A self-signed certificate contains a public key, information about the owner of the certificate, and the owner's signature. It has an associated private key, but it does not verify the origin of the certificate through a third-party certificate authority.
To achieve the highest level of authentication between critical software components, do not use self-signed certificates, or use them selectively.
A certificate (Certificates are digital identification documents that allow both servers and clients to authenticate each other. A certificate file has a .crt extension.) on the client must be associated with EFT Server to initiate an SSL (Secure Sockets Layer, a protocol designed and implemented by Netscape Communications, provides for encryption of a session, authentication of a server, and optionally a client, and message authentication.) connection. When you are administering EFT Server on the local computer, you can create certificates using the Certificate Creation Wizard (Tools > Certificate Creation Wizard) or import your own. There are three types of files associated with an SSL certificate key pair:
Private key file (.key) - The private key (EFT Server's private key decrypts the client's session. The private key has a .key extension and is part of the public-private key pair.) should never be distributed to anyone. It is used to decrypt the session, which is encrypted by the public key (A message encrypted with a recipient's public key cannot be decrypted by anyone except the recipient possessing the corresponding private key. See Private Key.).
Certificate request file (.csr) - Each time you create a certificate using EFT Server, a Certificate Signing Request file is also created. A Certificate Signing Request (CSR) is a PKCS10 request, which is an unsigned copy of your certificate. This file can be signed by EFT Server's Certificate Signing Utility or sent to an intermediate certificate authority, such as GeoTrust, for signing.
Certificate file (.crt) - This is a signed certificate, whether self-signed or signed by an intermediate certificate authority.
For maximum compliance with security standards, you should use a trusted authority signed SSL certificate. You can import certificates or use this wizard to create your own. The private key (.key) and certificate request (.csr) files are created at the same time. You are prohibited from creating certificates for EFT Server while remotely administering EFT Server because this action can create a security breach. Any certificates you create remain on the computer on which you created them, unless you take special steps to deliver and associate these files with another computer.
To create an SSL certificate
In the Administrator, connect to EFT Server, click the Server tab, then do one of the following:
On the main menu, click Tools > Create SSL Certificate.
On the toolbar, click the New SSL Certificate
icon ![]() .
.
On the keyboard, press ALT+T+C.
The Create SSL Certificate wizard appears.

In the Certificate name box, specify the name of the certificate that will be generated.
In the Path box, specify the path to the folder in which the certificate is to be saved. The wizard saves the .key, .csr, and .crt files in this folder (e.g., C:\Documents and Settings\All Users\Application Data\Globalscape\EFT Server or \EFT Server Enterprise).
|
|
If you are purchasing a signed certificate from a certificate authority (CA), you usually need to forward the contents to the CA. To do this, locate the .csr and open it in a text editor; then you can copy and paste the contents. |
In the Expiration Date box, specify the date on which the certificate will expire.
In the Passphrase and Confirm passphrase boxes, type the passphrase used to encrypt the private key. The passphrase can be any combination of characters or spaces. Do not lose the passphrase; the certificate is useless without it.
In the Key Length (in bits) box, specify the key length: 512, 1024, 2048, and 4096 bits. Smaller keys are faster, larger keys are more secure.
|
|
If you create a certificate with a key length of 4096 bits or greater, the Web Transfer Client will not function properly due to its reliance on the Java runtime (JRE), which currently does not support key lengths of 4096 bits or greater. |
Click Next. The Certificate Information page appears.
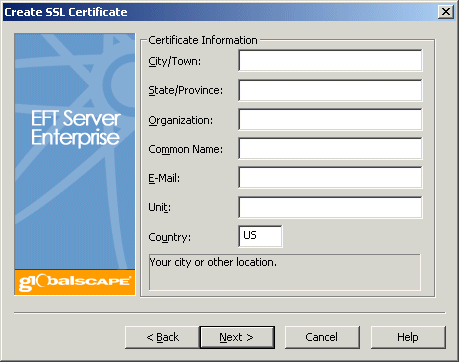
Each of the boxes must be completed before continuing. The information you provide is stored in the certificate.
In the City/Town box, provide the name of your city, town, or other locality.
In the State/Province box, provide the name of the state or province.
In Organization box, provide the name of your organization, or any other designator.
In the Common Name box, provide the common name or fully qualified domain name, such as www.globalscape.com. (Typically, the name or domain name associated with the Site.)
In the E-Mail box, provide your e-mail address in the format username@domain.com.
In the Unit box, type any other information about your organization, such as department name.
In the Country box, provide the 2-letter ISO country code using uppercase letters.
Click Next. The Certificate Options page appears.
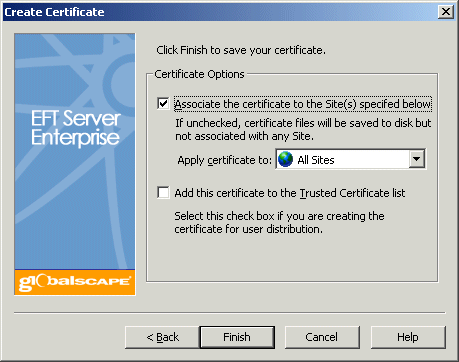
If the Associate the certificate to the Site(s) specified below check box is cleared, the wizard saves only the certificate files in the folder you previously specified, but does not associate it with any Site. If the check box is selected, the wizard associates the certificate to the administration service or Site(s) you specify in the Apply certificate to box.
In the Apply certificate to box, specify which components of EFT Server are affected (Administration Service, All Sites, or a specific Site).
|
|
Associating a new certificate with a Site requires a restart of the Site, and any active users will be disconnected, so it is recommended that you associate certificates when Sites are inactive or stopped. |
If the Add this certificate
to the Trusted Certificate list check box is selected, the wizard
adds the certificate to the Trusted Certificates database. Use this feature
if you are creating certificates for user distribution. You can limit
EFT Server access to just the users that have the certificate. You can
verify the addition to the Trusted Certificate database by clicking Tools > Certificate
Manager or, on the toolbar, click the Certificate
Manager icon ![]() . (Refer to The
Certificate Manager for more information.)
. (Refer to The
Certificate Manager for more information.)
Click Finish.