Prohibiting Password Reuse
You can configure EFT to remember a user account's previous passwords and not allow a user to submit a new password that is the same as any of the prior passwords for that account. You can set this at the Site, Settings Template, and user accounts.
On a high security-enabled Site, password history is enabled by default. If a user attempts to change a password to one of the specified number of passwords previously used for that account, EFT denies the password change request. The option is available at the Site, User Setting, and per user.
EFT validates any password change attempt for reuse (no special casing), whether via COM or the administrator, resulting in a prompt (in the administrator) or an error code (COM).
The password history is reset when transitioning from a non-PCI state to a PCI state. For example, if you disable this option, click Apply, then re-enable the option, and then click Apply again, the count is started over (the password history is discarded when the option is disabled.)
To enable enforcement of password history
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the Site, Settings Template, or user that you want to configure.
-
In the right pane, click the Security tab.
-
Select the Prohibit reuse of previous check box, then type the number of passwords to remember.
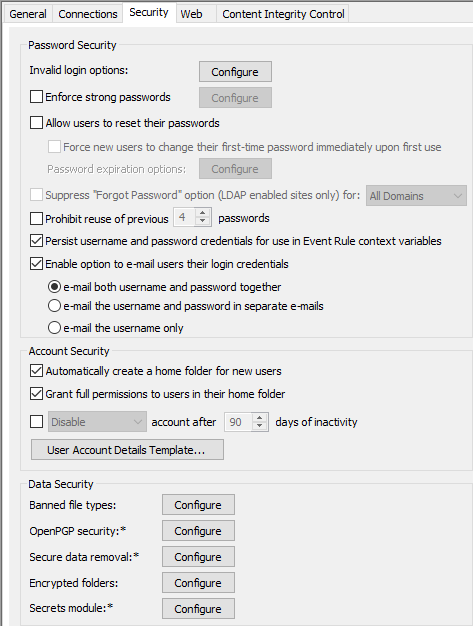
The number of iterations does not include the current password. For example, if you set password history to 4, and a password change attempt is made, EFT first determines whether the new password matches the current password, then evaluates whether the new password matches any of the previous 4 passwords.
-
Click Apply to save the changes on EFT.
Password Reuse Warnings
The following password-reuse violations cause warning messages to appear:
-
On a high security-enabled Site, if you disable enforcing password history, a warning message appears.
-
If enforcing password history is enabled and a password change request is made by the end-user (either by a user-initiated password reset or a forced reset), and the new password is the same as any of the specified number of previous passwords, EFT rejects the password change attempt. If a password change attempt over HTTP/S fails due to reuse, a warning message appears.
-
If a user logged in via FTP attempts to change the login password without being prompted (that is, not a forced reset), and the password fails due to reuse, EFT rejects the password change, but the user may continue the FTP session. If the change attempt was due to a forced reset (that is, require password change on initial login), the user will not be allowed to continue their session until a valid password is provided.
-
If a password change attempt over SFTP fails due to reuse, EFT rejects the change and prompts the user to resubmit a valid password. The user is not allowed to continue until a valid password is provided.
-
If a password change attempt in the administrator Login dialog box fails due to reuse, EFT rejects the change attempt, and a warning message appears.