Auditing Administrator Changes to the ARM Database
(Requires Advanced Security Module in addition to ARM) Administrators often need to know when and what changes were made to EFT and who made them. The Administrator Actions Log report provides information about administrator changes.
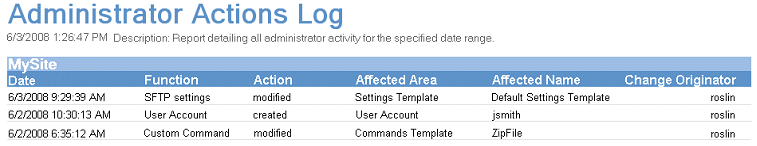
EFT logs the following changes made to EFT to the ARM database:
-
The Date the action occurred, in MM/DD/YYYY HH:MM:SS format.
-
The affected feature or Function. (Refer to Functions Audited below.)
-
The type of Action (created, added, removed, modified, enabled, disabled, started, and stopped).
-
The Affected Area (Server, Site, Settings Template, User Account, Event Rule, Command, Group, VFS, Report).
-
The name of the affected object, Affected Name (Server Name, Site Name, Settings Template Name, User or Admin Account Name, Event Rule Name, Command Name, Group Name, Folder Name, Report Name).
-
The name of the administrator that made the change, Change Originator.
The data in the preconfigured report is arranged in columns, Date, Function, Action, Affected Area, Affected Name, and Change Originator, grouped by Site name, and sorted in reverse chronological order (newest change at the top).
Functions Audited
When the following functions are created, added, removed, modified, enabled, disabled, started, or stopped, the action is logged to the database. Many possible actions are grouped together. For example, modifying SSL cipher selection, changing SSL clear command channel values, or modifying SSL connection string all fall under "SSL settings." Also, intermediate states are not audited (e.g., a toggle was checked, but later unchecked, rendering the transaction moot). Instead, only committed states are captured (once the administrator applies changes).
|
|
|