Cryptography: OpenSSL Action
You can configure an OpenSSL action in an event rule to sign or verify a file.
The OpenSSL action is supported on HTTPS and SFTP and can be used for the following triggers:
-
Scheduler (Timer)
-
Folder monitor
-
File Uploaded
-
Verified Upload Succeeded events
EFT can only create detached signature files; however, it can verify signatures for non-detached, detached, and XML Enveloped signature files.
The signing certificate formats include:
-
.pem
-
.cer, .crt, .der – in binary DER form only
-
.p7b, .p7c – PKCS#7 SignedData structure without any data, just the certificate
-
.p12 – PKCS#12, may contain certificate(s) (public) and private keys (password protected)
-
.pfx – PFX, predecessor of PKCS#12 (usually contains data in PKCS#12 format, e.g., with PFX files generated in IIS)
To use the Cryptography: OpenSSL action
-
Create an event rule (or use existing rule) and add the action to the event.
-
Click one of the linked items. The Open SSL dialog box appears.
-
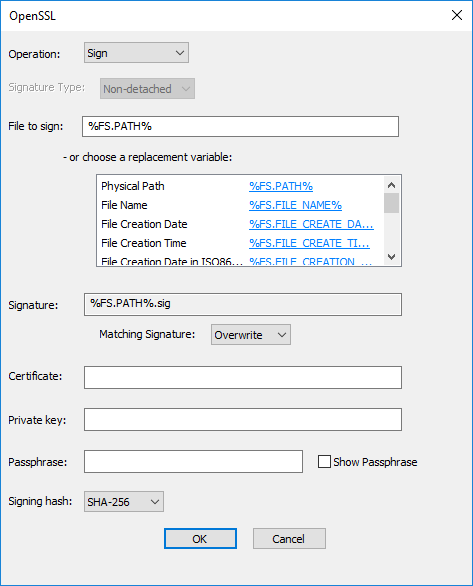
In Operation, click the drop-down list and click Sign or Verify Signature. The available fields change depending on whether you choose Sign or Verify Signature.
-
If you clicked Sign, the Signature Type field is read-only.
-
In the File to sign box, The File System variable %FS.PATH% is the default. You can chooses a replacement variable instead.
-
The Signature field is read-only and displays the filename of the signature file path used, which is the same as the file to process, with ".sig" appended to the filename. This text box is auto-filled and non-editable.
-
In Matching Signature, specify what to do if a duplicate signature is found: Overwrite, Skip, or Fail.
-
In the Certificate, Private Key, and Passphrase fields, provide the associated certificate information.
-
The Show Passphrase check box allows you to verify the passphrase was typed correctly.
-
In Signing hash, click the applicable algorithm: SHA-256, SHA-384, SHA-512.
-
If you clicked Verify Signature, in File to sign, specify the file path, or click another variable in the list of replacement variables. Then specify the Certificate path and click OK.
-
Add additional actions or conditions as needed, then click Apply to save the Event Rule.