Script: PowerShell Action
(Requires EAM) The Run PowerShell script Action is used in Event Rules to execute a PowerShell script. (Requires Windows PowerShell 4.0 or later.)
EFT will always use Windows PowerShell ISE (if available on the target machine) to edit the embedded script, regardless of your default setting.
A PowerShell log is enabled and saved in the \ProgramData\ folder as \Logs\powershell.log.
100s of PowerShell functions and cmdlets are available. Refer to https ://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/get-date?view=powershell-7 for cmdlets examples and information about using PowerShell.
VariantWrapper for variables to be passed as VARIANT will fail in PowerShell. (This is a bug in PowerShell.)
EFT context variables (where populated) need to be passed into the script. The script will access variables with $EFT_CONTEXT global variable via the GetVariable method. Create or modify context variables by using SetVariable method of $EFT_CONTEXT global variable.
The script action is able to modify or create any variables except the systems environment (%ENV.) pseudo variables. When %ENV.[value]% is used in event rules, EFT will look up the [value] from the systems environment variables.
When referencing a dataset in PowerShell, PowerShell does not handle the % symbol, so this is how it would be accessed: ("Customer.CurrentRow.FirstName")
$EFT_CONTEXT.GetVariable("Customer.CurrentRow.FirstName") + ',' +
$EFT_CONTEXT.GetVariable("Customer.CurrentRow.LastName")
>>C:|Users\Administrator\Desktop\test
To user a PowerShell script in an event rule
-
In the administration interface, connect to EFT and click the Server tab.
-
Add the Run PowerShell script Action to the rule.
-
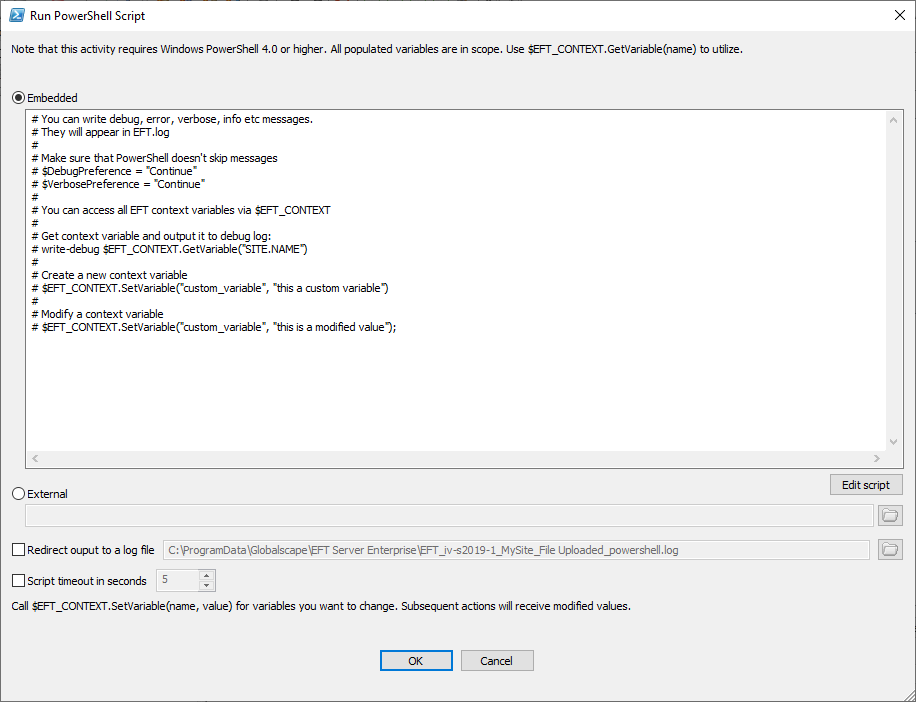
In the Rule Builder, click the embedded script link. The Run PowerShell Script dialog box appears with a sample script that is commented out.
-
Click Embedded if you want to paste a script into the dialog box or click External of you want to point to a PowerShell script in a folder that EFT can access.
-
To create a PowerShell log file, select the Redirect output to a log file check box, then specify where to save the log. By default, it is saved to C:\ProgramData\Globalscape\EFT Server\<computer_name>_<site_name>_<event_rule_name>_powershell.log.
-
If you want to analyze PowerShell output in context with the event trigger and all associated actions with that event, you would need to clear the Redirect check box, apply changes, then open logging.cfg, un-comment the Event.PowerShell logger (remove the #), then save the logging.cfg file. (If you leave the Redirect check box selected, the PowerShell logs will not appear in logging.cfg for this action.)
-
Click Edit Script to view/edit the script in a text editor. (Windows PowerShell ISE is the default editor.)
-
Select the Script timeout check box and specify the number of seconds before terminating the script.
-
Click OK to save the action.
-
Add other conditions or actions as needed, then click Apply to save the rule.