Descriptions of Preconfigured Reports
The Auditing and Reporting module comes with a number of preconfigured reports that allow you to start analyzing data right away. The report templates are .xml files and are installed in %systemdrive%\ProgramData\Globalscape\EFT Server\Reports. If you plan to edit the default templates, it is a good idea to save a backup of them first. You can use these reports as is, or as templates to create your own custom reports.
The preconfigured reports described below are provided with the Auditing and Reporting module. You can run the reports as is or edit them to suit your specific needs.
-
Activity - AS2 Transfers (Detailed) - A verbose AS2 file transfer report that provides the information necessary for troubleshooting problem transactions.
-
Activity - AS2 Transfers (Summary) - A transaction report that displays the same information as shown on the Transfers - AS2 node. The report queries all AS2 transactions for the dates specified, grouped by site, sorted by date, and listed in reverse chronological order.
-
Activity - by Permissions Group - This report displays the various Actions performed by all the groups, such as administrator, All users, and Guests, and it displays Date/Time, Remote IP address, protocol, Action, filename, folder, KB transferred, and the result.
-
Activity - by Users (Detailed) - This report displays all folders and files created and the delete activity for all users who logged on to EFT during a particular period, grouped by username, and sorted in reverse chronological order. The report includes the time stamp, remote IP address of the user, protocol, Action, file name, folder, KB transferred, and the result.
-
Activity - by Users (Summary) - This report displays the transfer activity (total number of uploads and downloads) for all users who logged on to EFT during the date range specified, grouped by username, subgrouped by date, sorted by username, then transfer direction, and date, in ascending order.
-
Activity - File Scanned Data Results - This report displays all scanned data results.
-
Activity - File Transfers as Client - This report displays all file transfers initiated by EFT.
-
Activity - File Transfers as Server - This report displays all transfers initiated by remote clients.
-
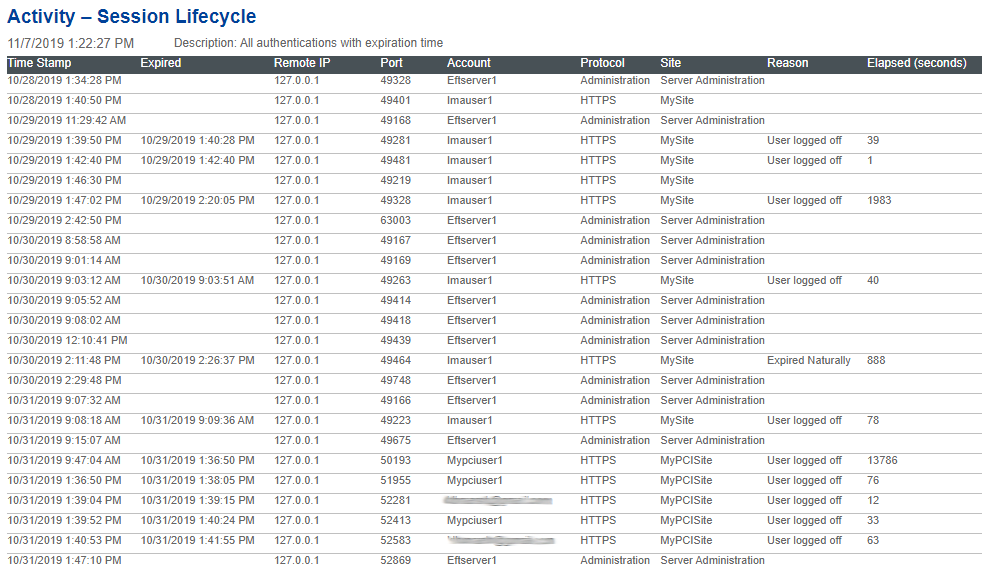
Activity - Session Lifecycle - This report displays authentications and session expired time. (NOTE: If an EFT user connects to EFT using CuteFTP over HTTPS and uploads several files, the report does not include data in the Expired (logout time), Reason, or Elapsed columns.)
-
Admin - Audit Log - This report displays a summary of all EFT administrator activity for the specified date range.
-
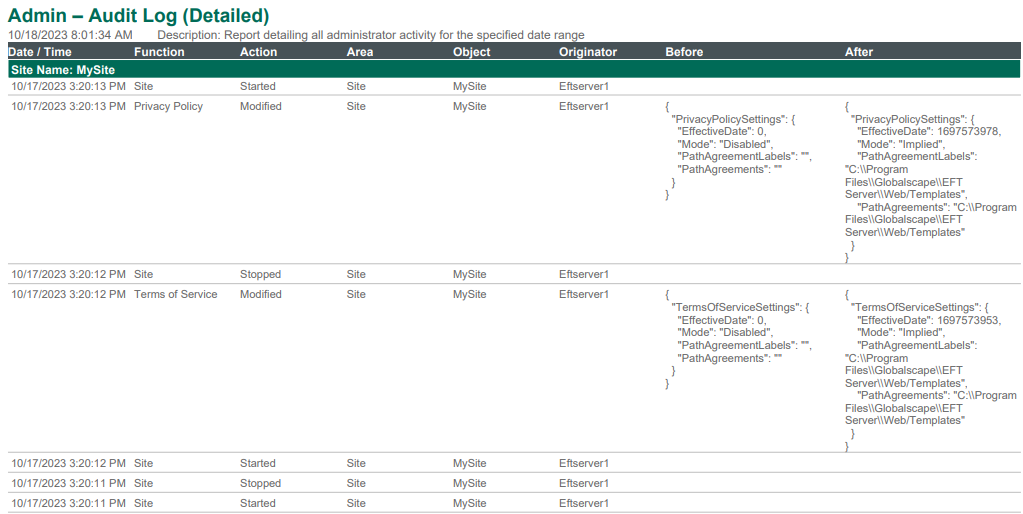
Admin - Audit Log (Detailed) - This report displays all EFT administrator activity for the specified data range, with Before and After details.
-
Admin - Authentications - This report shows administrator connections (success and failures) to the this EFT for the give date range.
-
Content Integrity Control - A report showing all Event Rules with CIC actions, grouped by site name, sub-grouped by the user-defined event name, sorted by the unique event ID (not shown) in descending order. Includes Parameters, Begin and End Date\ Time, and Result.
-
Event Rules - by Trigger Name (Summary) - This report summarizes all Event Rules with their corresponding Actions, grouped by Site name, subgrouped by the user-defined Event name, sorted by the unique Event ID (not shown in report) in descending order.
-
Event Rules - by Trigger Type (Detailed) - This report displays the Event Rule activity by user-defined Event name, grouped by Site name, subgrouped by the Event type, sorted by date in reverse chronological order.
-
Event Rules - by Trigger Type (Summary) - This report summarizes the Event Rule activity by user-defined Event name, grouped by Site name, sub-grouped by the Event type, sorted by date in reverse chronological order.
-
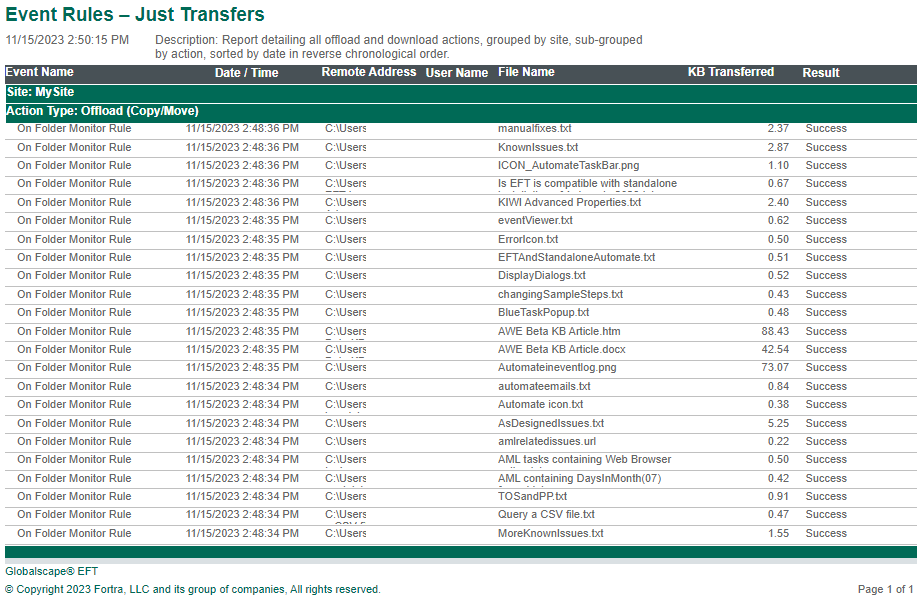
Event Rules - Just Transfers - This report details all offload and download Actions, grouped by Site subgrouped by Action, sorted by date in reverse chronological order.
-
Executive Summary Report - This report summarizes the following information for the period specified:
-
Average transfer speed
-
Total number of downloads, uploads
-
Total bytes transferred (inbound/ outbound)
-
Top 5 users (by # of connections)
-
Top 5 users (by bytes transferred)
-
Privacy - Admin Changes to Personal Data - This report details changes to personal data fields, organized by date/ time, Site, Template, Account, Field changed, and Before and After changes.
-
Privacy - Terms and EU Status Changes - This report details privacy terms and EU status changes organized by date/ time, Site, Template, Account, IP address, Right Exercised, and Reason a user exercised their privacy rights.
-
Privacy - User Rights Exercised - This report details date/ time, Site, Template, Account, IP address, Right Exercised, and Reason a user exercised their privacy rights. (See examples in Privacy Reports.)
-
Traffic - Average Transfer Rates by User - This report displays the average transfer rate for specific users, grouped by username, subgrouped by date, sorted by username, transfer direction, and date, in descending order.
-
Traffic - Connections Summary - This report details connections to EFT (IP address or user connections) and bytes transferred by date, grouped by Site name, sorted by date in reverse chronological order.
-
Traffic - Datewise - hourly Bytes Transferred - This report details the connections and bytes transferred sorted by date and hour, in chronological order.
-
Traffic - Datewise - IPwise bytes transferred - This report displays the connections established by remote IP addresses and total bytes transferred.
-
Traffic - IPwise Connections (Summary) - This report displays the connections established by remote IP addresses and total bytes transferred.
-
Traffic - Monthwise-IPwise Bytes transferred - This report displays the connections established by various remote IP addresses each month. It displays the Site name, month name, remote IP address, connections, and total bytes transferred.
-
Traffic - Most Active IPs - Connections - This report displays the most active IP addresses; that is, the IP addresses of the users who frequently log on to EFT. It displays the data transferred, Site name, remote IP address, and bytes transferred. This report can be used to determine Denial of Service (DoS) attacks against EFT.
-
Traffic - Most Active IPs - Data Transferred - This report displays the IP addresses of users who log on to EFT frequently; the number of connections established by various users. It displays the information on the total bytes transferred, number of connections, remote IP address, and Site name.
-
Traffic - Most Active Users - Connections - This report displays the connections established by the most active users.
-
Traffic - Most Active Users - Data Transferred - This report displays the usernames of users who log on to EFT frequently, the number of connections established by various users, and number of bytes transferred.
-
Traffic - Protocolwise Connections (Summary) - This report displays the connections established by various users and the protocol used by the users to transfer the data, that is, whether the users have used FTP, HTTP, or any other protocol to upload or download the files.
-
Traffic - Sitewise - Hourly by User - This report displays the total number of connection established by various users on a particular Site each hour.
-
Troubleshooting - Event Rules Failures - This report displays failures related to the Event Rules.
-
Troubleshooting - Most Prolific Users - This report details users with the most log on attempts.
-
Troubleshooting - Negotiated SSH Ciphers - This report lists all negotiated SSH Ciphers organized by Time Stamp, Key Algorithm, Cipher, KEX, MAC, Compress Directory, Account, and Fingerprint (fingerprint is NULL for inbound connections).
-
Troubleshooting - Negotiated SSH Ciphers (Summary) - This report provides a summary of negotiated SSH Ciphers
-
Troubleshooting - Negotiated SSL Ciphers - This report list all negotiated SSL Ciphers, organized by Time Stamp, Protocol version, EncryptionCipher, KEX, Authentication, MAC, Directory Account
-
Troubleshooting - Negotiated SSL Ciphers (Summary) - This report a summary of SSL Ciphers used, organized by Protocol version, EncryptionCipher, KEX, Authentication, MAC, Directory, Account, Count
-
Troubleshooting - Operation Errors - This report displays protocol error codes and corresponding commands, sorted in reverse chronological order. The report includes the date and time the error occurred, remote IP address, protocol used, username, command, filename, virtual folder, and result (for example, transfer completed).
-
Troubleshooting - Socket Connection Errors(Inbound) - This report displays the number of connection errors occurred while connecting to a site. (Refer to Winsock Error Codes for a list of Socket ID error codes.)
-
Troubleshooting - Socket Connection Errors Summary (Inbound) - This report displays a summary of the number of connection errors occurred while connecting to a site.
-
Web Service- Invoke Event Rules (Detailed) - This report is used to view activity for invoking Event Rules through Web Service, grouped by username, and sorted by date in reverse chronological order.
-
Workspaces Files Picked Up - Shows shared Workspace files picked up, organized by Send Date, Sender Email, Recipient Email, File Name, File Size (KB), Subject, and Expires date.
-
Workspaces - Files Sent - This report lists Workspace files sent, organized by Send Date, Sender Email, Recipient Email, File Name, File Size (KB), Subject, and Expires date.
-
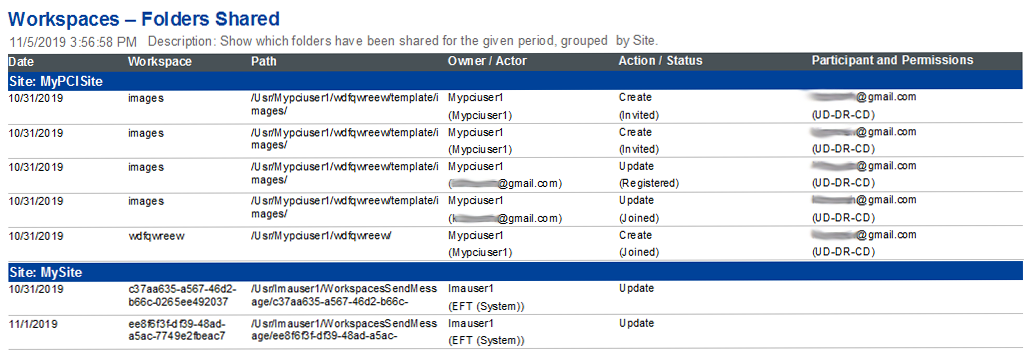
Workspaces - Folders Shared - This report shows which folders have been shared for the given period, grouped by Site, organized by Date, Workspace, Path, Owner/Actor, Action/Status, and Participant/Permissions.
-
Workspaces - Folders Unshared - This reports shows which folder shares of expired naturally or by their owner, organized by Date, Workspace, Path, Owner or Actor, Status, and Participant(s).