![]()
Note that the above description is a gross generalization of Public Key Infrastructure and the TLS/SSL protocol. For more detailed information, please refer to the following online articles:
This topic describes configuring a TLS/SSL Certificate Authority Certificate Chain for use with the Mail Express Server’s Web Server public certificate/private key pair.
What is the Mail Express Server Public Certificate/Private Key Pair?
In Mail Express 3.0+, an administrator may configure the TLS/SSL public certificate and private key pair via the General Configuration page of the Mail Express Server administration interface. This key pair is required to provide TLS/SSL communications when a client connects to the Mail Express Server’s HTTPS port (port 443).
As part of the TLS/SSL protocol, the key pair is used to authenticate the Mail Express Server to the connecting client. The client, such as a browser, performs a number of checks to ensure it is talking to the correct, trusted server.
One of these checks compares the “Common Name” attribute of the Mail Express Server’s public certificate to the hostname portion of the URL to which the browser is connecting. If they do not match, the browser will issue a warning to the user that the certificate doesn’t match the server’s hostname.
Another check performed by the browser is verifying that the public certificate has been signed by a trusted certificate authority (CA) using the CA’s own public certificate and private key pair. Signing of public certificates is hierarchical in that a public certificate may be signed by a certificate authority, and that CA’s public certificate may have, in turn, been signed by another certificate authority, and so on.
Browsers, by default, include a set of industry standard trusted CA’s public certificates in a “Trusted Certificate Authority” list. Additionally, users may add to this list of trusted CAs. When the browser checks the server’s public certificate, it traces up the signing hierarchy starting at the server’s public certificate looking for a certificate authority that is in its trusted list.
|
|
Note that the above description is a gross generalization of Public Key Infrastructure and the TLS/SSL protocol. For more detailed information, please refer to the following online articles: |
What is an SSL Certificate Authority Certificate Chain?
In some cases, a public certificate is signed by one or more intermediate certificate authorities (CA). For example, a commercial certificate authority uses its own intermediate certificate to sign the server’s public key rather than their root certificate, then provides you with the appropriate intermediate public certificates, and often also their root certificate, when sending back your signed public certificate.
The public certificates for the intermediate CAs often are not in the client application’s list of trusted CAs. Rather, the client application will only know the root certificate for the commercial certificate authority. However, the client needs access to these public certificates so that it can verify the signature hierarchy of the server’s key. It needs these intermediate public keys so that it can “walk the chain” from the server’s public certificate up to a trusted certificate authority.
The TLS/SSL protocol provides a mechanism whereby the web server can provide the list of intermediate certificate authorities to the connecting client. The client can then verify the signature chain up to a trusted certificate authority. For this functionality to work in Mail Express Server you must properly configure the certificate chain.
When do I need to specify an SSL Certificate Authority Certificate Chain?
In theory, you only need to specify a chain if the commercial CA signed the server’s public certificate with an intermediate certificate that is not included in the industry-standard set of trusted CA public keys shipped by default within the more popular browsers.
However, there are many types and versions of browsers in use, making it difficult to guarantee that all clients connecting to the web server will possess the necessary trusted CA public certificates. It is safer to provide the full certificate chain proactively from the web server. As such, our recommended best practice is to configure the full certificate chain provided by the commercial certificate authority.
How is the SSL Certificate Authority Certificate Chain configured?
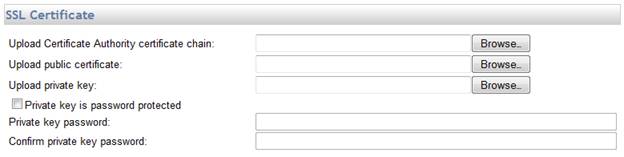
The SSL Certificate Authority (CA) certificate chain may be configured in the SSL Certificate section of the General Configuration page within the Mail Express Server’s administration interface.
|
|
Note that use of the certificate chain is optional. If you do not wish to specify a certificate chain simply don’t provide a file for the field. |
If you want to configure a certificate chain, note that the public certificate, private key, and optional private key password settings must all be specified at the same time. The interface does not provide a method to configure each setting independent of one another.
To specify a Certificate Authority certificate chain, click Browse to specify the file containing the certificate chain in the format specified below.
Supported Certificate Chain Format
The certificate chain should be contained in a single file and consist of the list of public certificates starting with the certificate of the CA that signed the web server’s public certificate and range up to the final root trusted CA certificate (the public certificate known to be in the browser’s list of trusted certificate authorities).
|
|
Note that it isn’t strictly necessary to include the final trusted certificate authority’s public certificate in the chain. However, it is recommended to include this certificate, when available, for the sake of completeness. |
Each certificate within the file should be in the PEM-encoded format. Each certificate should start with the text “-----BEGIN CERTIFICATE-----“ and end with the text “-----END CERTIFICATE-----“.
An example of a certificate chain file’s contents for a chain consisting of a single intermediate CA and the root CA is as follows (truncated for space):
-----BEGIN CERTIFICATE-----
MIIGzDCCBLSgAwIBAgIBATANBgkqhkiG9w0BAQUFADCBpjELMAkGA1UEBhMCVVMx
DjAMBgNVBAgTBVRleGFzMRQwEgYDVQQHEwtTYW4gQW50b25pbzEaMBgGA1UEChMR
R2xvYmFsU0NBUEUsIEluYy4xFDASBgNVBAsTC0VuZ2luZWVyaW5nMRUwEwYDVQQD
EwxtaWtlLXJvb3QtY2ExKDAmBgkqhkiG9w0BCQEWGW1oYW1iaWRnZUBnbG9iYWxz
Y2FwZS5jb20wHhcNMTAxMTE4MjEyMzA4WhcNMTUxMTE3MjEyMzA4WjCBmDELMAkG
A1UEBhMCVVMxDjAMBgNVBAgTBVRleGFzMRowGAYDVQQKExFHbG9iYWxTQ0FQRSwg
SW5jLjEUMBIGA1UECxMLRW5naW5lZXJpbmcxHTAbBgNVBAMTFG1pa2UtaW50ZXJt
ZWRpYXRlLWNhMSgwJgYJKoZIhvcNAQkBFhltaGFtYmlkZ2VAZ2xvYmFsc2NhcGUu
Y29tMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAsF+vlQfZnssDsqFx
IXCGHST1jiTHJGGHiiwc9Qb1NPDbyvcdNXvcfkdyYjd8VlYyo3/jnj6xx3PxzJhG
NmnBGJ0I7h/RFJaG7nmGfeWUHCLsVjGfQeEjC++d6zzE3unPOiLVIhv9abD6kISa
hLdltOBcT19mqg1yG4Q4XExjeYmSYGFiDIdv+WwwUssTyPdppaaWcsjNaFcmuopU
RfmcfULPFwvFN6LsgvSTYwYe9l8421fA5c+WiR1JomjGuJT/0sITpzQRCenWi0S0
WZuftT61+fU0/OxINhgO4yK6C1eOoaxmoEG2oVm2o4Bjy9ceYN2UqdRGt8t/23/h
Wog3vEwdoHqghrjeiGWWs98qfzINKokiMd7APcxdkZ1SzyvOEWht4V3/XedleiMx
8WGjbVtRg/k4Hgf2TGwxcw==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIG4jCCBMqgAwIBAgIJAJjguYVnU08GMA0GCSqGSIb3DQEBBQUAMIGmMQswCQYD
VQQGEwJVUzEOMAwGA1UECBMFVGV4YXMxFDASBgNVBAcTC1NhbiBBbnRvbmlvMRow
GAYDVQQKExFHbG9iYWxTQ0FQRSwgSW5jLjEUMBIGA1UECxMLRW5naW5lZXJpbmcx
FTATBgNVBAMTDG1pa2Utcm9vdC1jYTEoMCYGCSqGSIb3DQEJARYZbWhhbWJpZGdl
QGdsb2JhbHNjYXBlLmNvbTAeFw0xMDExMTgyMTE5NDdaFw0xNTExMTcyMTE5NDda
MIGmMQswCQYDVQQGEwJVUzEOMAwGA1UECBMFVGV4YXMxFDASBgNVBAcTC1NhbiBB
bnRvbmlvMRowGAYDVQQKExFHbG9iYWxTQ0FQRSwgSW5jLjEUMBIGA1UECxMLRW5n
aW5lZXJpbmcxFTATBgNVBAMTDG1pa2Utcm9vdC1jYTEoMCYGCSqGSIb3DQEJARYZ
bWhhbWJpZGdlQGdsb2JhbHNjYXBlLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQADggIP
xYK3mO1034kBdDxmVoBeEwfjWWPyC/uyFGwCNZCzoAQGMxNAnj33NBiCLHJRo1Z5
BxirSSMxOT4LEkmkOhuTyKB0TJZf+8wP8pK5BsO3xjO+uM1K3LY=
-----END CERTIFICATE-----
How do I know that it is working?
Verify that the chain is functioning properly by navigating to the Mail Express Server using your preferred browser. Prior to testing, you will want to ensure you haven’t previously permanently granted an “exception” for the server’s SSL Certificate warning within the browser.
You may optionally test from a computer known to have never visited the server before or you may clear the exceptions from the browser. The exact details on clearing the exception is browser dependent, but typically involves locating the list of trusted certificate authorities in the browser and checking if a certificate is present for the Mail Express Server’s URL (see below for the proper URL). If present, the certificate should be removed from the list.
When navigating to the Mail Express Server you must use the URL that corresponds to the Common Name attribute used in the server’s public certificate. For example, if the server’s public certificate Common Name is set to “mailexpress.example.com” you would navigate your browser to https://mailexpress.example.com.
If the chain has been correctly configured and the root trusted CA certificate is known to the browser, then the browser should navigate directly to the page.
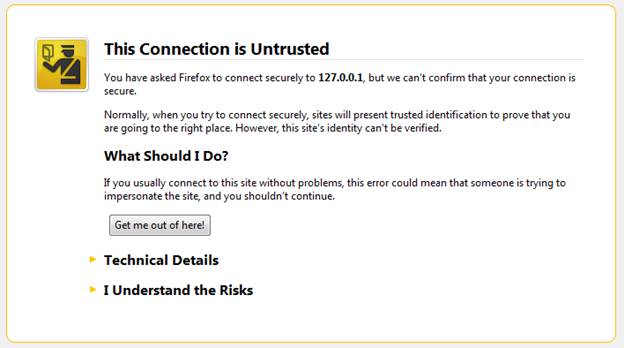
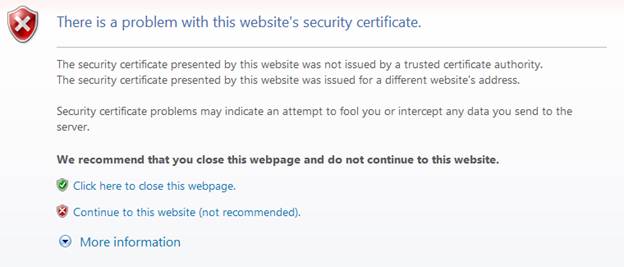
If something is wrong, then the browser will typically display an SSL Certificate warning page.
In Firefox, such a warning would be similar to:
In Internet Explorer, such a warning would be similar to:
Misconfiguration of the chain is not the only cause for the browser to display the warning page. You must examine the additional details provided by the browser to determine the exact cause of the error.
Other causes include:
Use of the wrong URL to access the Mail Express Server
Use of the wrong Common Name in the Mail Express Server’s public certificate
The final certificate authority is not in the browsers list of trusted certificate authorities.
The server’s public certificate has expired.