Remote Agent Logging
On the EFT server, remote Agent events can be tracked in the EFT.log file on EFT. By default, the Remote Agent log is commented out in logging.cfg.
On the Remote Agent's computer, there is also a file named agent.log that contains updates, errors, event rules it has received, and so on.
To enable logging of Remote Agent events
-
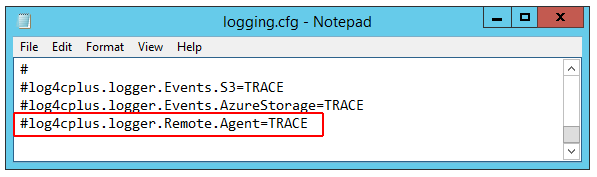
On the EFT server computer, open C:\ProgramData\Globalscape\EFT Server Enterprise\logging. cfg in a text editor.
-
Scroll to the very bottom, to
#log4cplus.logger.Remote.Agent=TRACE and remove the POUND SIGN #
TRACE level should be sufficient.
The EFT.log file entries will look something like this:
09-07-17 17:07:24,071 [2520] INFO Remote.Agent <> - Template Template (1) added by admin
09-07-17 17:14:59,634 [2520] INFO Remote.Agent <> - Template Template (2) added by admin
09-12-17 16:02:39,094 [2524] INFO Remote.Agent <HTTP.ProcessRequest> - Processing agent initial enrollment request.
09-12-17 16:02:39,203 [2524] INFO Remote.Agent <HTTP.ProcessRequest> - Agent ag_NUCQT7MG9OH auto-enrolled.
Remote Agent activity also appears in the server log file, e.g., C:\ProgramData\Globalscape\EFT Server Enterprise\Logs\u_ex170912.log:
2017-09-12 21:02:39 192.168.64.141 - - [1]POST /boe/v1/enrollments - 200 345 813 - 443
2017-09-12 21:02:39 192.168.64.141 - - [2]POST /boe/v1/enrollments/6d01ab2a-f523-4eb1-8b53-d8c608b128b0 - 200 6178 292 - 443
2017-09-12 21:02:39 192.168.64.141 - - [3]POST /boe/v1/agents/6d01ab2a-f523-4eb1-8b53-d8c608b128b0 - 401 313 216 - 443
2017-09-12 21:02:39 192.168.64.141 - ag_NUCQT7MG9OH [4]user ag_NUCQT7MG9OH - 331 - - - 443
2017-09-12 21:02:39 192.168.64.141 - ag_NUCQT7MG9OH [4]pass ****** - 200 - - - 443
2017-09-12 21:02:39 192.168.64.141 - ag_NUCQT7MG9OH [4]POST /boe/v1/agents/6d01ab2a-f523-4eb1-8b53-d8c608b128b0 - 200 3230 299 - 443
2017-09-12 21:02:39 192.168.64.141 - - [5]POST /boe/v1/agents/6d01ab2a-f523-4eb1-8b53-d8c608b128b0 - 401 313 216 - 443
2017-09-12 21:02:40 192.168.64.141 - ag_NUCQT7MG9OH [6]user ag_NUCQT7MG9OH - 331 - - - 443
2017-09-12 21:02:40 192.168.64.141 - ag_NUCQT7MG9OH [6]pass ****** - 200 - - - 443
2017-09-12 21:02:40 192.168.64.141 - ag_NUCQT7MG9OH [6]POST /boe/v1/agents/6d01ab2a-f523-4eb1-8b53-d8c608b128b0 - 200 3230 308 - 443
The Remote Agent computer also has logs in C:\ProgramData\Globalscape\EFT Remote Agent\. Trace-level logging must be enabled in agentlogging.cfg. An administrator can remote access the RAM computer and use a utility such as Baretail to actively monitor what the agent is doing.
C:\ProgramData\Globalscape\EFT Remote Agent\Agent.log
C:\ProgramData\Globalscape\EFT Remote Agent\agentlogging.cfg
More logging on specific transfers in the following directory (similar to how EFT does it by default): C:\ProgramData\Globalscape\EFT Remote Agent\logs\