![]()
The HSM checks the key length and expiration date only for EFT Server's SSL certificates (i.e., administration certificate and Site certificates); client certificates (i.e., trusted certificates) are not checked.
EFT Server can sign certificate requests created by other clients. Typically, the client certificate request is signed with the certificate created for EFT Server. If a certificate from the FTP server's Trusted Certificates database is used to sign client certificates, then all certificates you sign are automatically trusted.
|
|
The HSM checks the key length and expiration date only for EFT Server's SSL certificates (i.e., administration certificate and Site certificates); client certificates (i.e., trusted certificates) are not checked. |
To sign a certificate request
Obtain the Certificate Signing Request file (.csr). This can be done through e-mail or any other file delivery method.
In the left pane, click the Server or a Site node. (If EFT Server Group node is selected, the certificate options are unavailable.)
On the main menu, click Tools > Sign SSL Certificate, or click the Certificate Signing Utility icon ![]() . The Certificate Signing Utility dialog box appears.
. The Certificate Signing Utility dialog box appears.
In the Client certificate request box, click the folder icon ![]() to browse for and specify the Certificate Signing Request (.csr) file that you want to sign.
to browse for and specify the Certificate Signing Request (.csr) file that you want to sign.
In the Output path box, click the folder icon ![]() to browse for and specify the folder in which to save the signed certificate (.crt) file.
to browse for and specify the folder in which to save the signed certificate (.crt) file.
In the Resulting certificate expiration date box, click the list to open a calendar in which to specify an expiration date.
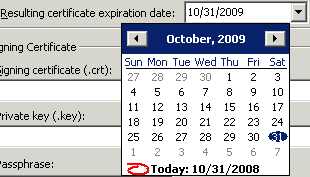
Click the left- and right-facing arrows to scroll through the months.
In the Signing certificate box, specify the certificate (.crt) that you want to use to sign the certificate request file (.csr). The signing certificate must be in your trusted certificate database in order for clients submitting the signed certificate to connect to the Site.
In the Private key box, specify the private key file (.key) associated with the signing certificate.
In the Passphrase box, provide the passphrase associated with the signing certificate.
Click OK. The new certificate is saved in the folder you specified.
Return the certificate file (.crt) to the user.