Cyber adAPT
Cyber adAPT secures every segment of the digital enterprise, finding more attacks more quickly than alternative approaches. Cyber adAPT’s patented threat detection platform monitors 100% of network traffic, no matter the source, and in real-time.
Integration Details
The Fortra VM integration connector will call Cyber adAPT’s skwiid API to query for threat events / alerts which have occurred within a specific window (30 days). These alerts will be put into a Threat List. The Fortra VM connector will then call Fortra VM APIs to pull any assets previously tagged as threats found by Cyber adAPT (these assets will have a label “Cyber adAPT Alarm”).
The Fortra VM connector will correlate the Cyber adAPT threats in the Threat List and the previously tagged assets from Fortra VM to remove the “Cyber adAPT Alarm” label for any assets not found in the newly created Threat List (keeping the assets tagged within Fortra VM up to date).
After removing Cyber adAPT alarm tags from assets not found to have threats within the 30 day window, the integration connector will then tag any new assets found in the Threat List.
To integrate with Cyber adAPT, perform the following (see below for detailed instructions):
- Generate a Fortra VM API Key
- Install script files (Click to Download).
- Set up
Generate a Fortra VM API Key
-
Log in to Fortra VM.
-
In the site heater, select your name and choose My profile.
-
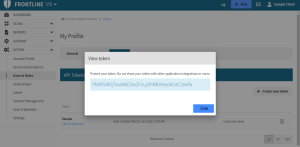
On the API Tokens tab, select Create new token.
-
In the Add New Token dialog, type the token name and select OK.
-
Below your token name, selecting Click to show key displays your API Key.
Installation
To install, place both script files (together in the same directory) on a machine which is network accessible to the Cyber adAPT skwiid probe.
Set Up
After the script files are placed on an appropriate machine, you are ready for set up.
Open the config.py file to update the following variables:
- Fortra VMAPI_token
This field is required for the script to successfully reach your Fortra VM account data. Enter the API Token that was generated. - skwiid_ip_address
This field is required for the script to reach the API of the skwiid probe. - skwiid_username
This field is used to authenticate the user to pull threat information from the skwiid probe. - skwiid_password
Along with the username, this field is required to authenticate the user.
Save and close the config.py file.
Type of Data Pulled
Below is a table describing the type of data being pulled from both Cyber adAPT and Fortra VM.
| Data Type | Data Description |
| Cyber adAPT Alerts | Cyber adAPT alert data detected by the skwiid probe |
| Fortra VM Hosts | This is the Active View Host client data within Fortra VM |
Executing the integration connector
To pull threat information from Cyber adAPT and tag assets within Fortra VM, run the FrontlineConnector.py script using python:
“python FrontlineConnector.py”