EFT Server provides the option to force password reset. On HS-enabled Sites, users are forced to change their passwords on first use.
You can enable the password reset page while disallowing general access to HTTP or HTTPS. When a new user logs in to EFT Server via the HTTP or HTTPS index page, EFT Server redirects the user to the reset page. After the user creates a new password, they are returned to the index page.
|
|
Password initial reset, expiration, and account management
features only apply to GlobalSCAPE and ODBC authentication Sites. These
options are not available if other authentication types (AD Active Directory; a Microsoft implementation of LDAP directory services
used to provide central authentication and authorization services for
Windows-based computers.,
LDAP, etc.) are used. Password security features all apply at EFT Server
level, not to individual accounts. |
When a user logs in to the HTTPS index page and the Force reset check box is selected, the user is automatically redirected to the reset page if:
The /manageaccount page is enabled and the user logs in with a temporary password.
The /manageaccount page and Redirect HTTP to HTTPS options are enabled, and the user logs in with a "temporary" password.
The user logs in with a temporary password to the FTP port or SFTP engine. (No commands are allowed other than exiting or changing the password until the password has been changed, and the user is prompted to change the password.)
An administrator logs in using a temporary password. A warning appears to prompt the administrator to supply a new password.
To configure user accounts to enforce password reset
In the Administrator, connect to EFT Server and click the Server tab.
In the left pane, click the user or Settings Template you want to configure.
In the right pane, click the Security tab.
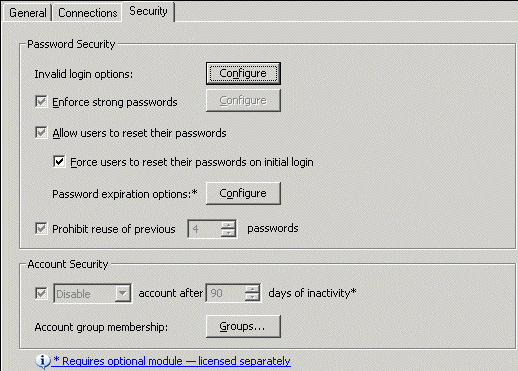
Select the Allow users to reset their passwords check box.
Select the Force users to reset their passwords on initial login check box.
Configure password expiration and invalid login options, if desired.
Click Apply to save the changes on EFT Server.
When a password is reset, EFT Server verifies the new password against complexity criteria and password history, if those features are enabled. Users are not allowed to proceed with their session until a password is created and accepted by the system. If the password is not accepted by the system:
In HTTPS and SFTP, the authentication request will be denied.
In FTP, no further FTP commands will be accepted until the new password is provided and meets complexity and password history requirements, if those features are enabled.
For HS-enabled Sites:
PCI DSS requirement 8.5.3 states that you should set first-time passwords to a unique value for each user and force users to change their password immediately after the first use.
PCI requirement 8.5.9 states that users should change their passwords at least every 90 days.
PCI requirement 8.5.8 states that you should generate unique passwords for each user. These requirements apply to both end users and administrators.
PCI requirement 8.5.10 states that you should generate strong passwords. Manual entry of passwords is disallowed in the Create New User and Change Password dialog boxes; users and administrators are forced to generate complex passwords by clicking Generate, to avoid the possibility of reusing the same password.
If a Site is running in PCI Compliance mode, warnings appear in the following situations:
If you clear the Force users to reset their passwords on initial login or Admin must reset their password at next login check box.
If you clear the Allow users to reset their password check box.
If you disable account management over HTTPS, and the Force users to reset their passwords on initial login or Expire passwords after <n> days check boxes are enabled.
If you clear the Force users to reset their passwords on initial login or clear the Enable account management page over HTTPS check boxes.