![]()
The FIPS 140-2 validated GSCM is based on the openssl-fips-1.1.1 FIPS source and the openssl-0.9.7m project. If FIPS is not enabled, the non-FIPS SSL version of OpenSSL 0.9.8h is used.
The Federal Information Processing Standard (FIPS) Publication 140-2 specifies the security requirements of cryptographic modules used to protect sensitive information. Secure FTP Server (FIPS) supports operation with the FIPS 140-2 Validated GlobalSCAPE Cryptographic Module (GSCM) for SSL/TLS and certificate generation. Imported certificates that were signed using non-FIPS compliant algorithms will be invalid.
Secure FTP Server (FIPS) supports all of the file transfer protocols currently supported by the non-FIPS version of Secure FTP Server (FTP, FTPS, SFTP, HTTP, and HTTPS). SSL protocols (FTPS or HTTPS) are FIPS-compliant protocols.
|
|
The FIPS 140-2 validated GSCM is based on the openssl-fips-1.1.1 FIPS source and the openssl-0.9.7m project. If FIPS is not enabled, the non-FIPS SSL version of OpenSSL 0.9.8h is used. |
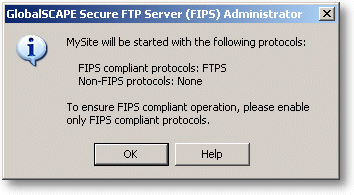
The SSL library is loaded when the Server service is started, and a
message box displays which protocols are in use and which of the protocols
in use are FIPS compliant.
A series of startup tests, including Known Answer Tests (KAT) and library-integrity checks, determine whether the GSCM is initialized successfully. Secure FTP Server (FIPS) is designed to operate only with the GSCM initialized into the FIPS-approved mode; you cannot operate the Secure FTP Server (FIPS) application without the GSCM being initialized into the FIPS-approved mode. If GSCM initialization fails:
Encryption services are disabled, an error message appears, all Sites and protocols are disabled, and a Windows Event log is created.
When you attempt to restart the Site, a message indicates that the Site cannot be restarted, because GSCM initialization failed. After you dismiss the message, the Secure FTP Server Administrator (client) closes. If restarting the Server service does not correct the issue, contact GlobalSCAPE Customer Support for assistance.
Secure FTP Server uses one of the following three cipher combinations during SSL/TLS negotiation:
TLS 1.0 RSA Key Exchange, RSA Authentication, 256 bit AES encryption, and SHA1 HMAC
TLS 1.0 RSA Key Exchange, RSA Authentication, 168 bit 3DES encryption, and SHA1 HMAC
TLS 1.0 RSA Key Exchange, RSA Authentication, 128 bit AES encryption, and SHA1 HMAC
The use of the SHA1 HMAC is TLS 1.0 specific. By limiting the algorithms, we force use of TLS 1.0 in Secure Server. For more info on why FIPS requires TLS 1.0, refer to http://www.mail-archive.com/openssl-users@openssl.org/msg54318.html.
The order of preference, as listed above, is provided by Secure FTP Server to the SSL client (e.g., the Administrator interface or CuteFTP). During SSL negotiation, the SSL client is allowed to select its preferred combination from this list. By default, the SSL client typically picks the highest common denominator. Secure FTP Server allows only these three cipher combinations; the algorithms cannot be NULL. FIPS certifies both DSA and RSA for digital signature generation and verification, but only allows RSA for key wrapping. Since SSL requires key wrapping, when Secure FTP Server is in FIPS mode, only RSA can be used. Per FIPS requirements for RSA key wrapping, the Server enforces a minimum key length of 1024 bits and a maximum key length of 4096 bits.
|
|
If the Server requires certificates from connected clients, those certificates must also use SHA-1. |
|
|
For more information about certification of the GlobalSCAPE Cryptographic Module (GSCM), refer to the Module Validation List on the National Institute of Standard and Technology (NIST) Website at http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/140val-all.htm#908. The GSCM’s certificate number is 908. |