![]()
Outbound connection information is audited in that same folder in a log named cl<date>.log.
To monitor EFT Server activity, you can reference EFT Server’s log files. EFT Server supports W3C, Microsoft IIS, and NCSA log file formats. Server events are logged to a file named [log file format]yymmdd.log, where YY, MM, and DD indicate the numeric year, month, and day respectively. Depending on the log file format selected, a 2-letter abbreviation is prepended to the filename, as described in the table below. For example, a log file in the Microsoft IIS format created on August 22, 2007 is named in070822.log.
Logs are saved by default to C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\EFT Server Enterprise\Logs or C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\EFT Server\Logs, but you can specify a different location on the Logs tab of the Server, as shown below. (On Windows 2008, Application Data files for all users are in a hidden folder named %systemroot%\ProgramData instead of under Documents and Settings\All Users\Application Data.)
|
|
Outbound connection information is audited in that same folder in a log named cl<date>.log. |
|
Log File Format |
Abbreviation |
|
ex |
|
|
nc |
|
|
in |
Log Example
Below is an example of an ex-formatted log:
#Version: 1.0
#Software: CuteLogger
#Date: 2010-04-08 20:07:50
#Fields: date time c-ip c-port cs-username cs-method cs-uri-stem cs-uri-query sc-status sc-bytes cs-bytes s-name s-port
2010-04-08 20:07:07 192.168.241.1 - test [1]user test - 331 - - - 22
2010-04-08 20:07:07 192.168.241.1 - test [1]pass ******* - 230 - - - 22
2010-04-08 20:07:16 192.168.241.1 - test [1]created /Test+File+1.txt - 226 - 54 - 22
2010-04-08 20:08:23 192.168.241.1 - test [1]rnfr /Test+File+1.txt - 350 - - - 22
2010-04-08 20:08:23 192.168.241.1 - test [1]rnto /Test+File+2.txt - 250 - - - 22
2010-04-08 20:08:26 192.168.241.1 - test [1]sent /Test+File+2.txt - 226 - 54 - 22
2010-04-08 20:10:02 192.168.241.1 - test [1]dele /Test+File+2.txt - 250 - - - 22
2010-04-08 20:10:08 192.168.241.1 - test [1]ssh_disconnect timeout - 421 - - - 22
2010-04-08 20:10:09 192.168.241.1 - test [1]ssh_disconnect timeout - 421 - - - 22
2010-04-08 20:11:57 192.168.241.1 - test [2]user test - 331 - - - 990
2010-04-08 20:11:57 192.168.241.1 - test [2]pass ****** - 230 - - - 990
2010-04-08 20:12:04 192.168.241.1 - test [2]created /Test+File+1.txt - 226 - 54 - 990
2010-04-08 20:12:16 192.168.241.1 - test [2]rnfr /Test+File+1.txt - 350 - - - 990
2010-04-08 20:12:16 192.168.241.1 - test [2]rnto /Test+File+2.txt - 250 - - - 990
2010-04-08 20:12:28 192.168.241.1 - test [2]rnfr /Test+File+2.txt - 350 - - - 990
2010-04-08 20:12:28 192.168.241.1 - test [2]rnto /Test+File+3.txt - 250 - - - 990
2010-04-08 20:12:31 192.168.241.1 - test [2]sent /Test+File+3.txt - 226 122 - - 990
The log can be read as described below:
|
Field |
Description |
Example (Each field in the log has either a value (e.g., date) or a dash (-) if no value was sent for that field.) |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
date |
Date log was recorded |
2010-04-08 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
time |
Time log was recorded |
20:07:16 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
c-ip |
Client IP address |
192.168.241.1 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
c-port |
Client port |
21 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
cs-username |
Username |
test |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
cs-method |
Method (Command Sent) |
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
cs-uri-stem |
Stem portion of URI |
/Test+File+1.txt |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
cs-uri-query |
Query portion of URI |
- |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
sc-status |
Status code |
226 (Closing data connection. Requested file action successful.) |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
sc-bytes |
The number of bytes that the server sent to the client. |
541 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
cs-bytes |
The number of bytes that the client sent to the server. |
54 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
s-name |
|
- |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
s-port |
Server port |
22 |
|
|
For information about log file formatting, refer to http://www.microsoft.com/technet/prodtechnol/WindowsServer2003/Library/IIS/be22e074-72f8-46da-bb7e-e27877c85bca.mspx?mfr=true |
In the administration interface, connect to EFT Server and click the Server tab.
In the left pane, click the Server node.
In the right pane, click the Logs tab.
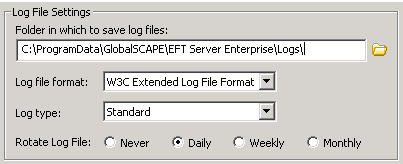
In the Log File Settings area, in the Folder in which to save log files box, type the path to the directory in which to save this Server's log files. To browse for a path, click the folder icon ![]() .
.
|
|
By default, log files are saved in the EFT Server data directory in the Log folder (e.g., C:\Documents and Settings\All Users\Application Data\GlobalSCAPE\EFT Server Enterprise\Logs). On Windows 2008, Application Data files for all users are in a hidden folder named %systemroot%\ProgramData instead of under Documents and Settings\All Users\Application Data. |
In the Log file format list, click W3C Extended, Microsoft IIS, NCSA Common, or No Logging.
|
|
Changing the log file format disconnects all active users. It is recommended to stop all Sites or wait until all users are inactive before changing the log file format. |
In the Log type list, click Standard or Verbose. (Verbose provides more details, but makes larger files.)
In the Rotate Log File area, specify Never, Daily, Weekly, or Monthly.
Click Apply to save the changes on EFT Server.
|
|
Logs are not written to disk in real time. As events occur, EFT Server buffers those events in real time and then flushes (writes) them to file after either a) 60 lines are available or b) 32kb of log data is received in 1 second or less. |
|
|
For information about the Audit Database Settings, refer to Auditing Database Errors and Logging. |