You have several options for how you configure EFT in your network architecture. Some common (but not all) deployment scenarios are described below.
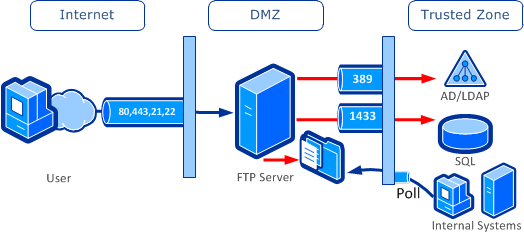
Traditional File Transfer Server Deployment

This is the least expensive deployment option but also the lease secure. This scenario requires inbound ports to backend databases and directories for account authentication. Files deposited into the DMZ will reside there until picked up by back-end systems, resulting in delayed processing. Pushing (rather than polling for) files to back-end systems is also an option, but presents even more security problems.
Secure File Transfer Server Deployment
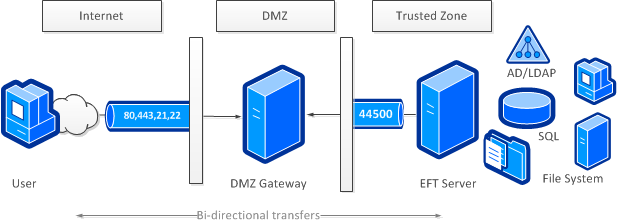
This scenario has a higher upfront cost, but vastly improves security. No inbound holes are required in the trusted zone firewall, because connections are only initiated by EFT Server to the DMZ Gateway proxy. The DMZ Gateway proxy effectively terminates inbound client connections at the gateway, transmitting only the payload of the connection over an independently established connection made by EFT to the gateway. This architecture is fully compliant with security mandates such as those imposed by the PCI DSS regarding where data is stored, since the tier where the FTP server resides is not physically accessible from external sources (because no inbound holes are required in the firewall in front of EFT Server). This architecture can also be used in reverse for transfers initiated by EFT Server, with all outgoing transactions brokered by the gateway over the same single outbound port used for EFT and DMZ Gateway communications. (Refer to the DMZ Gateway documentation for information.
Advanced Deployment Scenario
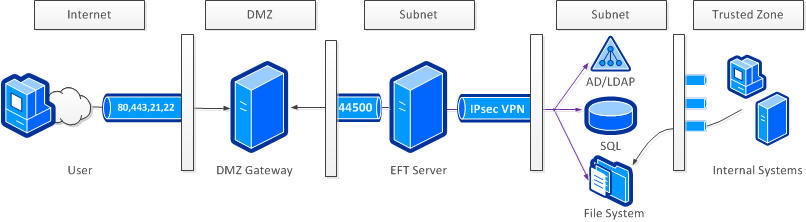
Some organizations require further separation of roles between network zones. One way to accomplish this is to place EFT Server its own subnet outside of the trusted zone. However, this creates the problem of where to write files and how to access data sources. A common solution is to open ports to each of those services in the next zone or, to reduce the number of ports and increase security, deploy an IPsec VPN tunnel into the next zone (as shown), or even into the trusted zone (not shown).
If none of these scenarios exactly meets your needs, Globalscape's Professional Services team can work with you to design a custom architecture.