
You have several options for how you configure EFT Server in your network architecture. Some common deployment scenarios are described below. If none of these scenarios exactly meets your needs, GlobalSCAPE's Professional Services team can work with you to design a custom architecture, assist with installation and initial configuration, and help you create custom scripting, Event Rules, Commands, and external user databases.
In the most basic deployment scenario, both end users and business partners (clients) communicate with EFT Server as it resides in your organization's DMZ. All authentication directory service quests and data storage occur inside the demilitarized zone.
EFT Server can be configured to forward all received data to the back-end network to mitigate the risks associated with storing it in the DMZ. This architecture, commonly known as store and forward, means that data only resides in the DMZ temporarily before it is offloaded to a back-end system for processing or storage. This store-and-forward architecture requires a hole to be punched through the firewall in west-to-east fashion, a deviation from security best practices. This architecture is the one most commonly employed by competitors to GlobalSCAPE’s EFT Server solution.

The ideal security solution is to implement a two-tier architecture comprised of EFT Server deployed behind the corporate firewall and EFT Server’s DMZ Gateway deployed inside the demilitarized zone. This setup is known as a streaming or pass-through configuration.

Various hybrid approaches exist consisting of multiple servers in a variety of configurations for different business use cases. Take for example a scenario in which the majority of traffic is outbound push with occasional in-bound pull, initiated by an automated script or batch process. In this scenario, data is generated behind the corporate firewall, then forwarded from one EFT Server to another EFT Server that resides in the DMZ for client pick-up, or directly from the back-end server to a destination server residing at the partner’s location.
|
|
The business need for placing EFT Server in the DMZ often stems from the need to pre- or post-process data as it moves through the DMZ, such as performing an anti-virus scan or an encryption procedure. |
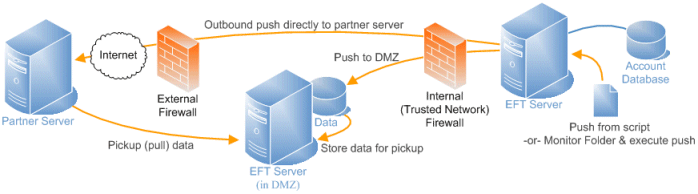
In this hybrid deployment scenario, a client-initiated push and/or pull transaction is brokered through DMZ Gateway, and outbound push transactions are initiated by EFT Server, either from with the corporate firewall, or from an EFT Server residing in the DMZ. In this example, the partner is equipped with a file transfer server to service outbound push operations initiated by EFT Server.
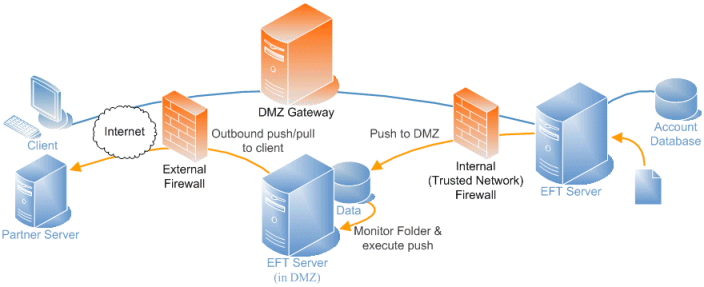
In the architecture illustrated below, 2 EFT Servers and 2 DMZ Gateway Servers in a server cluster meet business continuity requirements requiring the duplication of servers to provide a fail-over cluster.
