Creating a Remote Connection
After you have configured a local connection to EFT, you can create a remote connection.
To create a remote EFT administrator connection
-
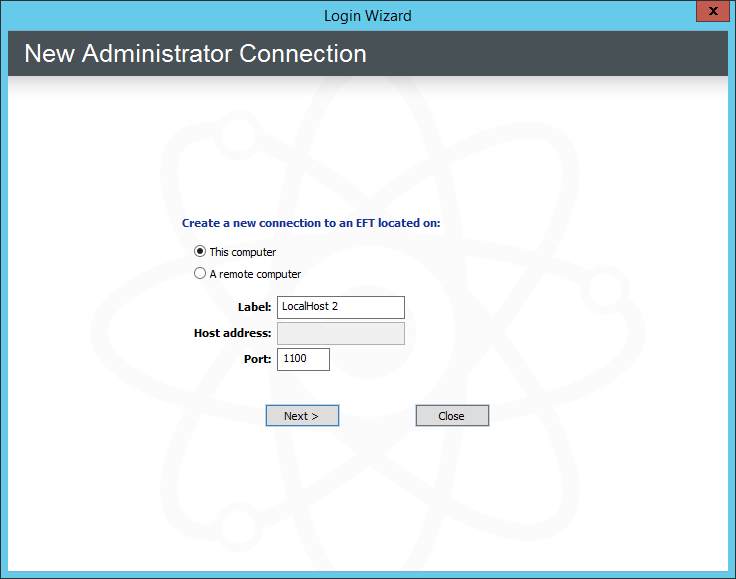
On the main menu click File >New Server. The New administrator Connection page appears.
-
Be sure that the remote Server service is running, and that it allows remote administration. Then:
-
Click A remote computer.
-
In the Label box, provide a name for the remote Server.
-
In the Host address box, provide the IP address at which the remote Server allows connections.
-
In the Port box, provide the port through which the remote Server allows connections.
-
-
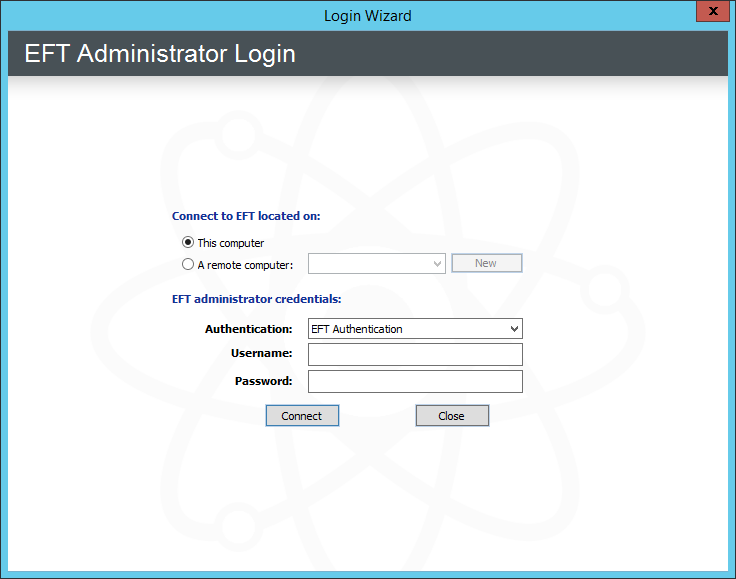
Click Next. The Login page appears.
-
Click the Authentication box and specify the type of authentication to use for this login. Future connections will default to the authentication type that you specify during this initial login, but you can choose a different type. Authentication types include:
-
EFT Authentication - Choose this option to log in with an EFT-specified administrator account, such as the one you created during installation.
-
Integrated Windows Authentication - Choose this option to log in as the currently logged on user (Integrated Windows Authentication). Requires the Advanced Security Module (ASM).
-
Windows Authentication - Choose this option to log in using a specific Windows account. Requires the Advanced Security Module (ASM).
-
If you specified EFT Server Authentication or Windows Authentication, in the Username and Password boxes, provide the login credentials that you created during installation. The Welcome page appears. Because you have not yet activated the software, the "Free Trial" reminders appear. After you activate, you will not see this prompt.
-
Do one of the following:
-
If you are evaluating the software or just do not want to activate yet, click Start Trial, then follow the procedures in Configuring EFT.
-
If you have purchased a license, click Activate Now, then follow the procedures for activating the software.
-
Click Next. The Server Setup wizard Welcome page appears.
-
If you are restoring from a backup, click Restore from Backup, then refer to Backing Up or Restoring Server Configuration for the procedure. Otherwise, continue to the next step.
-
If you are not restoring from a backup (EFT Enterprise only), click Next. The FIPS Options page appears.
-
To use FIPS for SFTP (SSH2), select the Enable FIPS for SFTP check box.
-
To use FIPS for SSL, select the Enable FIPS for SSL check box.
-
A confirmation prompt appears when you select either check box. When you enable FIPS, the EFT service must be restarted. Click OK to continue with FIPS enabled or click Cancel if you do not want to use FIPS and restart the EFT service.
-
Click Next. The Remote administration page appears.
-
Because you are configuring a remote administrator connection, ensure that the Allow remote administration check box is selected.
-
Specify the Listening IPs.
-
Click Configure to specify one or more IP addresses. The Listening IP Settings dialog box appears.
-
All Incoming (IPv4) is selected by default. Select the check boxes for addresses that you want to allow; clear the check boxes for the addresses that you do not want to allow, and then click OK.
-
Specify the Listening port. (For security best practices and compliance with the PCI DSS, specify a port other than the default of 1100.)
-
Click Next. The Secure Remote administration page appears.
-
administrator account credentials are transmitted in plaintext unless SSL is enabled. Organizations complying with the PCI DSS are required to use SSL for remote administration. To enable secure remote administration, select the Use SSL for secure remote administration check box, and then click Next. The SSL Certificate Options page appears.
-
Do one of the following:
-
In the Certificate and Private Key boxes, click the folder icon
 to browse for the private
key pair files.
to browse for the private
key pair files. -
Click Create certificate to create one. Refer to SSL Certificate-Based Login, Creating Certificates, Importing a Certificate into the Trusted Certificate Database for information regarding certificates.
-
If you are using Auditing and Reporting, select the Enable auditing check box, then provide the information required to connect to the ARM database as described below. If you are not using Auditing and Reporting, skip to the next step. (Auditing and reporting is a requirement of the PCI DSS.)
-
In the Database type area, specify whether you are using SQL Server or Oracle for the auditing database. (Oracle available in EFT Enterprise only.)
-
In the Host[\Instance Name] box, type EFT name or IP address.
-
In the Authentication box, specify the type of authentication used by the database, either Windows Authentication or SQL Server Authentication.
-
If you choose SQL Server Authentication, you must also specify the "sa" username and password. In the Username and Password boxes, type the username and password used to connect to the database (not the EFT credentials).
-
In the Database Name box, type the name of the database.
-
In the Audit failure notification email address box, type the email address to which EFT is to send database connection error notifications. You can add as many email addresses as needed; separate the addresses with a comma or semicolon. EFT uses its global SMTP email settings from the SMTP Configuration to send the emails. You will configure those settings on the next page.
-
In the In case of audit database error area, specify an Action for EFT to take if there is an error with the database. To stop recording data, select Stop auditing. To continue recording data to a file, select Audit to folder, and specify the location for the log file.
-
In the From email address box, specify the email address for email notifications (such as those triggered by Event Rules). This is the address that appears in the From box of emails sent by EFT. For example, type noreply@serverhost.com.
-
The email address is validated when you click OK. If the email address contains invalid characters or does not contain the @, an error message appears. Click OK to dismiss the error message, then correct the address.
-
In the SMTP host address boxes, specify the SMTP server host address and port.
-
If the Use SMTP server authentication, select the check box and provide the Username and Password.
-
Click Next. Server Setup is complete.
-
Click an option, then click Finish. If you chose FIPS mode for SSL and/or SSH, prompts appear explaining that EFT has entered FIPS mode. Click OK to dismiss the prompts.
-
If you chose Run the Site Setup wizard now, the Site Setup wizard Welcome page appears.
-
Refer to Creating a Site for the procedure for configuring the Site. The procedure differs depending on the user authentication type you choose.
When you enable FIPS mode, the ciphers, keys, and hash lengths and types that are not FIPS approved are not available. If a FIPS-approved state cannot be achieved when FIPS is enabled, the EFT service is stopped and an error is written to the Windows Event Log.

If you are using SQL Server as the Auditing Database, \InstanceName corresponds to SQL Server's notion of named instances, a feature that allows a given computer to run multiple instances of the SQL Server Database Service. For more information, refer to http://msdn2.microsoft.com/en-us/library/ms165614.aspx
UNC paths are supported. The Globalscape Server service must run on a computer that has access to the network share, and the full UNC path must be used, that is: \\xcvd.forest.intranet.xc\Common_Files, not G:\Common.
You are offered the option of continuing to the Site Setup wizard, or quitting the wizard, saving EFT settings, and configuring the Site(s) later. You must configure at least one Site to service inbound connections to EFT.
Related Topics