EFT Server Log File
The main log for EFT is the EFT<servername>.log in the EFT installation folder. (Not affected by the Server > Logs tab setting.) If you want to save EFT<servername>.log to a different location, change the reference at the bottom of the logging.cfg file to the location [AppDataPath] that you prefer:
log4cplus.appender.R.File=${AppDataPath}\EFT.log
The EFT <servername>.log files are configured in the logging.cfg file in C:\ProgramData\Globalscape\EFT Server. Refer to the logging.cfg file itself to see which loggers are available to be enabled.
There are 7 log levels: TRACE, DEBUG, INFO, WARN, ERROR, FATAL, and OFF. The levels are hierarchical in nature, so enabling a level enables all levels # to its right (that is, enabling INFO enables WARN, ERROR, and FATAL). Each logger's level can be set independently. Children inherit their parent's level unless explicitly set.
By default the system log level is set to INFO. This will log all INFO, WARN, ERROR, and FATAL log messages. Optionally, you may want to temporarily increase the verbosity of the logging while diagnosing behavior by changing the INFO level to TRACE or DEBUG. Be aware that enabling the TRACE or DEBUG level may have a significant performance impact on the system and may also cause log files to grow rapidly.
log4cplus.rootLogger=INFO, RootFileAppender
Domain-Level EFT Server Loggers
The logging.cfg file includes a list of more granular loggers. You may optionally enable a custom log level for a particular logger by removing the comment ('#') marker from the beginning of the line. This may be useful when you want to enable more verbose logging for only a particular area of functionality rather than changing the level for the root logger. Be aware that enabling the TRACE or DEBUG level may have a significant performance impact on the system and may also cause log files to grow rapidly. Be sure to comment out the custom log level when you are finished troubleshooting.
SFTP Logging
In the logging.cfg file, you can configure logging for SFTP transfers. In the ARM schema, the table tbl_NegotiatedCiphersSSH is associated with tbl_Authentications and tbl_Actions, which tracks the negotiated cipher set for successful SFTP client/server authentications.
-
Setting the following advanced properties to true will improve the log performance: EnableXferLog (enable transfer logs) and CloseFinishedItemLog (false = enabled/default. By default, successful logs are removed.)
-
You can see negotiated ciphers in the EFT client log files, for troubleshooting purposes.
To configure logging for SFTP transfers
-
Open logging.cfg in a text editor, such as Notepad.
-
Find this line:
#log4cplus.logger.SFTP=TRACE
-
Delete the # from the front of the line to enable the logger.
-
Leave as TRACE or change to DEBUG for troubleshooting.
If you change it to DEBUG, be sure to change it back to TRACE and/or add the # to the front to comment out (disable) that log to avoid creating unnecessarily large log files.
Note that there are differences in how the logs are displayed depending on whether you are using SFTP.DLL or SFTP2.DLL.
When using the SFTP2.dll, the logs at the KEX section are in ASCII format:
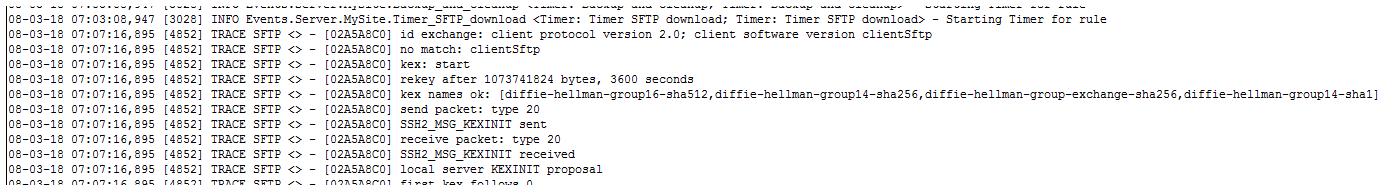
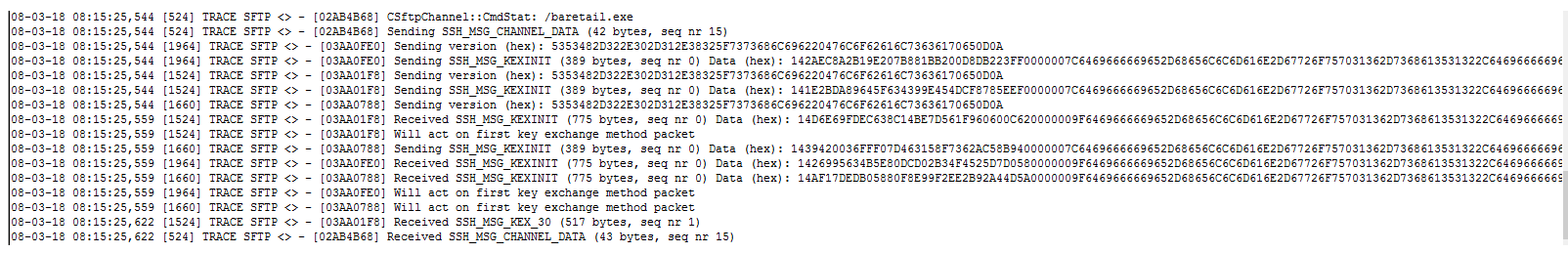
When using the legacy SFTP.dll, the KEX section is in HEX format:
SSL/TLS Logging
You can enable to SSL logging to track the details of successful SSL connections. In the ARM schema, the table tbl_NegotiatedCiphersSSL is associated with tbl_Authentications and tbl_Actions, which tracks the negotiated cipher set for successful SSL/TLS client/server authentications.
To track the details of successful SSL connections.
-
Open the logging.cfg file in a text editor such as Notepad.
-
Remove the comment next to #log4cplus.logger.SSL=TRACE, and change TRACE to DEBUG.
-
Remove the comment next to #log4cplus.logger.IPAccess=TRACE.
Example logs:
04-10-17 10:16:09,117 [16424] DEBUG IPAccess <> - Check IP address against IP Access Rules: IP: 127.0.0.1, access allowed
04-10-17 10:16:09,117 [7444] DEBUG SSL <> - SSL connection accepted; protocol version = TLSv1.2, cipher = ECDHE-RSA-AES128-GCM-SHA256, key length = 128
However, this adds more verbosity to the logs. Additionally, this does not track failed connections and puts the onus on the customer/administrator to pick apart the logs.
For failed connections made via SSL/TLS, the log entry should contain the following:
INFO SSL <> - SSL connection failed; ip address= ; connection ID=
For successful connections made using insecure ciphers via SSL/TLS, the log entry should contain the following:
WARN SSL <> - Insecure SSL connection accepted; protocol version=; cipher=; key length=; ip address=; connection ID=
For successful connections made using weak ciphers via SSL/TLS, the log entry should contain the following:
WARN SSL <> - Weak SSL connection accepted; protocol version=; cipher=; key length=; ip address=; connection ID=
SysLogAppender
You can add the SysLogAppender to EFT's logging.cfg file, found in ..\ProgramData\Globalscape\EFT Server (to send logging information to a security information and event management (SIEM) server, for example).
Add the following code snippet to the bottom of the file. Add comments to inform future users of its purpose.
log4cplus.rootLogger=TRACE, syslog
log4cplus.appender.syslog=log4cplus::SysLogAppender
log4cplus.appender.syslog.ident=syslog
log4cplus.appender.syslog.layout=log4cplus::PatternLayout log4cplus.appender.syslog.layout.
ConversionPattern=[%T] %-5p %b %x - %m%n
log4cplus.appender.syslog.host=pdc
log4cplus.appender.syslog.udp=true
log4cplus.appender.syslog.port=514
log4cplus.appender.syslog.facility=user-
Refer to https://kb.globalscape.com/KnowledgebaseArticle11033.aspx for details of configuring an advanced property to log all HTTP request headers.