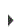Network Access to IBM i Servers
Exit Point Manager acts as your software firewall between networked clients and your IBM i servers. Exit Point Manager eliminates the problems you would see in the previous scenario:
Network Access controlled by Powertech Exit Point Manager
- Exit Point Manager provides a secured audit and reporting capability so you can easily see who is doing what. It also provides real-time alerts when a user tries to circumvent the access rules you've specified.
- Exit Point Manager allows you to configure network access rules to control who can do what. For example, using Exit Point Manager you can enforce network rules that say "Bob is allowed to download the payroll file, but cannot upload the file, or modify it in any way."
Exit Point Manager integrates with the IBM i network server programs at the exit point level. When you activate Exit Point Manager, several exit point programs are installed in the IBM i registration facility. You can view the names of these exit-point programs using the IBM i WRKREGINF (Work with Registration Information) command.
The Powertech Exit Point Manager exit point programs are called when someone makes a network request to the associated server. For example, when a user requests an FTP logon, the IBM i FTP server passes control to the Exit Point Manager exit point program to allow Exit Point Manager to validate the request. Exit Point Manager may tell the FTP server to accept or reject the FTP logon request, or to perform some other action, such as sending an alert message that an intruder has tried to penetrate the system.
For a complete overview of the IBM i servers and their functions, see Appendix B: Servers and Functions. You'll find useful information to help you define your Exit Point Manager access rules.
 Previous
Previous