Secure PNC Settings
After installing the DMZ Gateway, open gwconfig.xml in the root install folder with a text editor like Notepad. It should have the settings below for each DMZ Gateway profile.
SecurePNCEnabled – This can be set to “true” or “false” to either enable or disable the secure PNC feature. By default this is false. If set to “true” you will also need to at a minimum provide values for the PNCKeyStorePath, PNCStorePassphrase, PNCProtocols, and PNCCiphers. If these aren’t set, the DMZGatewayServer.log file should contain log entries explaining what is missing.
If the SecurePNCEnabled setting is set to true, then it also acts like a “require SSL” setting in that only secure peer notification channels will be allowed. In other words, whether or not a channel is to be secured is enforced by the server and not solely dictated by the client.
PNCKeyStorePath – The full path to a Java keystore file which contains the certificate and private key (pair) that the DMZ Gateway will use for the PNC. By default, this has no value.
PNCKeyStore path supports network locations, however, the DMZ Gateway server service needs to have access to the network share. In this example, the network share on \\192.168.100.143 has the administrator account with access to it.
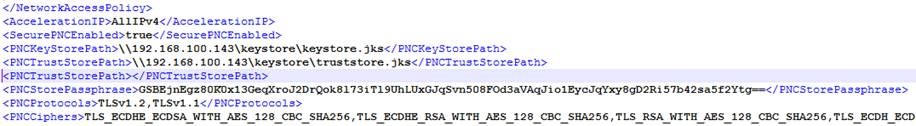
PNCTrustStorePath [Optional] – The full path to a Java keystore (that is, trust store) file which contains EFT’s certificate (just certificate, not private key) that is specified on the EFT Site-level Connections tab in the SSL Certificate Settings dialog box. If a path is provided, client certificate authentication is required, and therefore EFT’s certificate must exist in this keystore for the certificate to be trusted. If a path is not provided, then client certificate authentication is not required. By default, this has no value.
PNCStorePassphrase – This is that keystore passphrase for both the keystore and truststore mentioned above. You enter the password verbatim and then when the DMZ Gateway starts it will auto-encrypt the passphrase in the config file. By default, this has no value. PNCStorePassphrase is encoded to protect it from casual observance, but for added security it is recommended that you update the ACLs for the gwconfig.xml file to allow read and write access to only the account under which the DMZ Gateway service runs.
PNCProtocols – A comma separated list of protocols that the DMZ Gateway will allow for the secure PNC. This can take on the following values (by default set to TLSv1.2,TLSv1.1):
-
TLSv1.2
-
TLSv1.1
-
TLSv1
-
SSLv3 – This protocol is disabled by default by the JRE. To enable it you must update the java.security file under the install folder of the DMZ Gateway under “bin\jre1.8.0_74\lib\security” and remove SSLv3 from the line below:
-
jdk.tls.disabledAlgorithms=SSLv3, RC4, MD5withRSA…
-
SSLv2Hello
PNCCiphers – Comma-separated list of cipher suites that the DMZ Gateway supports. Defaults to a list of secure ciphers that are supported by Java 1.8. Refer to the “Default Enabled Cipher Suites” section of https://docs.oracle.com/javase/8/docs/technotes/guides/security/SunProviders.html, which shows what Java 8 supports by default irrespective of the default PNCCiphers list.
Per https://docs.oracle.com/javase/7/docs/technotes/guides/security/SunProviders.html#importlimits, Java, by default, limits the encryption strength (that is, maximum key size) for various algorithms due to import regulations in some countries. Therefore, to use stronger encryption like AES 256, you will need to deploy the JCE Unlimited Strength Jurisdiction Policy Files We aren’t enabling that by default so that we can make sure we also comply with these import restrictions.
Also, the SSLEngine JCE API doesn’t appear to support the cipher suite syntax such as "RSA+AES” or ! so the full cipher suite names must be specified.
Here is an example of the new config settings with sample values:
<SecurePNCEnabled>true</SecurePNCEnabled> <PNCKeyStorePath>C:\devel\certs\keystore.jks</PNCKeyStorePath> <PNCTrustStorePath>C:\devel\certs\truststore.jks</PNCTrustStorePath> <PNCStorePassphrase>GSBEvsavuSo9cA6OO18fS5B+ubI+zdoDBYTzMoA3vtDQiiA65hLnVLdRAwyIZStqezbpLnbsu3E1IOH5Fh1Hij9qjQ==</PNCStorePassphrase> <PNCProtocols>TLSv1.2,TLSv1.1,TLSv1</PNCProtocols> <PNCCiphers>TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256</PNCCiphers>