Mobile Transfer Client FAQ
Frequently asked questions (FAQ) are answered below.
Where do I get the MTC app?
In the Google Play Store or Apple App store, search for globalscape.com.
What protocols does MTC support?
MTC only uses HTTPS. This protocol provides transport security and a rich mechanism (using headers) for communicating with EFT about things like security policies, file checksums, and other advanced features that older protocols such as FTP and SFTP cannot provide.
What if I want to use FTP or SFTP?
There are plenty of free and for-pay FTP and SFTP clients available to iOS and Android; however, those apps do not offer the same policy and security controls as provided by MTC.
What authentication mode does MTC use?
MTC relies on Basic Auth over an encrypted HTTPS connection. Session (Form)-based authentication is being considered for a future version.
Why can’t I just use my mobile browser to download files instead of using your native app?
You can to a certain extent if you log in to the WTC in your mobile browser. However, what you can do once you connect is severely limited by the mobile operating system and browser you choose to use, and also lacks the security policy features provided by MTC.
What prevents my users from using a mobile SFTP or FTPS client or third-party browser?
Nothing really; but that is no different from today when it comes to your user’s choice of desktop-based client. As the administrator you can turn off SFTP or FTPS support entirely, or allow these protocols knowing that you can’t control the app your user chooses to use as their client. The benefit of using MTC is that you can set a corporate policy that mandates that users only use the MTC client to interact with EFT from their mobile device, as MTC provides a level of governance and control due to its centrally managed security policies. EFT logs can demonstrate whether users are using MTC or not based on the protocol used and the http user-agent string (keep in mind user-agent strings can be forged). And organizations with an MDM solution in place can enforce the use of MTC by whitelisting MTC and blacklisting any other file transfer client app that doesn’t meet IT’s security requirements.
Does the MTC app protect (encrypt) data at rest?
Yes. MTC leverages the OS level encryption for encrypting contents at rest. In iOS this means the user MUST be using a pin code to unlock their device. If the user has not established a pin code then data will not be encrypted while at rest. When the device is unlocked (user enters their pin code), an OS-wide decryption key is created that MTC will leverage when reading files from disk. When a user performs an "Open In" or "Share as Link" operation, MTC takes a decrypted COPY of the cached file and passes it to the third-party app, assuming those operations are allowed by the security policy. The third-party app may or may not use the encryption class, meaning the file is not guaranteed to be encrypted when saved to disk by the third-party app (e.g., they assign the file to the NSFileProtectionNone class).
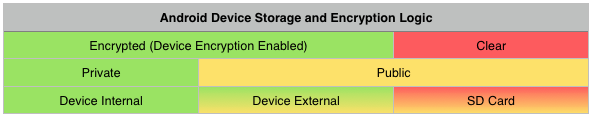
Android is a bit more problematic as apps and their data are not completely sandboxed. Starting with Android 3.0 you can enable whole disk encryption; however, once you enter your pin code, your device is decrypted device-wide, and nothing prevents the user or another app on the device (deliberately run by the user or otherwise) from accessing the data directory for any other app. To prevent this breach of data privacy, MTC leverages Android’s so-called "internal" data storage, a relatively small partition of the overall non-removable physical storage that acts like a data sandbox, preventing both the user and app from accessing files downloaded from EFT into MTC’s cache or offline vault. Contrast this "internal" storage with the so-called "external" storage (not to be confused with the physically inserted SD card) which represents the remainder of the non-removable hard-drive and allows any app on the device to access any other apps’ data. The downside of using internal storage is that it is usually about a tenth or less of the overall non-removable disk space. Using a physically inserted SD for storage is simply out of the question because neither encryption nor data privacy are extended to this truly external, removable storage media type. Below is a graphic that helps illustrate Android’s various partitions and how encryption and privacy (data sandboxing) apply. MTC follows the purely green path. However, keep in mind that data will only be encrypted if the device-wide encryption is enabled on the device.
Are there any restrictions for MTC to work in EFT?
Yes. HTTPS must be enabled and the Site must rely on a single-factor authentication manager (AD, LDAP, ODBC, or GS Auth). Sites using RSA SecurID, RADIUS 2FA, or CAC-based authentication will result in failed MTC login attempts.
How do I troubleshoot MTC connection problems?
MTC can optionally keep a detailed log of all its transactions including the HTTP transport stream. There is even an option in the MTC log viewer for the user to email the log so that you can review decrypted HTTPS requests and responses and assist the user in determining why an operation failed. Alternatively, you can use EFT’s eft.log file (after enabling the HTTP logger) to view decrypted HTTPS sessions. Most of the time what you are looking for is 401s (authentication failed), 404s (the resource requested was not found), or 503s (insufficient permission for the requested resource).
Does MTC support forced password reset, user-initiated password changing, lost password reset, and username recovery?
Forced password reset upon initial (or next) login is supported by MTC. User-initiated password change is not supported, but they can still do this from their desktop or even mobile browser. MTC also supports lost password reset and lost username recovery.
I have multiple Sites that are accessible to the same set of users. Can MTC accommodate multiple Sites?
Yes, MTC supports the concepts of Profiles, which are essentially the same as accounts on EFT Sites.
Can my users download a file to their device, make changes to the file, then re-upload the file back to EFT?
Yes, assuming "Allow opening of files in external apps" is enabled.
-
On iOS devices, when the user chooses to open a file in a third-party app, MTC checks to see if a local cached copy exists and is fresh. If the file is not in cache or is stale, the file is downloaded from the server and then a copy of the file is passed to the third-party app. Once the user is done making changes in the third-party app (assuming the app can edit that file type) the user would then select the "Open In" or equivalent function in the third-party app and choose MTC as the destination. Files copied back into MTC are placed in the MTC offline vault. Back in MTC, the user can select files in their vault and upload those to EFT, effectively overwriting the original file. The download, open in third-party app, open back in MTC, then upload, are all separate operations.
-
On Android devices, MTC takes on a more active role for file editing. When the user downloads the file, selects the Open In function, and then selects a third-party app, MTC passes a handle to the originally downloaded (and cached) file, rather than a copy of the same. MTC then spawns a file monitoring thread to keep track of changes (saves) made to that file. The user makes their edits in the third-party app, and after saving their changes, they must switch back to the MTC app. Once MTC is in the foreground, it cancels the monitoring thread. If changes were recorded, it immediately uploads the file to the server, overwriting the original file.
Does MTC work with any Mobile Device Management (MDM) technology?
Yes, as long as the MDM solution you have in place provides app management capabilities—meaning the MDM solution can distribute apps curated from the app store. Keep in mind that MDM-managed devices require enrollment, which might be enforceable within the organization, but rarely so for partners, customers, or other non-employees who still need to interact with your organization. The good news is that MTC has its own MDM capabilities via EFT policy controls, removing the need to rely on third-party MDM solutions, unless otherwise desired.
Does MTC leverage Good Technology, Mobile Iron, or similar MDM app wrapping or containerization technology?
No, MTC does not rely on any third-party MDM wrappers or SDKs because MTC provides its own MDM capabilities via EFT policy controls. These policy controls provide the same containerization benefits as one of the commercial MDM solutions but without the added cost or complexity. EFT’s centrally managed policies control intra-app workflow, password storage and complexity rules, and data storage rules, while ensuring encrypted storage and transmission of data—all without having to force your users (which might not be direct employees of the organization) to adopt an MDM-specific version of the application on their device.
Can EFT's security policies for MTC be set per-user?
Security policies must be set on EFT Site-wide, affecting all templates and users belonging to that Site. If you need a separate set of policies for certain users, then you could set up a second Site (on a different IP address or port). Please contact Globalscape if you feel that you need template-level or user-level control over MTC‘s security policies, so we can determine whether to extend more granular control over those policies in a future version release.
Can the security policy for blocking MTC from opening files be specific to certain file types?
When Open In is disallowed, it will affect all files, regardless of extension.