Local Security Policy Setting when Using Active Directory Authentication
To use AD authentication, Globalscape Customer Support recommends creating an AD account for the EFT service "Log on as" account with adequate privileges to all of the resources (AD domain query, network shares) required for the Site. There is no set formula for the type of account needed, because network configurations vary. Some EFT customers might need to pull users across multiple domains or might want to restrict that kind of access. Consult with your AD network administrator for assistance, if necessary.
If you are using a Domain User account (an AD account that is a member of the Domain Users group and nothing more), make sure that full permissions are granted to the EFT service domain user account in the following locations:
-
Installation folder
-
Application data folder
-
Windows temp folder (varies by system)
-
Any shared drive paths required by EFT
-
Any output directories to which EFT may need to read/write files
In Component Services, provide the appropriate permissions:
-
Click Start > Run, type dcomcnfg.exe, then press ENTER. Component Services appears.
-
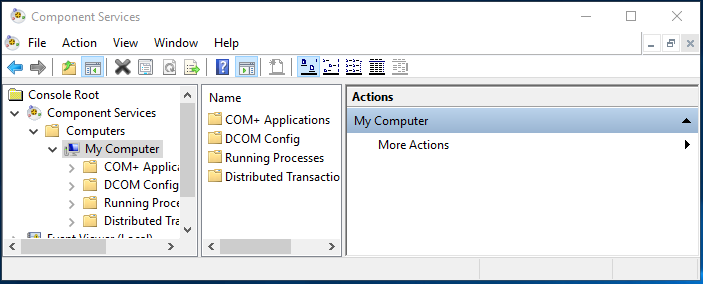
Expand Component Services > Computers.
-
Right-click the My Computer node, and then click Properties. The My Computer Properties dialog box appears.
-
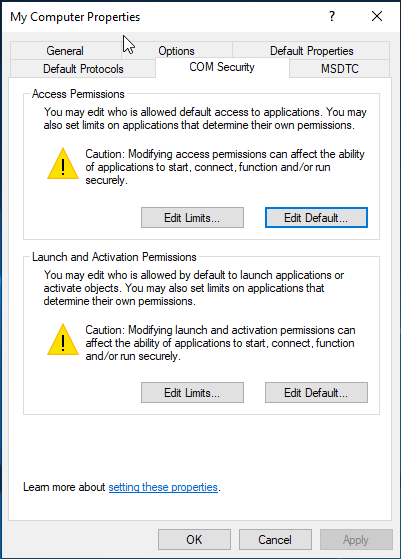
Click the COM Security tab.
-
Under Access Permissions, click Edit Default.
-
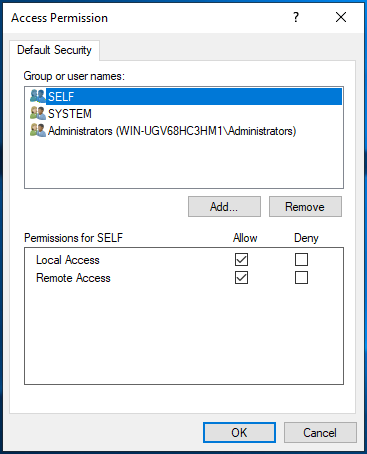
Add the domain user and then select the Allow check box for Local Access and Remote Access.
-
Click OK to close the Access Permission dialog box.
-
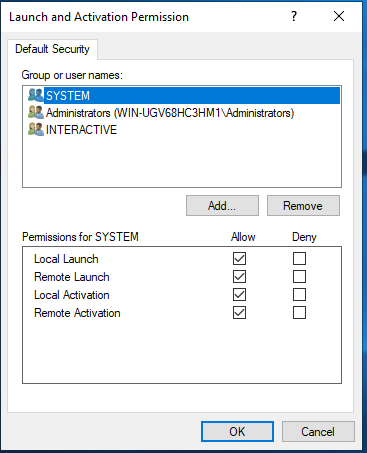
Under Launch and Activation Permissions group, click Edit Default.
-
Add the domain user and then select the Allow check box for Local Launch and Local Activation.
-
Click OK, then OK again, then close Component Services.
If you run into issues, run Process Monitor or similar tools and isolate non-success results caused by cftpsai.exe, cftpstes.exe, gsawe.exe, and other EFT processes.
Refer to Support for Foreign Groups for more information.