EFS Encryption
Physical folders stored on the disk in EFT's Virtual File System (VFS) can be transparently encrypted during read/write using Microsoft's Encrypting File System (EFS) by which data is encrypted as it is written to disk, and decrypted prior to transmission.
-
Before you enable this feature, it is recommended that you set up appropriate backup measures to protect your data. If you need to recover a private key to decrypt data, and that key is lost, you will not be able to recover the data that the key protects. If you need more information on setting up appropriate backup procedures, refer to Configuration and Security Best Practices.
-
When EFT is running in HA mode and sharing a network resource, you must run the EFT server service with a Log On account that can access that shared network resource.
-
EFS is not available for systems running on FAT32 file systems. NTFS is required.
-
EFS is not available with NT authentication due to limitations of NT authentication. If you require this feature with an NT set up, LDAP authentication is recommended.
-
The PCI DSS requires that logical access and decryption keys be managed independently for disk-level encryption. If you enable this EFS for a high security-enabled Site, EFT prompts you to disable it, or continue with reason.
-
The PCI DSS requires that if EFT disk encryption is used (rather than file- or column-level database encryption), logical access must be managed independently of native operating system access control mechanisms (for example, by not using local system or Active Directory accounts). Decryption keys must not be tied to user accounts. That does not mean EFS cannot be used at all, but rather that it cannot be used as the sole mechanism for repository encryption. For this reason, the Server will only warn, rather than fail, during an audit.
-
If you have a large number of VFS folders and the interface becomes unresponsive when EFS is enabled, be sure to clear the EFS folder icon check box. Selecting the Enable EFS folder icons check box when you have a large number of VFS folders can cause the interface to become unresponsive while the server checks each one for encrypted contents.
-
You cannot have the folder open when trying to encrypt the folder in EFT.
To enable EFS encryption
-
In the administration interface, connect to EFT and click the VFS tab.
-
In the left pane, right-click the parent folder you want to configure, and then click Encrypt Contents.
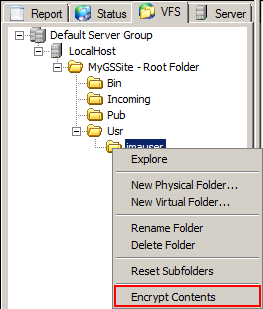
-
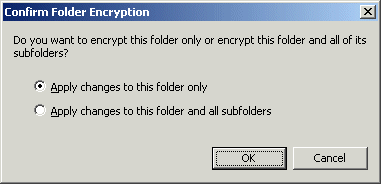
If the folder you selected has subfolders, a confirmation message appears.
-
Specify whether to Apply changes to this folder only or Apply changes to this folder and all subfolders, and then click OK.
-
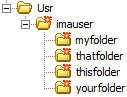
If the Enable EFS folder icons check box is selected, the encrypted folder and subfolders display a red asterisk to indicate that the folder contents are encrypted.
-
-
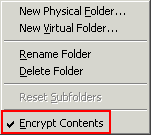
To remove encryption, right-click the encrypted folder and click Encrypt Contents to clear the check box.
-
If the folder you selected has subfolders, a confirmation message appears. Specify whether to Apply changes to this folder only or Apply changes to this folder and all subfolders, and then click OK.
When EFS is applied to a folder, you can configure the Server to add a red asterisk to the folder icon to indicate that the folder contents are encrypted. This setting is turned off by default. If you select the Enable EFS folder icons check box, the server will check each folder for encrypted contents before displaying the icon.
If you have thousands of folders, you should leave the check box unselected; selecting the check box when you have a large number of folders can cause the interface to become unresponsive while the server checks each one for encrypted contents.
To enable the EFS folder icons
-
On the main menu, click Edit > Global Settings.
-
Select the Enable EFS folder icons check box.
-
Click OK. (To disable the feature, clear the check box.)
Related Topic
-
Encrypted Folders (EFT Encryption) with EFT-managed encryption