Flooding and Denial of Service Prevention
EFT provides a built-in system to detect and counter against various layer-7 targeted DoS attacks. These attacks either intentionally target availability or do so indirectly as a byproduct of brute forcing, vulnerability scanning, directory traversal, and similar attacks that attempts to exploit confidentiality or integrity. EFT uses a point system to determine the likelihood of an attack, with separate counters in place to account for different attack vectors. You can control the sensitivity of the attack detection logic or override the default values, if desired.
Other Attack Types and their Prevention
To mitigate the effects of Layer 3 or 4 DoS attacks, including volumetric Distributed Denial of Service (DDoS) attacks, we recommend the use of external DDoS protection services, where traffic is redirected to a content delivery network cloud security provider, which in turn returns only clean traffic to your organization. These solutions can be costly, but are the only effective means of preventing these types of attacks.
Apart from the availability protections mentioned on this page, EFT includes additional protections against confidentiality and integrity attacks. Some of those are configurable, such as failed login attempt ban logic, password complexity rules, username blacklisting, IP white/blacklisting, banned file types, max allowed connections from same IP, and various other configurable settings. EFT also includes numerous internal protections against typical attacks as documented by OWASP, including, but not limited to:
-
Performing input and resource request validation, cleaning, and escaping
-
Applying best practices to session creation, management, destruction
-
Proper application of ACLs for resource authorization
-
Internal protections against XSS, CSRF, and similar attacks
These protections and more are covered in other sections of the guide or in knowledgebase articles in more detail.
To enable flood and DoS prevention and set the sensitivity value
-
In the administration interface, connect to EFT and click the Server tab.
-
On the Server tab, click the node of the Site you want to configure.
-
In the right pane, click the Connections tab.
-
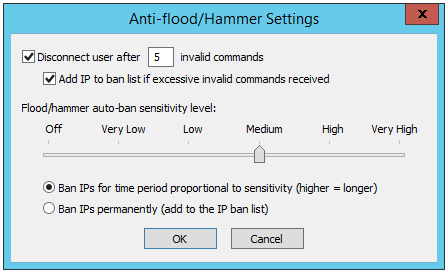
In the Network Usage and Security Settings area, next to Denial of Service settings, click Configure. The Anti-Flood/Hammer Settings dialog box appears.
-
In the Flood/hammer auto-ban sensitivity level area, specify a sensitivity level using the slider bar.
-
Click a ban period:
-
Ban IPs for time period proportional to sensitivity (higher = longer)
-
Ban IPs permanently (add to TCP/IP access restrictions list)
-
-
Click OK to close the dialog box.
-
Click Apply to save the changes on EFT.
If you set the slider to Off, Very Low, or Low on a high-security-enabled Site, a message appears to warn you that this setting violates PCI DSS requirements related to securely configuring cardholder environments.
See also Disconnecting Users after a Defined Number of Invalid Commands and Controlling Access to the Site by IP Address.
Flood and DoS Prevention Scoring
Behind the scenes, EFT applies several counters that it uses to identify possible attacks. If an attack is identified, the attackers IP is banned for a time proportionate to the sensitivity level. High sensitivity levels offer greater protection but may also result in a higher number of false positives. We recommend starting at the Medium sensitivity level, and then adjusting the slider over time as you analyze traffic patterns and characteristics.
Socket connections
This counter applies to any socket connection made with EFT’s listener ports and is useful for countering everything from malicious and intentional SYN floods to innocent but damaging misconfiguration by partners hammering your server in a misguided attempt to determine availability.
How it works: Using the Medium sensitivity value as an example, EFT sets a 1,000-point limit or threshold that must not be exceeded for a given duration of time, called a timer tick, which equates to a period of 10 seconds. Starting at zero points, each new socket connection made from the same IP address to a non-HTTP port will add 100 points to the prior value. This means that 10 connections in rapid succession (within 10 seconds) to a non-HTTP port would result in a short-term ban. Connections made to HTTP ports only accumulate 8 points at a time, to accommodate for the typical higher number of requests associated with HTTP, thus allowing up to 125 connections from the same IP during that same 10-second duration. This may seem high, but a typical HTTP pre-session behavior may yield upwards of 40-50 different requests (loading login page and various public assets, then link to lost password or other portals).
At each 10-second timer tick, the accumulated points are reduced by 350 points, effectively bringing the counter back to 0 in a little over 30 seconds (-350 points per timer tick is equal to -1050 points after three ticks), assuming no additional connections are made. If an IP exceeds the connection-points limit and is banned, it will be unbanned once the points fall back to zero. At a 35-point reduction per timer ticket, it would take roughly 30 minutes for that to occur.
Below is the table for socket connections at each sensitivity level. + points are added and - points reduced from the accumulated points.
| Security Level Characteristics – Global (IP) Counter | Protocol | Very Low |
Low | Medium | High |
Very |
|---|---|---|---|---|---|---|
| Starting points | All | 0 | 0 | 0 | 0 | 0 |
| Point limit | All | 2000 | 1500 | 1000 | 800 | 600 |
| + Points for each socket connection | HTTP | 8 | 8 | 8 | 8 | 8 |
| + Points for each socket connection | FTP, SFTP | 100 | 100 | 100 | 100 | 100 |
| - Points at each timer tick (approximately every 10 seconds) | All | (2000) | (750) | (350) | (300) | (150) |
| - Points at each timer tick if IP has been banned (exceeded limit) | All | (200) | (75) | (35) | (30) | (15) |
FTP and SFTP session flood
| Security Level Characteristics – Global (IP) Counter | User | Very Low |
Low | Medium | High |
Very |
|---|---|---|---|---|---|---|
| Starting points | Any | 0 | 0 | 0 | 0 | 0 |
| Point limit | Any | 2000 | 1500 | 1000 | 800 | 600 |
| + Points for each valid command | Any | 10 | 10 | 10 | 10 | 10 |
| + Points for each invalid command | Any | 300 | 300 | 300 | 300 | 300 |
| - Points for each session clean exit | Any | (All) | (All) | (All) | (All) | (All) |
| - Points at each timer tick (approximately every 10 seconds) | Any | (2000) | (750) | (350) | (300) | (150) |
| - Points at each timer tick if IP has been banned (exceeded limit) | Any | (200) | (75) | (35) | (30) | (15) |
HTTP session flood
HTTP/S session counters are a bit more nuanced, as there are requests that may occur both anonymously and as part of an authenticated session. The User column in the table below distinguishes between these two cases. Commands are HTTP verbs, whereas Path is the resource referenced by that verb. For example, a non-authenticated request to get a non-existent resource (perhaps a directory traversal probe) would accumulate 150 points, whereas the same request by an authenticated user would result in zero additional points. In addition to the base scores, administrators can optionally designate blacklisted or whitelisted resources (paths). A blacklisted path can be used to perform an immediate IP ban on specific paths requested by non-authenticated users.
| Security Level Characteristics – HTTP(S) Session Counter | User | Very Low |
Low | Medium | High |
Very |
|---|---|---|---|---|---|---|
| Starting points | Any | 0 | 0 | 0 | 0 | 0 |
| Point limit | Any | 2000 | 1500 | 1000 | 800 | 600 |
| + Points for each valid command | Any | 0 | 0 | 0 | 0 | 0 |
| + Points for each invalid command | Any | 300 | 300 | 300 | 300 | 300 |
| + Points for each request to non-public path | Anonymous | 150 | 150 | 150 | 150 | 150 |
| + Points for each request to non-public path | Authenticated | 0 | 0 | 0 | 0 | 0 |
| + Points for each request to non-public blacklisted path | Anonymous | 2000 | 1500 | 1000 | 800 | 600 |
| + Points for each request to non-public blacklisted path | Authenticated | 0 | 0 | 0 | 0 | 0 |
| + Points for each request to non-public whitelisted path | Any | 0 | 0 | 0 | 0 | 0 |
| - Points for each session clean exit | Authenticated | (All) | (All) | (All) | (All) | (All) |
| - Points at each timer tick (approximately every 10 seconds) | Any | (2000) | (750) | (350) | (300) | (150) |
| - Points at each timer tick if IP has been banned (exceeded limit) | Any | (200) | (75) | (35) | (30) | (15) |
Customizations
Customized Scores
The default scores were created through careful analysis of typical client interactions under various DoS scenarios; however, your needs may require customization of the default values, such as modifying only one parameter for a given sensitivity level to lower the chance of false positives under certain heavy but valid traffic patterns. To facilitate custom scenarios, EFT exposes all scoring values for each sensitivity in its Site configuration database. Please contact our support team for assistance in locating the appropriate table and applying new values.
Blacklist and Whitelist Overrides
To designate a blacklisted or whitelisted path for HTTP/S, set the following advanced properties:
AutoBanAnonymousUnauthorizedAccessServicePathAllowList = Auto-ban will ignore processing non-public access to the specified paths. AutoBanAnonymousUnauthorizedAccessServicePathBlockList = Auto-ban will ban IP address access to the specified paths. (Not the full URL, just the service path.)
{
"AutoBanAnonymousUnauthorizedAccessServicePathAllowList":[
"/",
"/custom-service",
"/sp/samlv2/sso"
],
"AutoBanAnonymousUnauthorizedAccessServicePathBlockList":[
"/mysql-admin/index.php",
"/administrator/phpMyAdmin/index.php",
"/sql/sql-admin/index.php "
]
}
Custom Scores for Admin Session
To designate a different sensitivity level for Administrative sessions, please use the advanced property: AutobanSensitivityLevelForAdminConnections