SSL Certificates
The majority of browsers will issue a warning to users when navigating to a site that uses a self-signed certificate. Typically this behavior is undesirable. As such it is highly recommended that the Mail Express Server be configured to use an alternate public key/private key pair that has been signed by a trusted Certificate Authority. Mail Express also supports certificate chaining.
-
The public certificate is specified with the following configuration item:
-
-
The private key is specified with the following configuration item:
-
-
If the private key is encrypted then the password is specified with the following configuration item:
-
-
If the private key is unencrypted the line should be removed.
-
Both the public certificate and private key files must be in the PEM-encoded format.
-
If an encrypted private key is specified, it must be in traditional PEM-encoded format. PKCS#8 formatted encrypted private keys are not currently supported.
-
Both RSA and DSA key types are supported.
-
For information on more advanced certificate handling options such as specifying revocation lists, refer to:
-
When you upload your own certificate/key pair those files are overwritten; however, copies of the default files are saved as MailExpressDefault.crt and MailExpressDefault.key in case you need to go back to the defaults.
Specifying an SSL Certificate
A self-signed certificate contains a public key, information about the owner of the certificate, and the owner's signature. It has an associated private key, but it does not verify the origin of the certificate through a third-party certificate authority. To achieve the highest level of authentication between critical software components, do not use self-signed certificates, or use them selectively.
The files associated with an SSL certificate key pair are:
Private key file (.key) - The private key should never be distributed to anyone. It is used to decrypt the session, which is encrypted by the public key (A message encrypted with a recipient's public key cannot be decrypted by anyone except the recipient possessing the corresponding private key.
Certificate file (.crt) - This is a signed certificate, whether self-signed or signed by an intermediate certificate authority.
You can specify an SSL certificate and key on the General Configuration page in the administration interface or paste the certificate and key files into the Mail Express configuration directory.
If you are using Mail Express with EFT Server v6.5 or later, you can create a PEM-encoded, self-signed SSL certificate in EFT and use that certificate in Mail Express. Mail Express will, "behind the scenes," convert the certificate to a format that it can use.
To Specify an SSL Certificate in the Mail Express administration interface
-
Launch the Mail Express Server administration interface. (e.g., click Start > Programs > Globalscape > Mail Express > Mail Express Admin or double-click the desktop shortcut).
-
Log in using the Mail Express Server administrator username and password that you specified during installation of the server.
-
In the SSL Certificate section, provide the SSL certificate information.
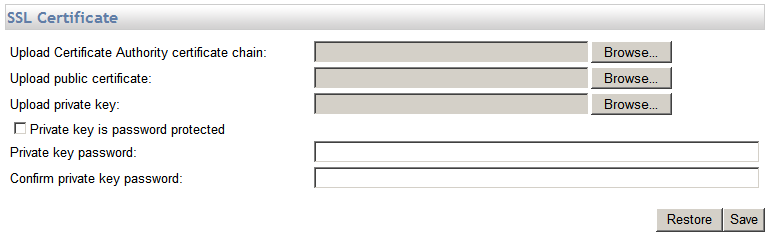
-
In the Upload certificate box, click Browse to find the signed certificate file (.crt).
-
In the Upload key box, click Browse to find the key file for the certificate (.key).
-
If a password is required for this certificate, select the SSL key is password protected check box, then provide the password in the SSL key password and Confirm SSL key password boxes.
-
Click Save to save the changes on the server or click Restore to cancel the changes. You must restart the Mail Express Server service before the new certificate/key takes effect.
Manually Configuring SSL Certificate/Key Options
You can specify an SSL certificate and key on the General Configuration page in the administration interface as described above. If you want to paste the certificate and key files into the Mail Express configuration directory and configure the certificate/key options manually, refer to the procedure below.
To configure SSL certificate/key options manually
-
Obtain an appropriate public certificate/private key pair signed by a trusted certificate authority.
-
The public certificate and private key may be either RSA or DSA-based.
-
The public certificate and private key should be placed in separate files and must be PEM encoded.
-
If an encrypted private key is specified it must be in traditional PEM-encoded format. PKCS#8 formatted encrypted private keys are not currently supported.
-
Log in (with administrator privileges) to the computer on which Mail Express Server is installed.
-
Navigate to the Mail Express configuration directory (e.g., C:\Program Files\Globalscape\Mail Express\conf).
-
Name the files MailExpress.crt and MailExpress.key. and paste them into the directory. This will overwrite the default cert/key pair. Backups of these files are shipped with Mail Express in case you need to revert to the original files. The backups are named MailExpressDefault.crt and MailExpressDefault.key.
-
Modify the configuration to use the new files:
-
Using a text editor, edit the <Installation Directory>\conf\server.xml configuration file.
-
Locate the “Connector” that defines the default port 8443 listener. This “Connector” may be found by searching for the following text:
-
port="8443"
-
Change the SSLPassword setting for the “Connector” to the password used to encrypt the private key:
-
SSLPassword="mailexpress"
-
Alternatively, if password protected was not used on the private key, then it should read:
-
SSLPassword=""
-
If the DMZ Gateway is being used the SSLPassword setting must also be modified for the DMZ Gateway Protocol Handler connector. This “Connector” may be found by searching for the following text:
-
protocol="com.globalscape.protocolhandler.DMZProtocolHandler"
-
Restart Mail Express Server.
What if I specify an invalid certificate/key pair or wrong password?
If you upload an invalid certificate or key, or provide an incorrect password, when you restart the server, the server will not be able to create the HTTPS listener and you will not be able to connect to Mail Express Server. To get back to a working state, you need to manually swap out the bad certificate/key pair with the defaults and change the password.
For the procedure for manually swapping out the bad certificate/key pair with the defaults and changing the password, refer to Resetting the Configuration of the SSL Certificate and Key.