In a typical network connection, a computer "asks" a server to authenticate it, the server returns the authentication approval to the computer, the computer acknowledges this approval, and then the computer is allowed to connect to the server.
In a denial of service (DoS) attack, a computer sends multiple authentication requests to the server. All requests have false return addresses, so the server can't find the computer when it tries to send the authentication approval. When the server closes the connection, the DoS attacker sends a new batch of forged requests, and the process begins again, causing the server to be unavailable for legitimate connections.
A common method of blocking a DoS attack is to set up a filter on the network that looks for attacks by noticing patterns or identifiers contained in the information. If a pattern comes in frequently, the filter can be instructed to block messages containing that pattern, protecting the server from being overloaded by malicious attacks.
Attacks can be divided into three types:
Connection-oriented attack - Attack that establishes numerous FTP connections to make the server inaccessible.
Command-oriented attack - Attack that establishes a set of connections that flood the server with "hard" commands (commands that require lots of server resources), trying to make the server inaccessible.
Combined attack - Attack that combines both above approaches—the most widespread type.
EFT Server's auto-ban system is intended to prevent possible DoS attack attempts, by identifying possible attacks based on user activity density (occurrences per second). The algorithm in context of each attack type has different implementations.
For a Connection-oriented attack, EFT Server has a map of IP addresses. Each IP address map node contains IP address fail points. Once EFT Server accepts a connection, it finds the corresponding IP address node and increases fail points by connection weight value. If IP address fail points reach a fail points limit, EFT Server refuses the connection and bans the IP address.
A Command-oriented attack is similar to a connection-oriented attack, but instead of an IP address map, EFT Server uses a Connection ID map. The moment a connection is established, EFT Server creates a connection node that contains fail points and an IP address. After each command, EFT Server increases connection fail points by command weight. If connection fail points reach a fail points limit, the connection is closed and the IP address is banned.
The auto-ban sensitivity slider controls connection oriented attacks. It assigns a weight to both recognized and non-recognized commands. Other than that it behaves as connection oriented logic. The Disconnect user after N invalid commands setting looks for sequence of invalid (non-recognized commands) in a row, without regard to time interval between commands. When used together, if a command's points exceed a given threshold in a given period OR if the number of invalid commands in a row exceeds a given threshold, then disconnect and (optionally) ban the user.
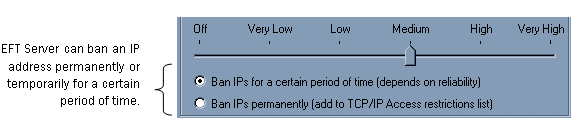
By default, all IP addresses are granted access to EFT Server. EFT Server allows you to grant access to only one specific IP address or a range of IP addresses, or deny access to one specific IP address or a range of IP addresses. EFT Server can automatically disconnect and even ban the IP addresses of computers who send an excessive number of invalid commands. (Refer to Disconnecting Users after a Defined Number of Invalid Commands.) You can configure EFT Server to ban IP addresses automatically that may potentially be associated with a DoS (Denial of Service) attack. EFT Server monitors connection patterns, tracks each computer's activity density, and then bans IP addresses with unnaturally dense activity. When EFT Server bans an IP address, it can ban it permanently (add it to the IP Access Restrictions list) or temporarily for a certain period of time.

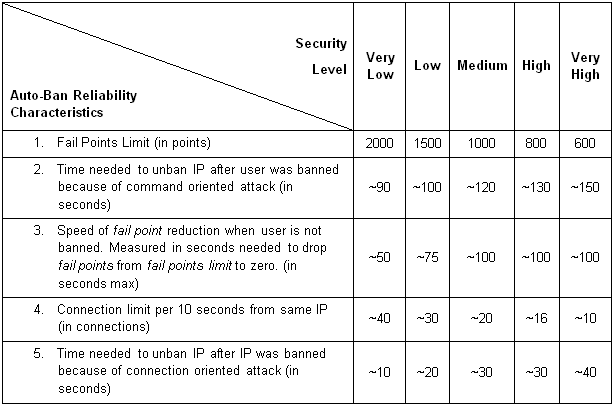
Banning an IP address temporarily protects EFT Server from attacks. If EFT Server is correct and a temporarily banned IP address was the source of an attack, EFT Server will not be harmed by the attempted attack. EFT Server's resources will remain free or minimally burdened, instead of being completely bogged down by the attacking IP address. If you select to ban IP addresses temporarily, the IP address's access to EFT Server is restricted for a minute or two, based on the EFT Server security setting you select using the Auto-Ban Reliability slider bar.
Temporarily banning users means that if EFT Server identifies an ordinary but very active user as a threat, the user will soon be able to reconnect to the Site. When you ban IP addresses temporarily, the level of security you set for the slider indicates both the number of seconds the user can attempt to occupy all of EFT Server's resources before being banned and the number of seconds the user is banned. The higher the security, the less time before the user is banned and the longer the user remains banned.
The reason for a temporary ban is that attack identification is not fool proof and there can always be a chance of a mistake. If EFT Server is allowed to decide which IP address to ban, we risk that some users will be banned by mistake when it might not be appropriate to ban that user permanently.
If you elect to permanently ban the IP addresses of users whose activity fits the pattern of an attack, those users are immediately banned when they exceed the number of connections allowed for the security level (based on the slider setting). If EFT Server has banned a user to whom you want to allow access, you can delete it from the IP address ban list.
With the slider, you can set the Auto-ban reliability (security level) or turn auto ban off. The default is Medium.
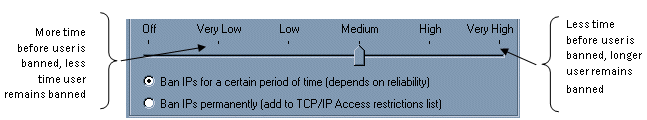
EFT Server has predefined security levels that correlate to the slider values: Off, Very Low, Low, Medium, High, and Very High.
|
|
IP address policy changes are propagated to the DMZ Gateway whenever the policy is modified in the administration interface or by the auto-ban logic. |
To activate auto-ban
In the administration interface, connect to EFT Server and click the Server tab.
In the left pane, click the Site you want to configure.
In the right pane, click the Connections tab.
In the Network Usage and Security Settings area, next to Denial of Service settings, click Configure. The Anti-Flood/Hammer Settings dialog box appears.
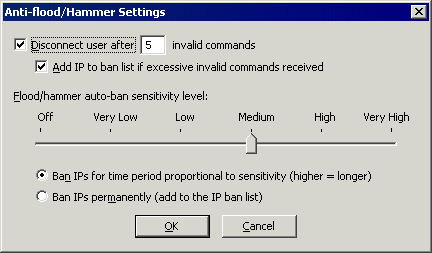
In the Flood/hammer auto-ban sensitivity level area, specify a sensitivity level using the slider bar.
|
|
If you set the slider to Off, Very Low, or Low on a PCI DSS Site, a message appears to warn you that this setting violates PCI DSS requirement 2.2.3, and allows you to continue with reason or choose a different setting. |
Click a ban period:
Ban IPs for time period proportional to sensitivity (higher = longer)
Ban IPs permanently (add to TCP/IP access restrictions list)
Click OK to close the dialog box.
Click Apply to save the changes on EFT Server.
See also Disconnecting Users after a Defined Number of Invalid Commands and Controlling Access to the Site by IP Address.