In EFT Server, when EFT Server warns you of a non-compliant setting, if you do not specify a setting that meets the PCI DSS requirement, you can specify the compensating controls (Compensating controls may be considered when an entity cannot meet a requirement explicitly as stated, due to legitimate technical or documented business constraints but has sufficiently mitigated the risk associated with the requirement through implementation of other controls. Compensating controls must 1) meet the intent and rigor of the original stated PCI DSS requirement; 2) repel a compromise attempt with similar force; 3) be "above and beyond" other PCI DSS requirements (not simply in compliance with other PCI DSS requirements); and 4) be commensurate with the additional risk imposed by not adhering to the PCI DSS requirement) (hardware, software, or policy) you are using to satisfy the requirement. The information that you provide in the warning message appears in the Compliance report, which you can provide to Qualified Security Assessors (QSAs) or Approved Scanning Vendors (ASVs), individuals who are certified by the PCI Security Standards Council as being qualified to validate compliance to the PCI DSS requirements.
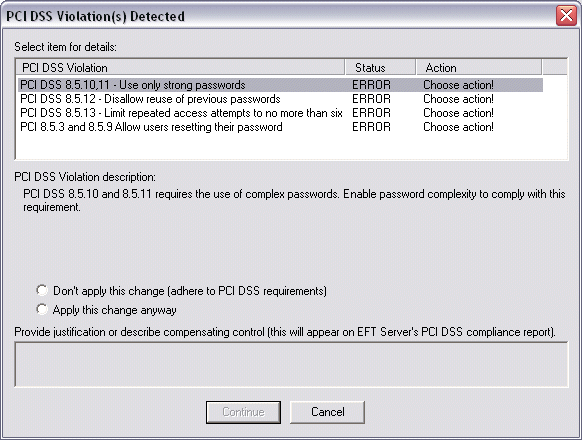
For High Security Sites, if you attempt to change a setting that would cause the Site, Settings Template, or a user account to no longer meet PCI DSS requirements, when you click Apply to save the changes on EFT Server, EFT Server does not commit the change, and a warning message appears that describes one or more violations, as shown below.
|
|
If you do not activate the HS module, this feature is disabled when the 30-day trial is expired. |
In the PCI DSS Violations dialog box, you can accept the non-compliant setting (Apply this change anyway) and provide a reason for accepting each setting (e.g., if you are using an alternate solution) or you can discard the change (Don't apply this change). If you accept the change and provide a reason, the warning and the reason that you provided appear in the Compliance report.
Related settings are audited and reported on as a group (e.g., all of the SSL-related settings or all of the account-related settings). For example, suppose on Monday you disable the account lockout settings for a user and specified in the PCI DSS Violations dialog box your reason for allowing this non-compliant setting. Then on Wednesday you change a complex password setting. The PCI DSS Violations dialog box appears and displays both of these settings, as well as others for which you provided a reason, and you will be required to allow the change and specify a reason or discard the changes for each of the non-compliant settings before EFT Server commits the changes. (That is, the allow or discard flag is separate, but they are audited and reported on as a group.) This functionality is designed to remind you of the non-compliant settings in case you want to bring them into compliance in EFT Server.
|
|
ARM is used to store the PCI DSS violations. If ARM is disabled, the violations are still recorded; however, the justifications that you type when you accept a non-compliant setting are not recorded in the database. You can still run the Compliance report, but the justifications that you provide will not appear in the report. When settings are changed via the COM API that affect PCI DSS compliance, no warning message appear. COM to apply the changes but EFT Server will reject the change with an "error 53." Refer to the GlobalSCAPE Server COM API user guide for a script example that can be used to capture such errors. |
If PCI DSS Violations are detected
Click a violation in the list, then do one of the following for each of the violations listed:
If you want to correct the violation, click Don't apply this change, click Continue, correct the setting, then click Apply.
If you want to keep the non-compliant setting, click Apply this change anyway, then in the Provide justification and describe compensating control box, type the reason for keeping the non-compliant setting. The description will appear in the compliance report.
Click Continue. You must address each violation in the list before you can click Continue.
Reporting of failed items occurs at the highest level of failure only, except in the case of an explicit setting that violates compliance. For example:
If a Site failed compliance because Enforce strong (complex) passwords was disabled (check box cleared), the report is generated for the entire Site.
If Enforce strong (complex) passwords was enabled for the Site, but was disabled for a Settings Template, the report is generated for the Settings Template.
If Enforce strong (complex) passwords was enabled at the Site and Settings Template, but disabled for some users, EFT Server reports for each of those users.
If Enforce strong (complex) passwords was disabled at the Site level, enabled at the User Setting Level, and disabled for a user, the warning appears for the Site violation and for the user account that is in violation.