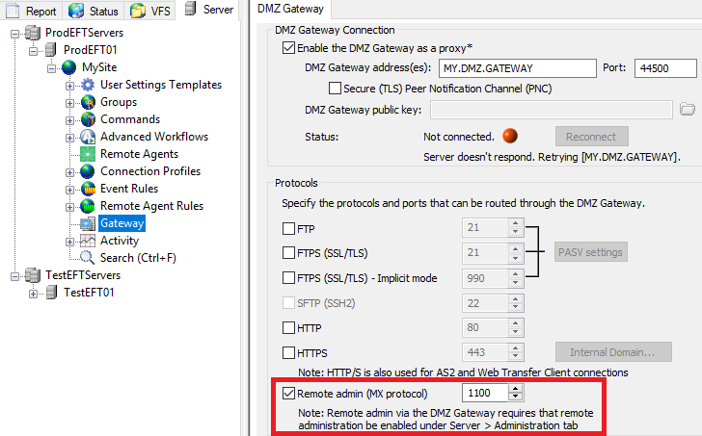
Remote Administration through DMZ Gateway
EFT shares its Site-level manual IP access list and permanent auto-ban IP (not temporary auto-ban) list to DMZ Gateway so that it can block IP addresses before reaching EFT.
Now that remote administration can be routed through DMZ Gateway, we allow EFT to transmit the remote administration manual IP access list to DMZ Gateway for the same purpose. For a client to perform remote administration through DMZ Gateway, its IP must pass both the Site-level and remote administration IP access validation. Note that the remote administration auto-ban feature in EFT is hardcoded to ban IP addresses temporarily, NOT permanently. Therefore, this auto ban list is not communicated to DMZ Gateway and rather it is enforced by EFT itself.
For customers with a new version of EFT supporting the remote administration through DMZ Gateway feature, and with an older DMZ Gateway, they can still do remote administration through DMZ Gateway, but only Site-level manual and Site-level permanent auto-ban IP access lists will be enforced at the DMZ Gateway. Remote administration IP access lists will be enforced only by EFT.
Notes to consider:
-
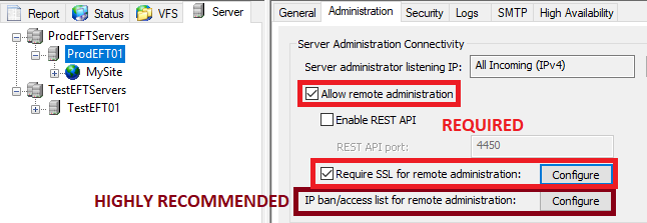
To enable remote administration through DMZ Gateway, you’ll need to enable remote administration in the EFT administration interface at the Server level and select the Require SSL for remote administration check box.
-
The Site and remote administration IP access/ban lists in EFT are combined at DMZ Gateway. If there is a conflict, e.g., the remote administration block list allows an IP address that is blocked at the Site level, then the IP address will be blocked (least privileges assignment).
-
If EFT automatically bans an IP address temporarily (as result of DoS/Flooding or other trigger), that IP address will not be shared with the DMZ Gateway. The administration access will still be blocked, but at EFT, not DMZ Gateway. The administrator can manually add those IP addresses to the permanent ban list, which will propagate to DMZ Gateway.
-
EFT can work with older DMZ Gateway versions (v<3.5) and still allow remote administration; however, when connected to an older DMZ Gateway, any IP address in the administration access/ban list will NOT be shared with the DMZ Gateway, as the older versions do not support receiving the administration IP access/ban list. Again, EFT will still block the connection, but DMZ Gateway will not.
-
If you are remotely connected to EFT via DMZ Gateway and make a change to the EFT<->DMZ Gateway settings, including disconnecting EFT from DMZ Gateway, the active session will not be affected. If/when you attempt to reconnect to EFT via DMZ Gateway, you will experience the effects of any changes.