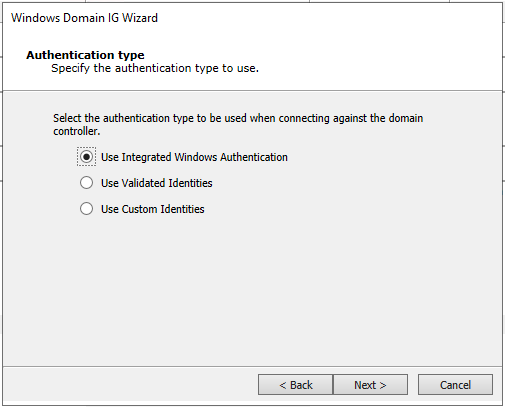
Use Integrated Windows Authentication will leverage the credentials of the logged on user (associated to the process where the OS Agent is running).
-
Click Next.
-
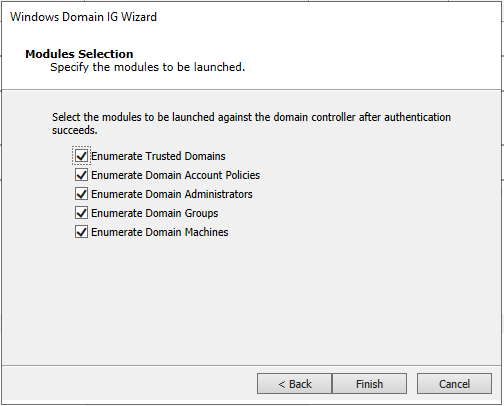
Click Finish.
The module will spawn several submodules to perform the tasks listed above. See results in the output/log of each submodule.
Kerberoasting Attack
-
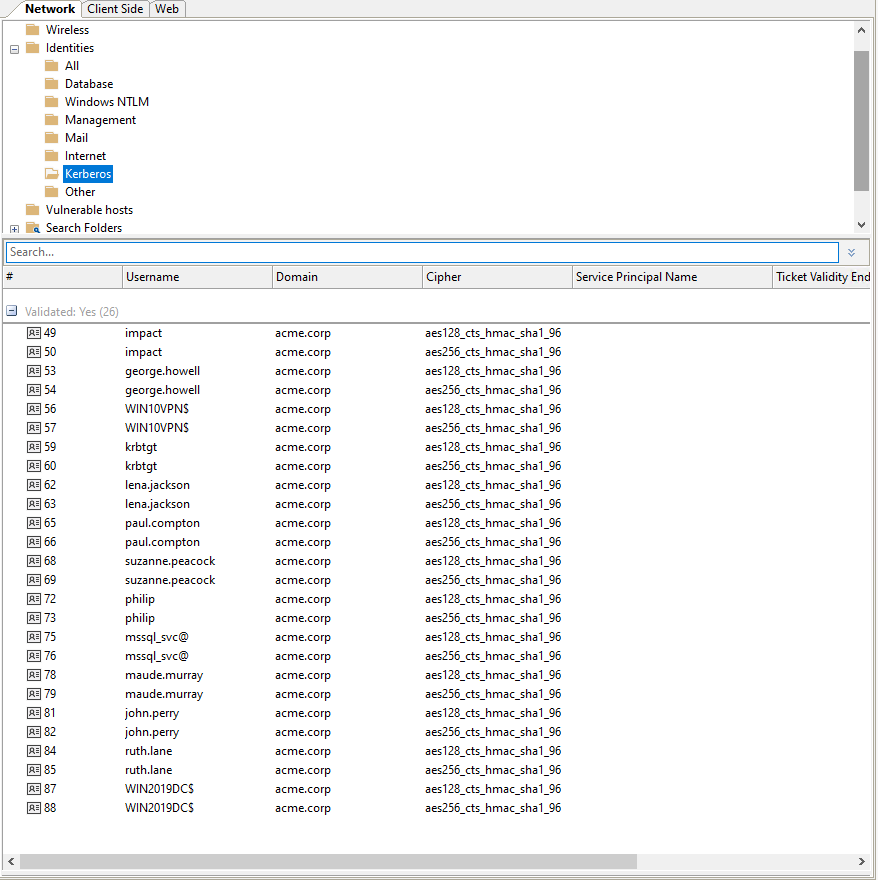
With the previously harvested domain identity, we can also try to find domain services that are using user accounts, which may be prone to a Kerberoast attack, where a potentially weak user account's password could be cracked.
-
Launch the Windows Domaing IG Wizard again.

-
Click Next.

-
Enter the domain name and click Next.
-
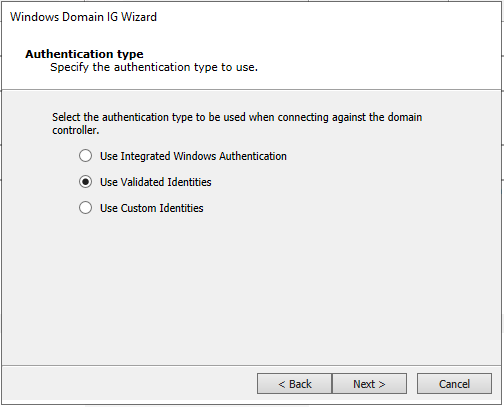
Select Use Validated Identities and click Next.
-
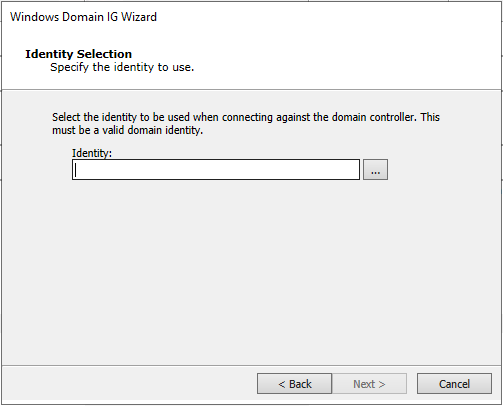
Select the ellipsis button (…) to select the previously obtained identity.
-
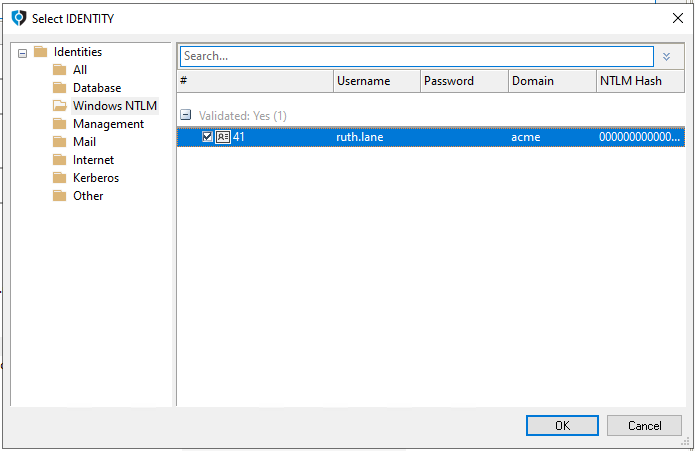
Go to the Identities - Windows NTLM group, select the identity for the domain user, and click OK.
-
Click Next.
-
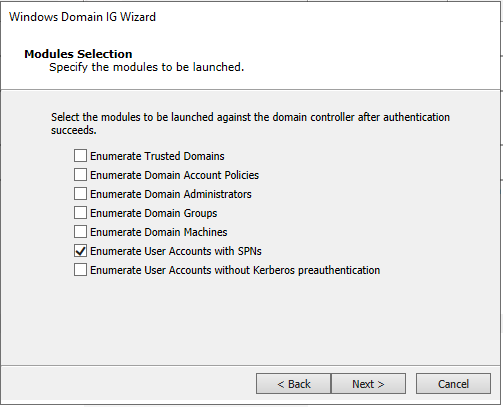
Uncheck all options and leave that of Enumerate User Accounts with SPNs and click Next.
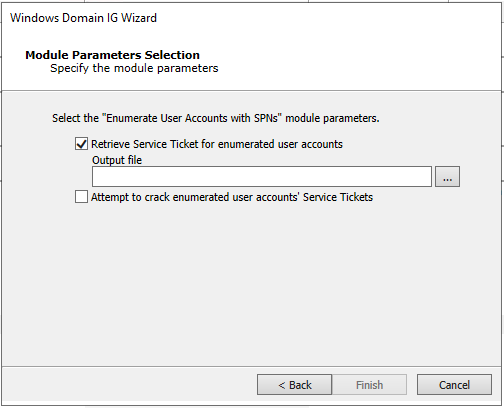
-
Click the ellipsis button (…) to provide the name of the file to output any retrieved ticket.
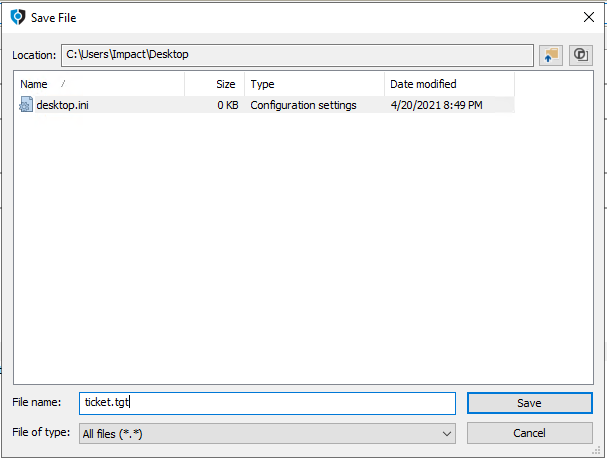
-
Enter the name of file name to extract ticket info (for example, ticket.tgt) and click Save.
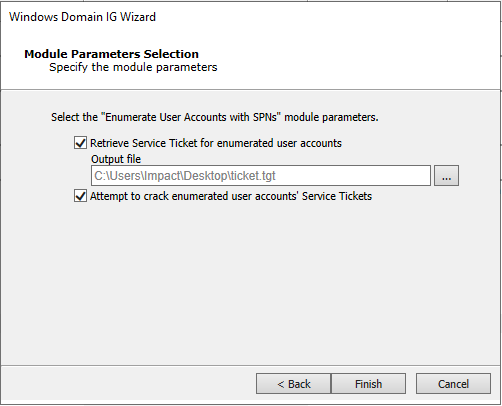
-
Check the option to try to crack any retrieved ticket and click Finish.
-
The module Enumerate User Accounts with SPNs will find a user account with a SPN.
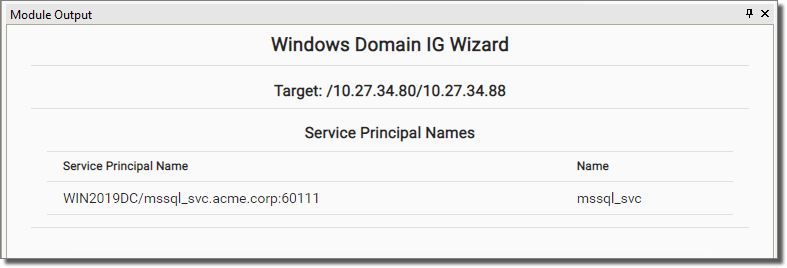
-
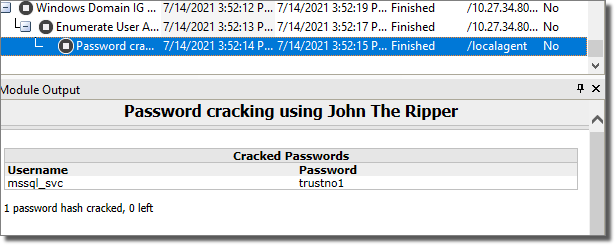
Then, the module Password cracking using John The Ripper will be launched to try to crack the password. If enabled, the password hash will also be sent to the Cloudcypher Online password decrypter service (see Using the Core CloudCypher Service) for cracking (Depending on the password length and complexity this may take a long time, so this step is optional and can be launched manually at a later stage, referencing the retrieved ticket (.tgt) file).
-
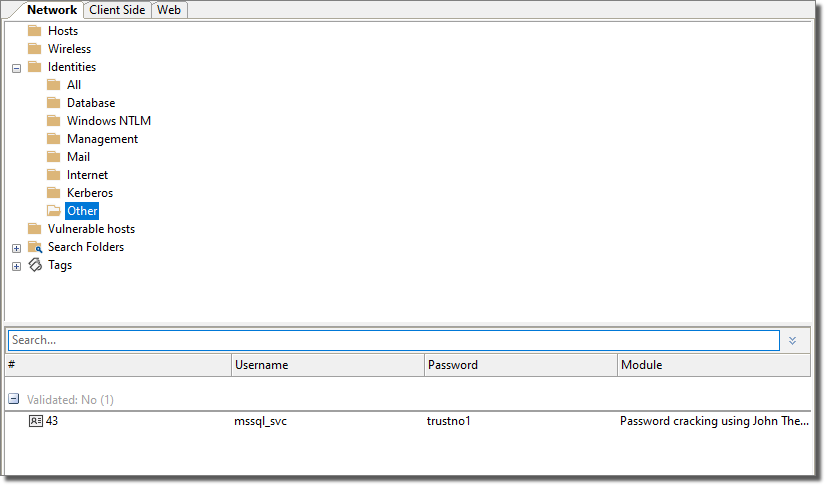
The cracked user/pwd is stored as a new identity in the Identities - Others group.
The credential obtained through the Kerberoast attack is going to be leveraged later, in the Compromising Active Directory Domain Controller section.
AS-REPRoasting Attacks
-
Similarly, you can also use the Windows Domain IG Wizard to enumerate users configured without Kerberos pre-authentication, to try and perform an AS-REPRoasting attack.
-
Launch the Windows Domain IG Wizard again.

-
Click Next.

-
Enter the domain name and click Next.

-
Select Use Validated Identities and click Next.

-
Select the ellipsis button (…) to select the previously obtained identity.

-
Go to the Identities - Windows NTLM group, select the identity for the domain user and click OK.
-
Click Next.
-
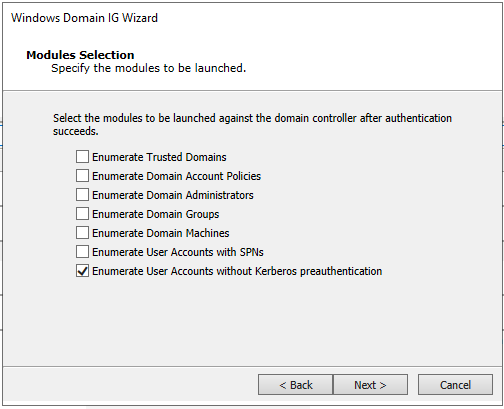
Uncheck all options and leave that of Enumerate User Accounts without Kerberos preauthentication and click Next (Notice that enumeration of user accounts with SPNs and user accounts without Kerberos preauthentication could have been launched at the same time, though we've launched individually to show the associated attack separately).
-
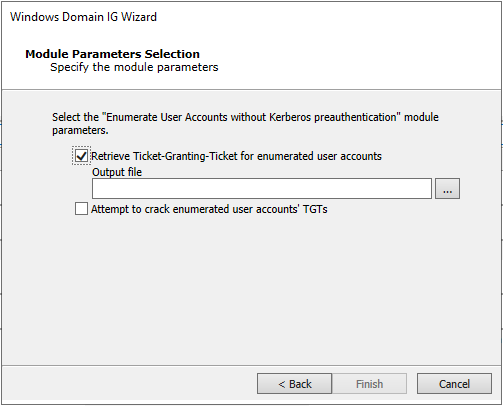
Click the ellipsis button (…) to provide the name of the file to output any retrieved ticket.
-
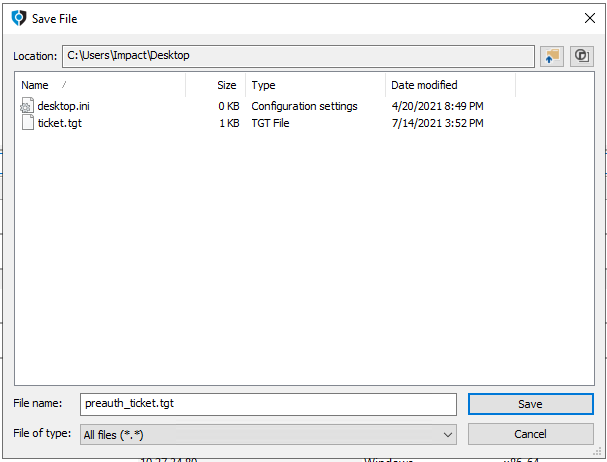
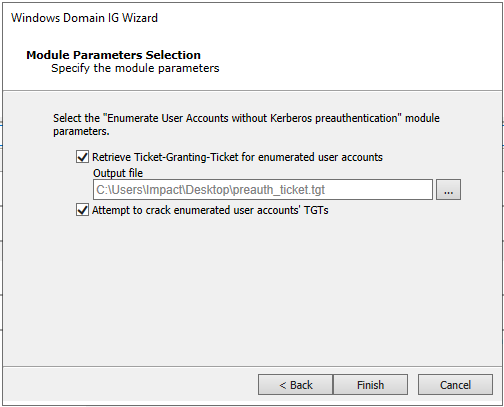
Enter the name of file name to extract ticket info (for example, preauth_ticket.tgt) and click Save.
-
Check the option to try to crack any retrieved ticket and click Finish.
-
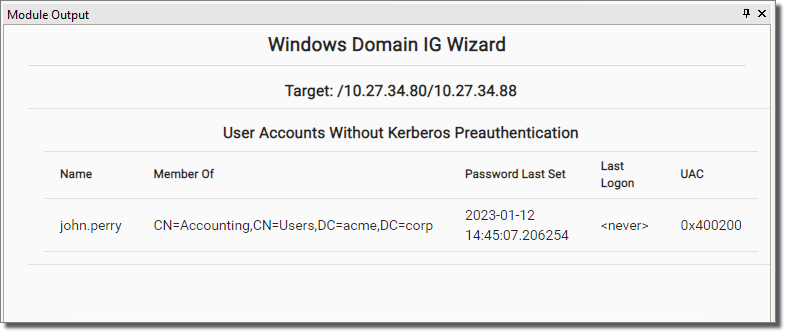
The module Enumerate User Accounts without Kerberos preauthentication will find a user account without Kerberos preauthentication.
-
Then, the module Password cracking using John The Ripper will be launched to try to crack the password. If enabled, the password hash will also be sent to the Cloudcypher Online password decrypter service (see Using the Core CloudCypher Service) for cracking (Depending on the password length and complexity this may take a long time, so this step is optional and can be launched manually at a later stage, referencing the retrieved ticket (.tgt) file).
Compromising Active Directory Domain Controller
The service user account that we previously cracked through the Kerberoast attack, may be configured with additional privileges required by the associated application. In this reduced example environment, the account is configured with local admin privileges in the Active Directory server host. We can thus try to leverage the cracked user and password to deploy an OS Agent in that host.
-
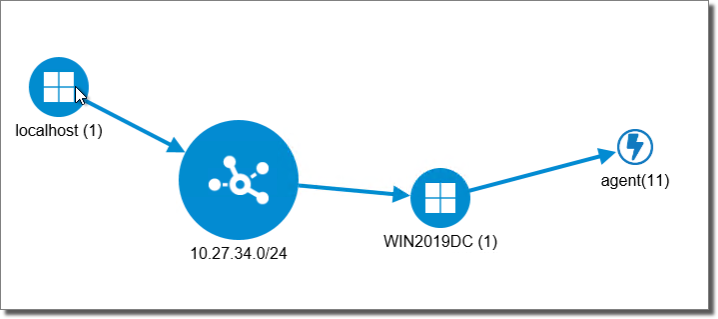
In the Network view, open the localhost entity, right-click on localagent and set it as source, for the next steps to be executed from the local machine where Core Impact is running.
-
Execute Network Information Gathering RPT on the AD Domain controller host.
-
In the Modules view, look for the module: Install Agent using WMI on the 10-Post Exploitation > Agents folder, and drag & drop it on the discovered AD DC host entity.
-
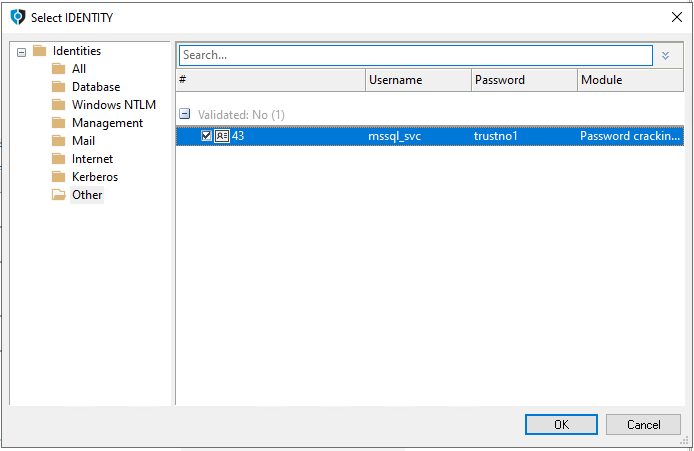
Select the IDENTITY parameter and then click on the ellipsis button (...) to select the identity of the previously retrieved service account and click OK.
-
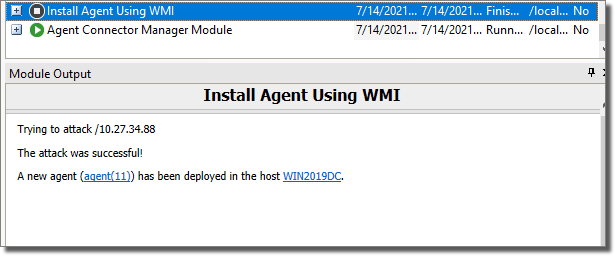
Click OK to launch the module.
-
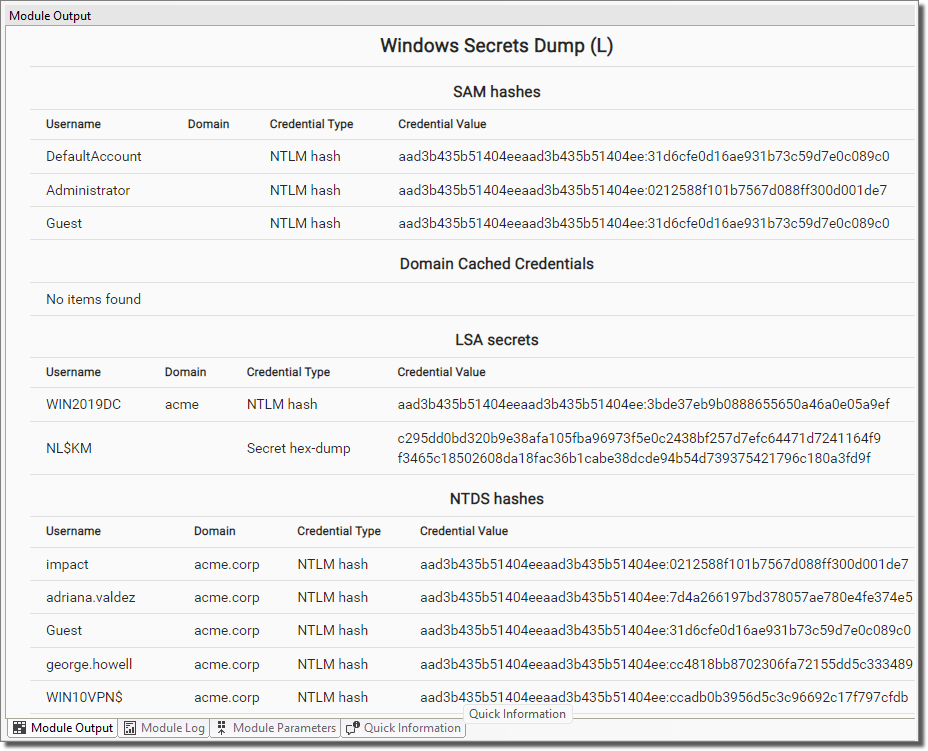
In the Modules view, look for the module Windows Secrets Dump (L) and drag-and drop it on the newly deployed OS Agent on the ADDC host. This module will retrieve and commit identities for all domain users, so make sure to consider whether to use the COMMIT IDENTITIES parameter in a large Active Directory environment.
Kerberos Golden Tickets
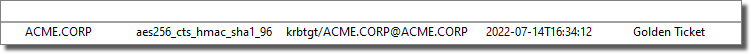
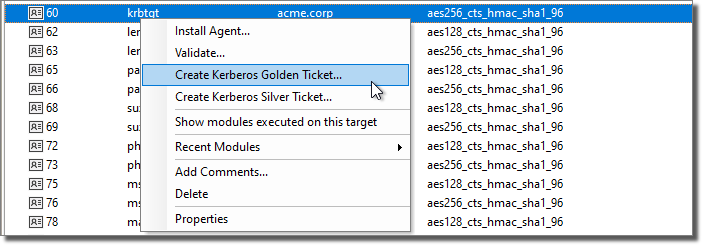
Among the retrieved identities found in the ADDC host, it's krbtgt, which is the Active Directory Key Distribution Service Account, and which can be used to forge valid Kerberos Ticket Granting Tickets (TGTs).
-
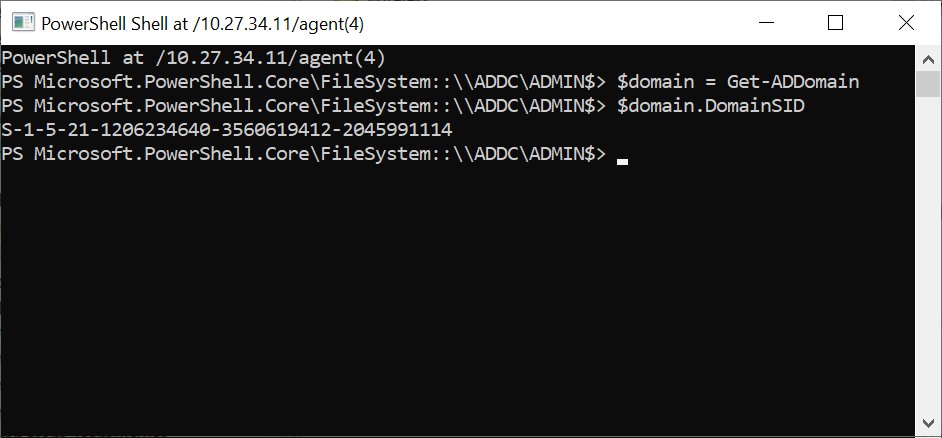
In order to create a Kerberos Golden Ticket we need the domain's SID, which is a required parameter for the module. We can obtain value through a PowerShell Shell on the OS Agent on the ADDC host, by executing:
- $domain = Get-ADDomain
- $domain.DomainSID
- Copy
-
We can now right-click on the krbtgt identity and use it to create a Kerberos Golden Ticket to impersonate another domain account.
-
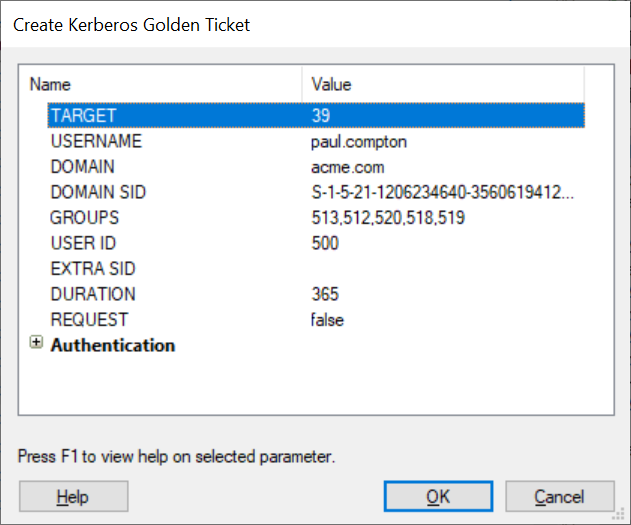
Complete the following module parameters:
USERNAME: paul.compton
DOMAIN: acme.corp
DOMAIN SID (complete with the value obtained above)
-
Click OK.
The module will have created a new golden ticket identity entity for the domain user paul.compton.