Description
Decrypts one or more previously encrypted files. Supports decrypting any cipher file, provided the file was encrypted using one of the supported types and algorithms (not limited to files encrypted by Automated Workflow).
Supports both symmetric (passphrase) and asymmetric (public/private key) modes. Standard support for a broad range of algorithms: Rijndael, DES, RC2, and TripleDES.
If PGP is installed, the actions can optionally use the PGP engine for both passphrase and public/private key encryption and support for the following algorithms: IDEA, 3DES, CAST5, Blowfish, AES128, AES192, AES256, and Twofish256.
Supports Automated Workflow file masking and filtering.
Declaration
<AMDECRYPT ENCRYPTTYPE="Text[options]" INPUTFILE="Text" OUTPUTFILE="Text" SUBFOLDERS="YES/NO" KEEPFOLDERSTRUCT="YES/NO" OVERWRITE="YES/NO" ISNEWER="YES/NO" ONLYIFEXIST="YES/NO" OVERWRITEREADONLY="YES/NO" OVERWRITEHIDDEN="YES/NO" ARCHIVETURNOFF="YES/NO" EXCLUDE="Text" RE="YES/NO" ISNEWERTHAN="Date" ISOLDERTHAN="Date" ATTRFILTER="Text" ENCRYPTALGO="Text[Option]" PASSWORD="Text" PRIVATEKEY="Text" />
Example
<AMDECRYPT ENCRYPTTYPE="KEY" INPUTFILE="C:\Test\encr*.doc" OUTPUTFILE="C:\Test\decr*.doc" SUBFOLDERS="YES" KEEPFOLDERSTRUCT="YES" OVERWRITE="YES" ISNEWER="YES" ONLYIFEXIST="YES" ARCHIVETURNOFF="YES" EXCLUDE="*pri" ISNEWERTHAN="%DateSerial(2007,02,01)+TimeSerial(16,58,42)%" ISOLDERTHAN="%DateSerial(2007,02,15)+TimeSerial(16,58,42)%" ATTRFILTER="+r-e" PRIVATEKEY="C:\Test\NewPriKey.pri" />
General Tab Parameters
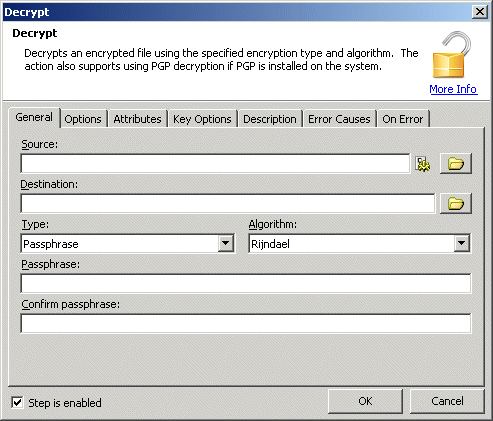
Source: Specifies the path and file names for the files to decrypt. Wildcard characters asterisk (*) and question mark (?) can be used to decrypt files matching a certain mask.
Text, Required
MARKUP:
a) INPUTFILE="c:\sourcefoldername\file.txt"
b) INPUTFILE="c:\sourcefoldername\*.txt"
Destination: Specifies the destination folder and (optional) filename for the files being decrypted. Folders that do not exist will be automatically created at runtime.
Text, Required
MARKUP:
a) OUTPUTFILE="c:\destinationfoldername\file.txt"
b) OUTPUTFILE="c:\destinationfoldername\
c) OUTPUTFILE="c:\destfolder\newdestfolder\*.txt"
Type: Specifies the type of encryption used to encrypt the files. The available options are:
(Default): Passphrase. A passphrase must be entered to decrypt.
KEY: Public/Private Key. A private key must be used to decrypt.
PGPPASSPHRASE: PGP Passphrase. A PGP passphrase must be entered to decrypt.
PGPKEY: PGP Public/Private Key. A PGP private key must be used to decrypt.
Text, Optional - Default "passphrase"
MARKUP: ENCRYPTTYPE="KEY"
Algorithm: Specifies the algorithm used in the encryption. Active only if Type parameter [ENCRYPTTYPE] is set to Passphrase (default) or PGP Passphrase.
Options for Passphrase are:
Rijndael
DES
RC2
TripleDES
Options for PGP Passphrase are:
IDEA
3DES
CAST5
Blowfish
AES128
AES192
AES256
Twofish256
Text, Optional - Default "Rijndael"
MARKUP: ENCRYPTALGO="DES"
Passphrase: Specifies the passphrase needed to decrypt the file.
Text, Required if decryption Type is Passphrase
MARKUP: PASSWORD="g9tc745yuig3j9t"
Options Tab Parameters
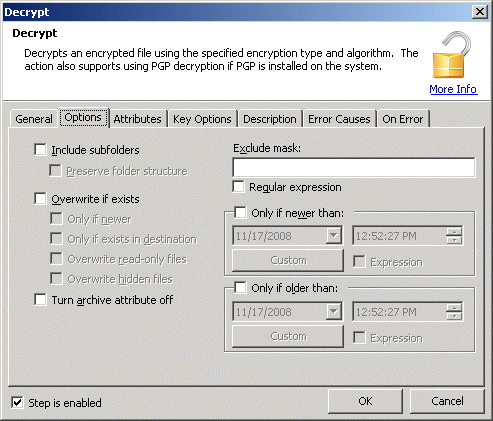
Include Subfolders: When set to YES (selected), specifies that, if present, subfolders should be searched for files matching the mask specified in the Source [INPUTFILE] parameter.
Yes/No, Optional default - NO
MARKUP: SUBFOLDERS="YES"
Preserve Folder Structure: Valid only if the "Include subfolder" [SUBFOLDERS] parameter is YES. When set to YES (selected), specifies that subfolders found in the source folder should be created in the destination folder, and source files should be decrypted into their respective folders rather than directly into the root of the target folder specified in the "Destination" [OUTPUTFILE] parameter. If the "Include subfolders" [SUBFOLDERS] parameter is set to NO this parameter is ignored.
Yes/No, Optional default - YES
MARKUP: KEEPFOLDERSTRUCT="NO"
Overwrite if Exists: When set to YES (selected), specifies that, if destination files already exist, they should be overwritten.
Yes/No, Optional default - NO
MARKUP: OVERWRITE="YES"
Only if Newer: Valid only if the "Overwrite if exists" [OVERWRITE] parameter is YES. When set to YES (selected), specifies that only files that are newer than those in the destination folders will overwrite existing files.
Yes/No, Optional default - NO
MARKUP: ISNEWERTHAN="YES"
Only if Exists in Destination: Valid only if the "Overwrite if exists" [OVERWRITE] parameter is YES. When set to YES (selected), specifies that only files that already exist in the destination will be decrypted from the source. All other files, regardless of whether they match the mask or other parameter settings will be bypassed.
Yes/No, Optional default - NO
MARKUP: ONLYIFEXIST="YES"
Overwrite Read-Only Files: Valid only if the "Overwrite if exists" [OVERWRITE] parameter is YES. When set to YES (selected), specifies that already existing files should be overwritten even if the file in the destination is marked with the "read-only" attribute. By default, read only files are not overwritten.
Yes/No, Optional default - NO
MARKUP: OVERWRITEREADONLY="YES"
Overwrite Hidden Files: Valid only if the "Overwrite if exists" [OVERWRITE] parameter is YES. When set to YES (selected), specifies that already existing files should be overwritten even if the file in the destination is marked with the "hidden" attribute. By default, hidden files are bypassed.
Yes/No, Optional default - NO
MARKUP: OVERWRITEHIDDEN="YES"
Turn Archive Attribute
Off: When set to YES (selected), specifies that the "archive"
attribute of the source files should be switched OFF. The Windows "archive"
attribute is generally used to track whether a file has been backed-up
by turning the source file's archive attribute off
Yes/No, Optional default - NO
MARKUP: ARCHIVETURNOFF="YES"
Exclude Mask: Causes the action to not decrypt files matching the masks specified. Filenames or wildcard masks may be used. Multiple entries may be specified by separating them with a pipe symbol (|), for example, *.txt|*.bak
Text, Optional default - (blank)
MARKUP: EXCLUDE="*.txt"
Regular Expression: If set to YES, specifies that a regular expression is used in the Exclude Mask [EXCLUDE] field.
Yes/No, Optional default - NO
MARKUP: RE="YES"
Only if Newer Than: Causes the action to only decrypt files if the source is newer than the date/time specified. If parameter is left blank or not included, the date of the files will be ignored (excluding "Only if newer" [ISNEWER] parameter).
date, Optional default - (none)
MARKUP: ISNEWERTHAN="%DateSerial(2007,10,12) + TimeSerial(00,00,00)%"
Only if Older Than: Causes the action to only decrypt files if the source is older than the date/time specified. If parameter is left blank or not included, the date of the files will be ignored (excluding "Only if newer" [ISNEWER] parameter).
date, Optional default - (none)
MARKUP: ISOLDERTHAN="%DateSerial(2007,10,12) + TimeSerial(00,00,00)%"
Attributes Tab Parameters
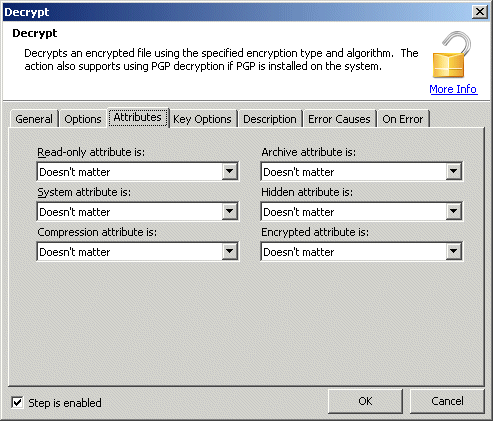
Attributes: This group of settings causes the action to filter which files are decrypted based on the attribute settings of the source files. In visual mode, a group of controls are provided to assist in the selection of this parameter. In markup mode, a single text item must be specified that contains the attributes of the files you wish to decrypt.
Available Options:
R - Read only: Specifying "+R" causes files with this attribute turned on to be included, "-R" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
A - Archive: Specifying "+A" causes files with this attribute turned on to be included, "-A" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
S - System: Specifying "+S" causes files with this attribute turned on to be included, "-S" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
H - Hidden: Specifying "+H" causes files with this attribute turned on to be included, "-H" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
C - Compression: Specifying "+C" causes files with this attribute turned on to be included, "-C" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
E - Encrypted: Specifying "+E" causes files with this attribute turned on to be included, "-E" causes files with this attribute turned off to be included, not specifying the letter (default) causes this attribute to be ignored.
Text, Optional (blank)
MARKUP:
ATTRFILTER="+R+A-S-H" (decrypt read-only and archive files, not
System or Hidden)
ATTRFILTER="-S" (do not decrypt "System" files)
Key Options Tab Parameters
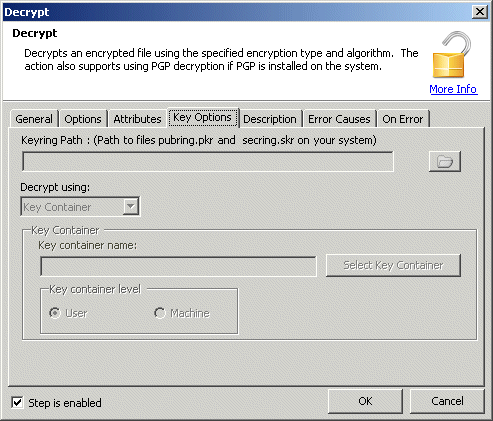
Key Path: Specifies the path and file name of the private key file to be used to decrypt the file.
Text, Required if decryption Type is Public/Private Key
MARKUP: PRIVATEKEY="C:\Foldername\PrivateKey.pri"
Key container name: Allows you to enter the name of the key container to identify which private or public key to use.
Text, Required
MarkUp: KEYCONTAINERNAME="Automated Workflow"
Key Container Level: Specifies whether the keys are stored in key container user or machine.
User-level RSA key containers are stored with the Windows user profile for a particular user and can be used to encrypt and decrypt information for applications that run under that specific user identity. User-level RSA key containers can be useful if you want to ensure that the RSA key information is removed when the Windows user profile is removed. However, because you must be logged in with the specific user account that makes use of the user-level RSA key container in order to encrypt or decrypt protected configuration sections, they are inconvenient to use.
Machine-level RSA key containers are available to all users that can log in to a computer, by default, and are the most useful as you can use them to encrypt or decrypt protected configuration sections while logged in with an administrator account. A machine-level RSA key container can be used to protect information for a single application, all the applications on a server, or a group of applications on a server that run under the same user identity. Although machine-level RSA key containers are available to all users, they can be secured with NTFS Access Control Lists (ACLs) so that only required users can access them.
Text [Options], optional default is "USER"
MarkUp: KEYCONTAINERLEVEL="MACHINE"
For more information, refer to http://msdn2.microsoft.com/en-us/library/f5cs0acs.aspx.