Specifying File Deletion Options
EFT's security modules provide a data sanitization/data wiping option. If you do not activate the module, this feature is disabled after the trial expires.
You can configure EFT to securely delete or purge a file by writing over the initial data using encrypted and/or pseudorandom data. A menu of purging methods is available; available options depend on the library used.
-
The 3-pass DoD method overwrites all addressable locations with a character and its complement, then a random character, and does this three times.
-
The pseudorandom data wiping method does the following:
-
Initializes the wincrypt library
-
Fills the file with randomly generated data from the wincrypt library
-
Flushes the data to disk
-
Deletes the file from file system calling the standard function DeleteFile()
*.pgp files are automatically excluded from the wipe process. When wipe is enabled, ANY delete operation also includes the wipe (sanitization) process.
To specify a delete method
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Site that you want to configure.
-
In the right pane, click the Security tab.
-
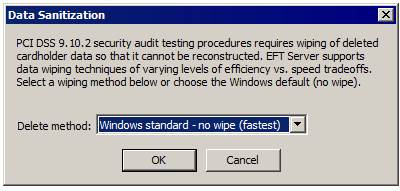
In the Data Security area, next to Secure data removal, click Configure. The Data Sanitation dialog box appears.
-
In the Delete method box, click the list to specify one of the following methods:
-
Windows standard (fastest)
-
Pseudorandom data (medium)
-
3-pass DoD 5220.22-m (slow)
-
-
Click OK to close the dialog box.
-
Click Apply to save the changes on EFT.
-
A message appears when the purging mechanism is changed to anything other than the Windows standard delete method.
For further reference regarding data wiping, see the following articles:
(These links are outside of Globalscape's domain and could change.)
-
Data remanence:http://en.wikipedia.org/wiki/Data_remanence,
specifically the section titled "Standard Patterns for Purging": http://en.wikipedia.org/wiki/Data_remanence#Standard_patterns_for_purging -
US DoD 5220.22-M Standard, defined in the US National Industrial Security Program Operating Manual of the US Department of Defense: http://en.wikipedia.org/wiki/National_Industrial_Security_Program
-
"Secure Deletion of Data from Magnetic and Solid-State Memory": http://www.usenix.org/publications/library/proceedings/sec96/full_papers/gutmann/