Product Integrations
One Identity Privileged Access Management (PAM)
One Identity PAM solutions mitigates security risks and helps achieve compliance by securing, controlling, monitoring, analyzing, and governing privileged access to critical organizational data and applications. The result is enhanced security and easier compliance with more efficient administration and governance of privileged access.
Configure PAM Appliance Information
-
From the navigation menu, select Scan Settings > PAM Profiles.
-
Select + Add PAM Profile.
-
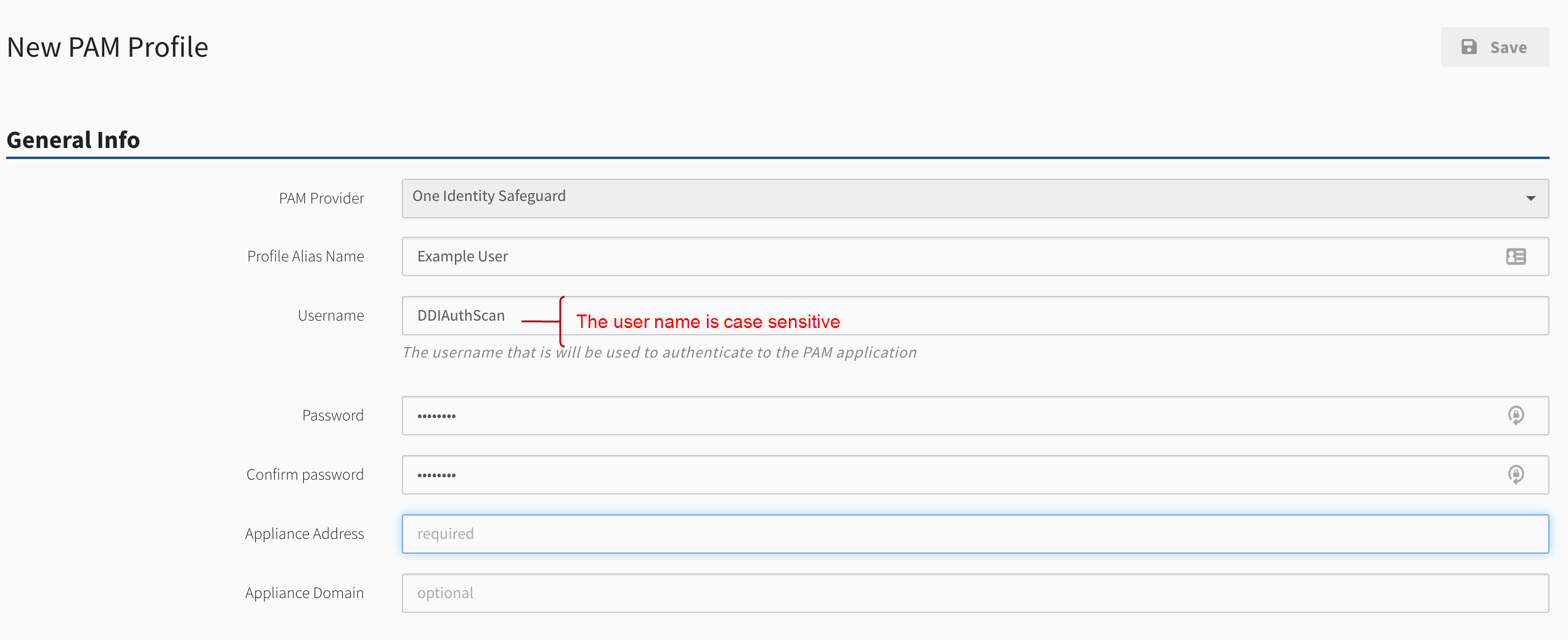
Enter the requested information in each of the General Info boxes.
NOTE: The username for the credential (not the Safeguard PAM user) is case sensitive. This is unlike our normal auth scan in which the username is not case sensitive. For example, LAB\DDIAUTHSCAN works in auth scan , but fails with the PAM scan. LAB\DDIAuthScan works in auth scan and also in PAM scan. DDIAuthScan is the username. -
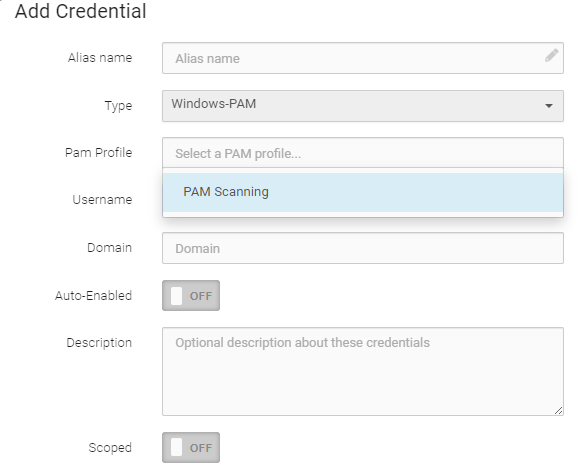
Once you have configured and saved your PAM profile, create scan credentials with your PAM profile as-per-usual through Fortra VM’s existing Credential Manager by selecting Windows-PAM or SSH Password-PAM as the credential type.
-
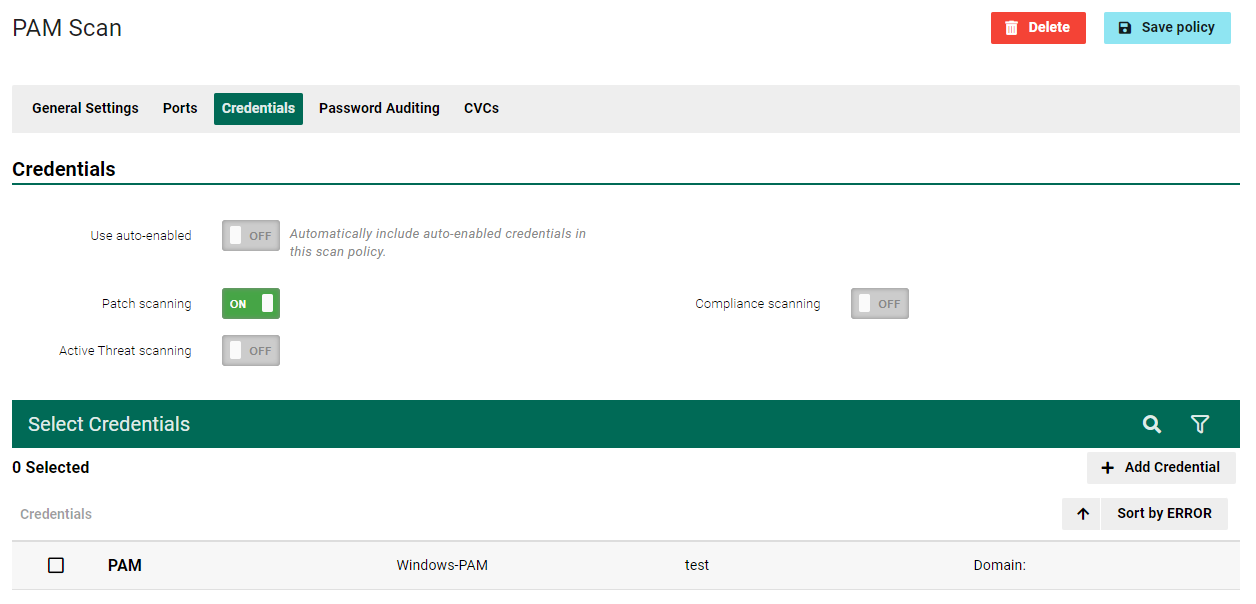
Once you have configured and saved your PAM credential settings, they will be available for use as-per-usual under the Credentials section when configuring Scan Policies.
Scan Requirements
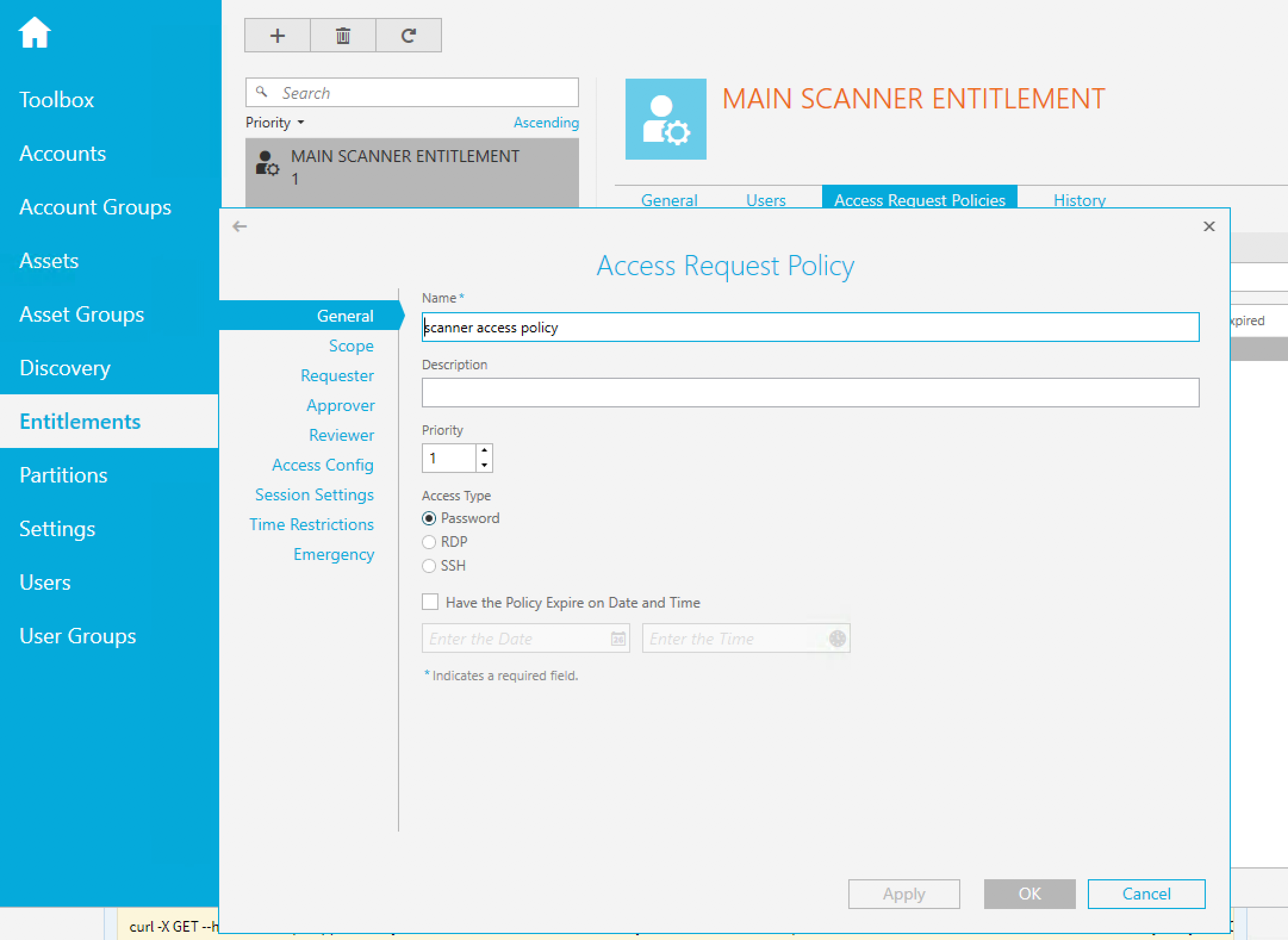
Configure the following in One Identity Safeguard:
-
General: Priority - Set to 1.
-
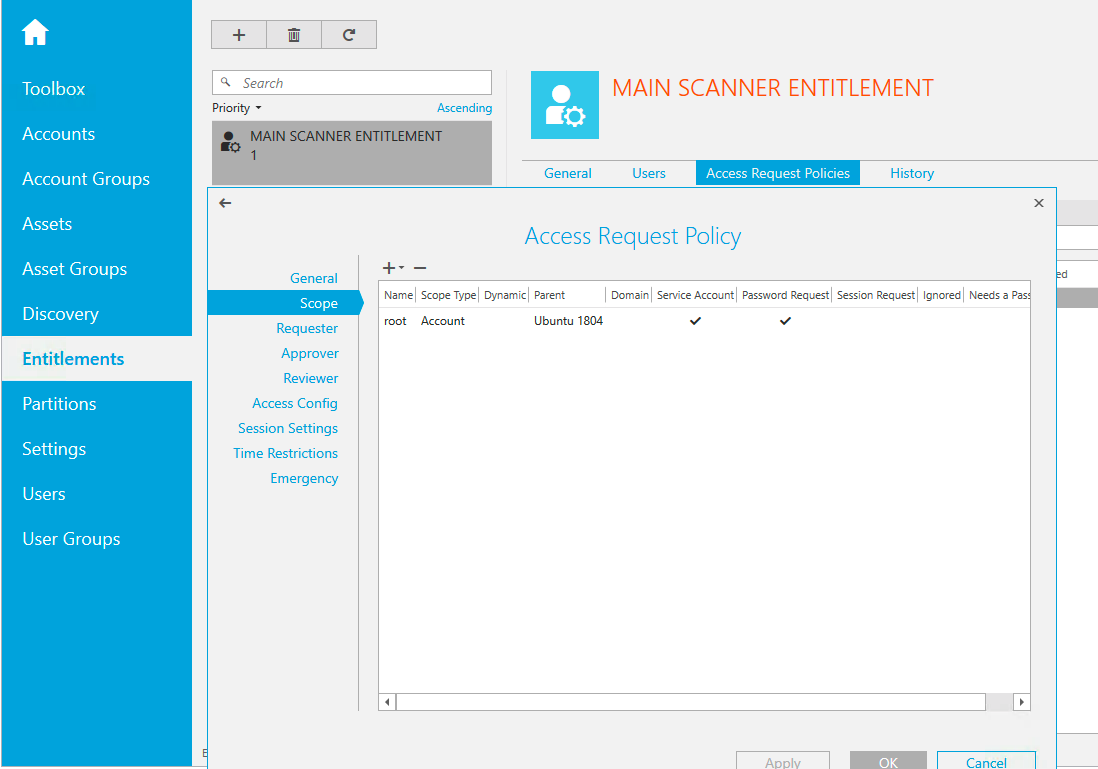
Scope - Add all accounts that will be in use for scanning.
-
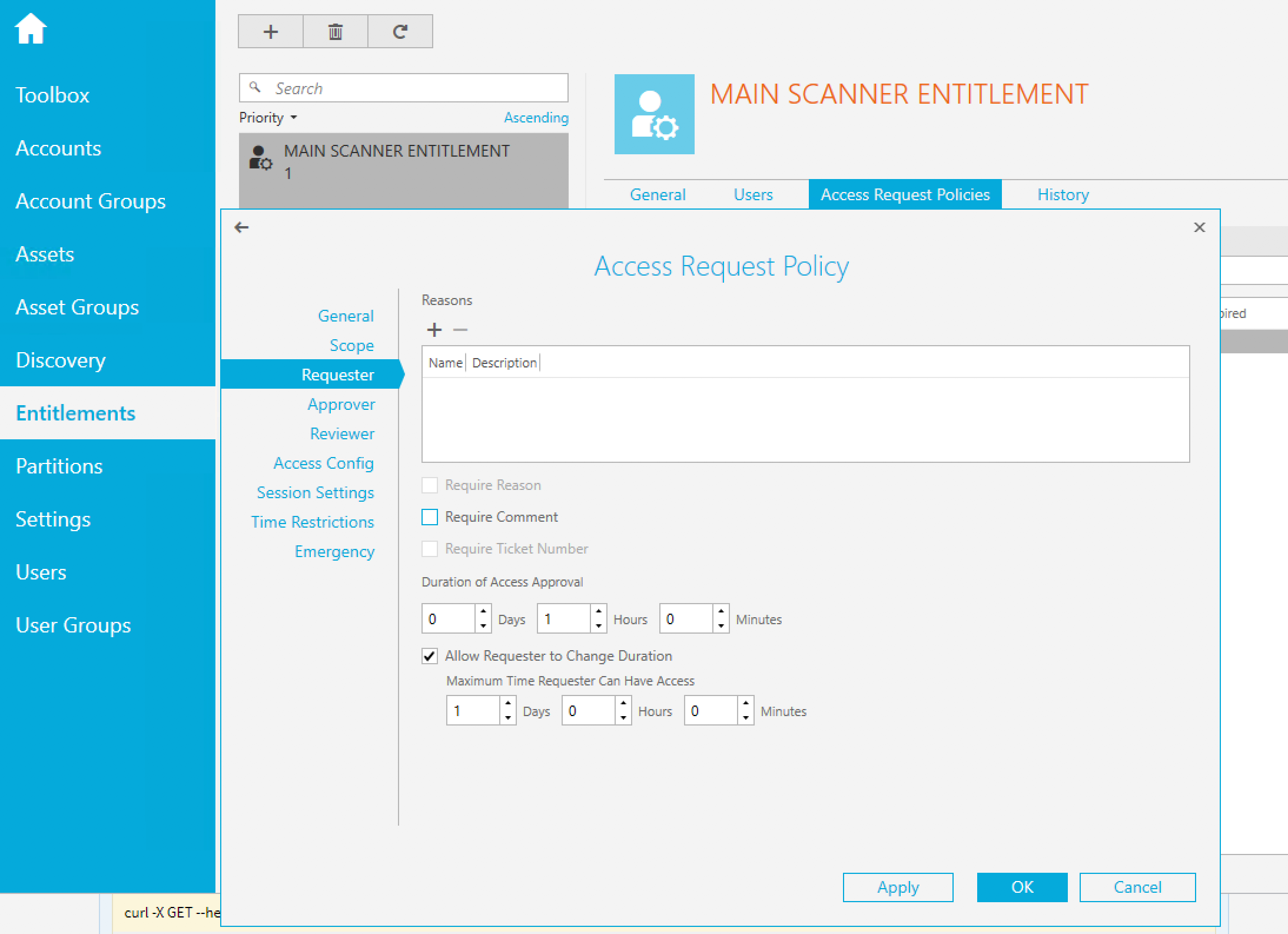
Requester:
-
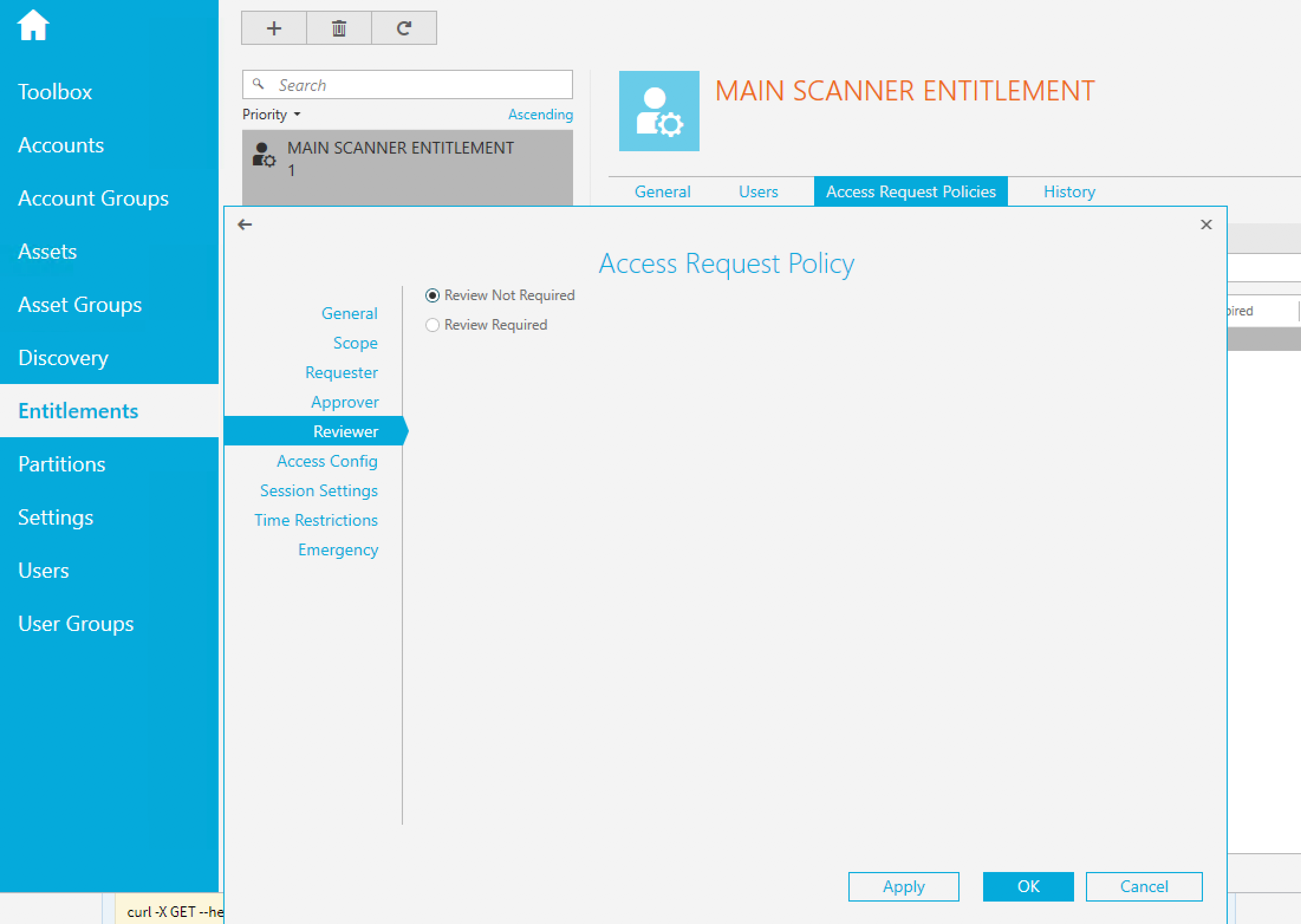
Approver and Reviewer:
-
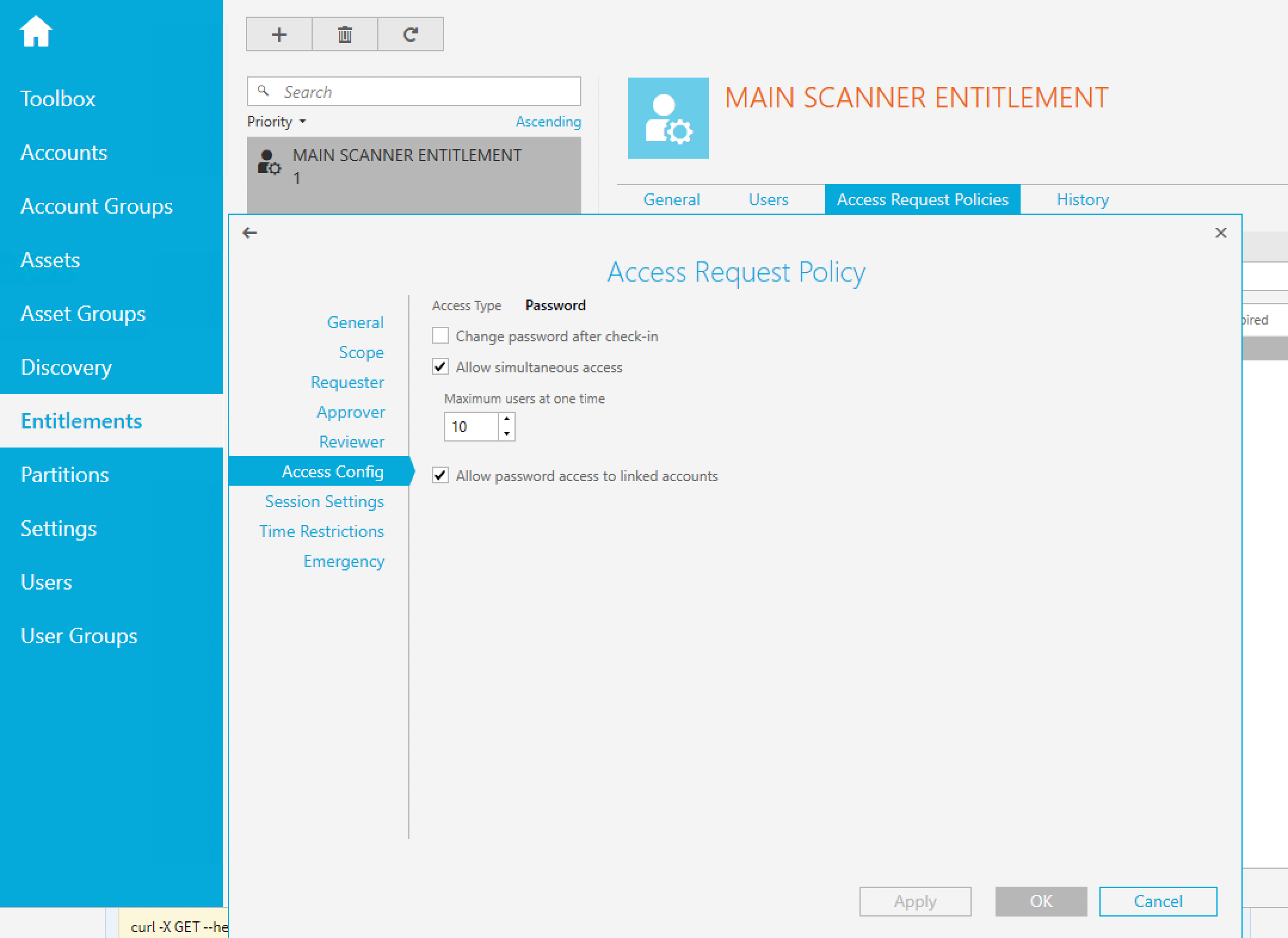
Access Config:
-
Users - The Safeguard User who will use the above described Entitlement must have these minimum permissions as well.