TLS 1.3 Support
EFT v8.0.6 and later support the TLS 1.3 protocol with OpenSSL v1.1.1.
TLS 1.3 can be selected in the protocol list in the TLS Settings dialog box. It is enabled by default. TLS 1.3 can also be disabled/ turned off in favor of using a different variant, such as TLS 1.2. There is no TLS 1.3 available in FIPS mode. (EFT in FIPS mode continues to use v1.0.2u.)
You can use developer tools in the browser to verify that the Web Transfer Client is using TLS.
To verify that TLS 1.3 is being used
-
Open your browser and navigate to the Web Transfer Client URL, such as https://localhost/Web/Account/Login.htm.
-
Do not log in.
-
Maximize the browser window.
-
Press F12 on your keyboard.
-
Click the right-facing arrows to open the drop-down box:
-
Click Security. The Security overview appears.
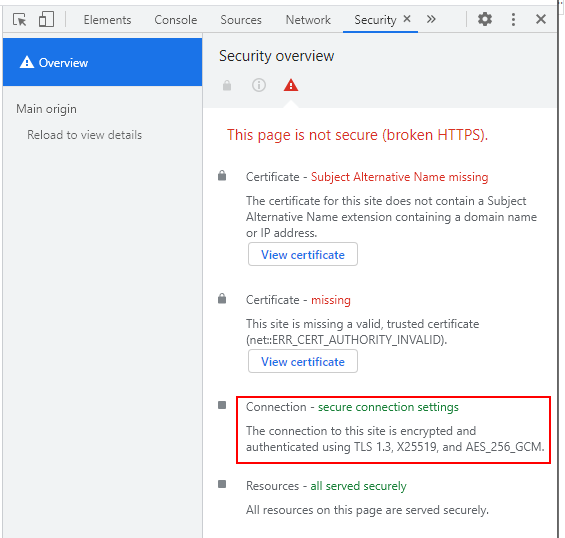
The Connection section describes whether the connection is encrypted and which ciphers are being used. (This screen shot was taken on a test system and did not have a valid certificate. That information is also displayed here on the Security tab.)
The following 25 ciphers are enabled by default:
-
TLS_AES_256_GCM_SHA384
-
TLS_CHACHA20_POLY1305_SHA256
-
TLS_AES_128_GCM_SHA256
-
ECDHE-ECDSA-AES128-GCM-SHA256
-
ECDHE-RSA-AES128-GCM-SHA256
-
ECDHE-ECDSA-AES128-CCM8
-
ECDHE-ECDSA-AES128-CCM
-
ECDHE-ECDSA-AES128-SHA256
-
ECDHE-RSA-AES128-SHA256
-
AES128-GCM-SHA256
-
AES128-CCM8
-
AES128-CCM
-
AES128-SHA256
-
ECDHE-ECDSA-AES256-GCM-SHA384
-
ECDHE-RSA-AES256-GCM-SHA384
-
ECDHE-ECDSA-AES256-CCM8
-
ECDHE-ECDSA-AES256-CCM
-
ECDHE-ECDSA-AES256-SHA384
-
ECDHE-RSA-AES256-SHA384
-
AES256-GCM-SHA384
-
AES256-CCM8
-
AES256-CCM
-
AES256-SHA256
-
ECDHE-ECDSA-CHACHA20-POLY1305
-
ECDHE-RSA-CHACHA20-POLY1305
The following algorithms are only available when FIPS is turned off:
-
TLS_AES_256_GCM_SHA384
-
TLS_CHACHA20_POLY1305_SHA256
-
TLS_AES_128_GCM_SHA256
-
ECDHE-ECDSA-CHACHA20-POLY1305
-
ECDHE-RSA-CHACHA20-POLY1305
-
DHE-RSA-CHACHA20-POLY1305
-
ECDHE-ECDSA-AES256-CCM8
-
AES256-CCM8
-
ECDHE-ECDSA-AES256-CCM
-
DHE-RSA-AES256-CCM
-
AES256-CCM
-
ECDHE-ECDSA-ARIA256-GCM-SHA384
-
ECDHE-ARIA256-GCM-SHA384
-
DHE-RSA-ARIA256-GCM-SHA384
-
DHE-DSS-ARIA256-GCM-SHA384
-
ARIA256-GCM-SHA384
-
ECDHE-ECDSA-AES128-CCM8
-
DHE-RSA-AES128-CCM8
-
AES128-CCM8
-
ECDHE-ECDSA-AES128-CCM
-
DHE-RSA-AES128-CCM
-
AES128-CCM
-
ECDHE-ECDSA-ARIA128-GCM-SHA256
-
ECDHE-ARIA128-GCM-SHA256
-
DHE-RSA-ARIA128-GCM-SHA256
-
DHE-DSS-ARIA128-GCM-SHA256
-
ARIA128-GCM-SHA256
-
ECDHE-ECDSA-CAMELLIA256-SHA384
-
ECDHE-RSA-CAMELLIA256-SHA384
-
DHE-RSA-CAMELLIA256-SHA256
-
DHE-DSS-CAMELLIA256-SHA256
-
ADH-CAMELLIA256-SHA256
-
CAMELLIA256-SHA256
-
ECDHE-RSA-CAMELLIA128-SHA256
-
DHE-RSA-CAMELLIA128-SHA256
-
DHE-DSS-CAMELLIA128-SHA256
-
ADH-CAMELLIA128-SHA256
-
CAMELLIA128-SHA256
-
DHE-RSA-DES-CBC3-SHA
-
DHE-DSS-DES-CBC3-SHA
-
DHE-RSA-AES256-CCM8
-
ECDHE-ECDSA-CAMELLIA128-SHA256
The following old and vulnerable algorithms were removed. (All that use DH and ECDH.) You cannot turn them on in non-FIPS mode. Here is the full list:
-
DH-DSS-AES256-GCM-SHA384
-
DH-RSA-AES256-GCM-SHA384
-
ECDH-RSA-AES256-GCM-SHA384
-
ECDH-ECDSA-AES256-GCM-SHA384
-
ECDH-RSA-AES256-SHA384
-
ECDH-ECDSA-AES256-SHA384
-
DH-DSS-AES256-SHA
-
DH-RSA-AES256-SHA
-
ECDH-RSA-AES256-SHA
-
ECDH-ECDSA-AES256-SHA
-
DH-DSS-AES256-SHA256
-
DH-RSA-AES256-SHA256
-
DH-DSS-CAMELLIA256-SHA
-
DH-RSA-CAMELLIA256-SHA
-
DH-DSS-AES128-GCM-SHA256
-
DH-RSA-AES128-GCM-SHA256
-
ECDH-RSA-AES128-GCM-SHA256
-
ECDH-ECDSA-AES128-GCM-SHA256
-
DH-DSS-AES128-SHA
-
DH-RSA-AES128-SHA
-
ECDH-RSA-AES128-SHA
-
ECDH-ECDSA-AES128-SHA
-
DH-DSS-AES128-SHA256
-
DH-RSA-AES128-SHA256
-
ECDH-RSA-AES128-SHA256
-
ECDH-ECDSA-AES128-SHA256
-
DH-DSS-SEED-SHA
-
DH-RSA-SEED-SHA
-
DH-DSS-CAMELLIA128-SHA
-
DH-RSA-CAMELLIA128-SHA
-
DHE-DSS-RC4-SHA
-
ECDH-RSA-RC4-SHA
-
ECDH-ECDSA-RC4-SHA
-
DH-DSS-DES-CBC3-SHA
-
EDH-RSA-DES-CBC3-SHA
-
EDH-DSS-DES-CBC3-SHA
-
DH-RSA-DES-CBC3-SHA
-
ECDH-RSA-DES-CBC3-SHA
-
ECDH-ECDSA-DES-CBC3-SHA
Also note, that "Export" status is a very outdated concept and is no longer supported by OpenSSL. This option is removed.