OpenPGP and EFT
EFT employs industry-standard OpenPGP (based on the open source implementation of Pretty Good Privacy) technology to safeguard data at rest. In contrast to symmetric encryption technologies that rely on a single password or shared secret for encryption and decryption, OpenPGP uses a public/private key pair and a password. Although widespread, dual-factor encryption technologies such as OpenPGP are not universally employed throughout the industry, because of the complexities involved in key creation, management, and distribution, as well as the application of public-key infrastructure technologies. Another drawback is the fact that the entire file must be present for OpenPGP encryption to work, resulting in a very brief period of time whereby data is stored "in the clear," until the encryption process is completed and the source (unprotected) file is deleted.
EFT supports encrypting, decrypting , signing, verifying OpenPGP messages in the format specified by RFC 4880. Refer to http://cdn.nsoftware.com/help/IG9/cs/OpenPGP.htm for more information.
For details of using OpenPGP in Event Rules, refer to OpenPGP Encryption/Decryption Action.
How OpenPGP Encrypt/Decrypt Works
Below are illustrations of how OpenPGP encryption and decryption works.
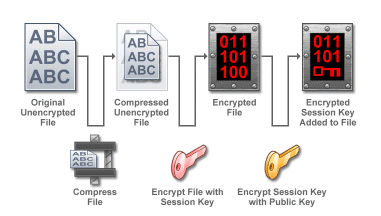
Encryption:
Decryption:
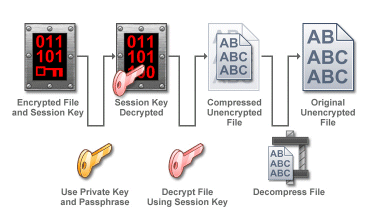
In EFT, the OpenPGP data encryption (or decryption) process is directed by Event Rules that specify how data files are treated in a particular context. OpenPGP uses a public key and a private key to encrypt data and maintain security. These two components are considered a key pair and are associated with a particular Site. The key pair is stored on the OpenPGP Keyring, which is the management tool for public keys and key pairs. The OpenPGP Keyring contains all key information and allows import, export, creation, and deletion of keys.
New key pairs are created using the OpenPGP Key Generation wizard. The wizard prompts you for key parameters and creation of a passphrase. Once the new key pair is generated, you must determine if the new key pair will be the default for the entire Site. Allowing assignment of a default key pair will automatically select this key when configuring an Event Rule using OpenPGP encryption.
The example below shows how a trigger Event (On Upload) is used to initiate OpenPGP encryption.
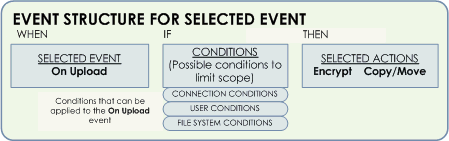
In an Event Rule, when a selected event occurs (for example, a file is uploaded to EFT), if the specified Condition exists (for example, user is member of group A), then the selected actions occur (for example, encrypt the file).
OpenPGP encryption is only available for certain Events:
-
On Upload - when a file is uploaded to a location.
-
On Rotate Log - when a log file is closed out and a new log initiated.
-
On Timer - an Event that occurs once or according to a schedule.
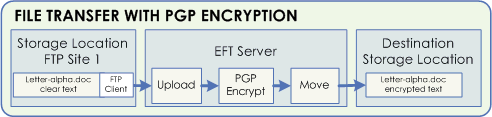
Below is a simplified example of the file transfer process in which EFT uses OpenPGP to encrypt uploaded data and the off-load capabilities of EFT to move the file to another location.
Related Topics