Running Cross Site Request Forgery (CSRF)
If a web application contains a form in which Cross Site Request Forgery (CSRF), this does not necessarily mean there is a security risk. For example, if a form does not have the capability to make any database changes or return database content, CSRF cannot be used to do any harm. For this reason, Core Impact requires that tests for CSRF risks be interactive - Core Impact will identify where CSRF is possible and you will determine whether these instances are security risks.
Use the following steps to run a Cross Site Request Forgery test:
-
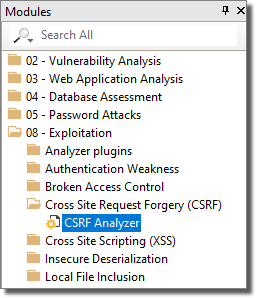
Click the Web entity tab, then click the Modules tab to view the Modules list.
-
Locate and double-click the module named CSRF Analyzer.
- Select the TARGET page(s) that you want to test for CSRF vulnerabilities. Then click OK.
- Navigate to the Executed Modules pane and select the line item that corresponds with the CSRF Module.
-
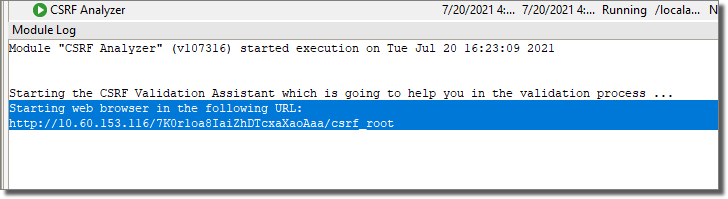
In the Module Log pane, look for a log entry that reads "Please open the following URL in your web browser" and a URL immediately following.Core Impact will automatically attempt to open this URL in your default web browser.
-
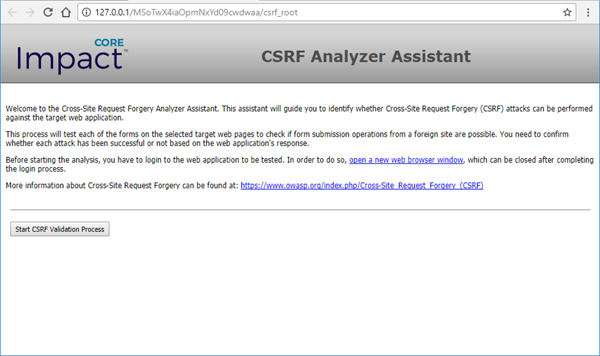
Core Impact presents you with a web page - the CSRF Validation Assistant - that steps you through the form data as identified in the target page(s).
CSRF Analyzer Module
-
Click the Start CSRF Validation Process button.
-
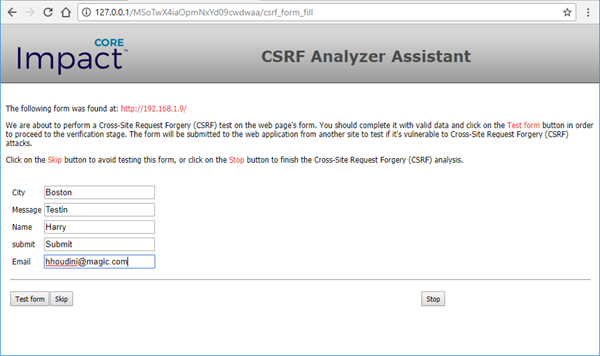
Core Impact displays the first form that it identified from the target page(s). Enter data into the field(s) and click the Test Form button to test the form. If you know that the form is not a security risk or do not want to test the form, click the Skip button to move to the next form.
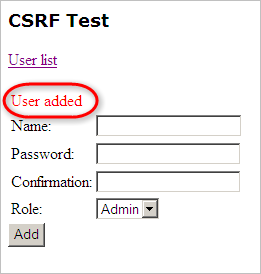
In the below screenshot, the form appears to be creating a new user in a web application, so you would want to enter valid information to see if you are able to successfully create a user.
-
The next form will display the results of the action. You must then determine whether the form presents a security risk. If it does, click the Attack worked button. If not, click the Attack didn't work button.
In the below example, the target page returned the confirmation "User added", indicating that we were successful in creating a new user in the system using CSRF. Because this is a security risk, we would click the Attack worked button.
- If you click Attack worked for any of your web pages, those pages will be visible in the CSRF folder of the Web entity view.