Changes to Security Options for SSH & SSL Connections in JAMS
File Transfer using the SFTP File Type
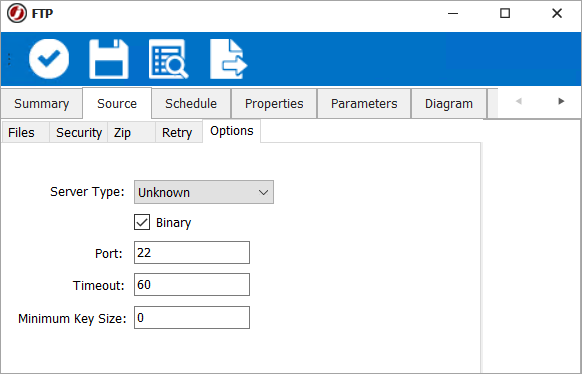
When using the SFTP Transfer type in a File Transfer Job, the Options tab will correspond with the screenshot below.
File Transfer using the SCP File Type
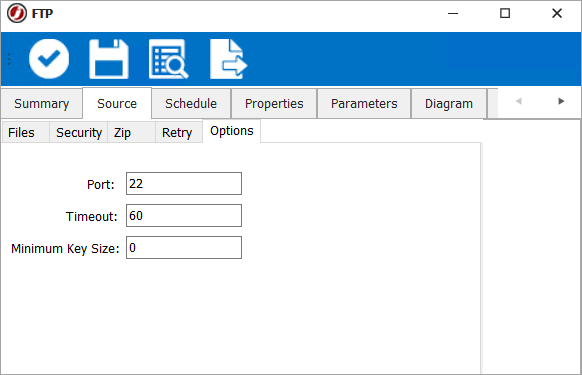
When using the SCP Transfer type in a File Transfer Job, the Options tab will look like the screenshot below.
In this case the Minimum Key Size property functions the same as described in the previous section.
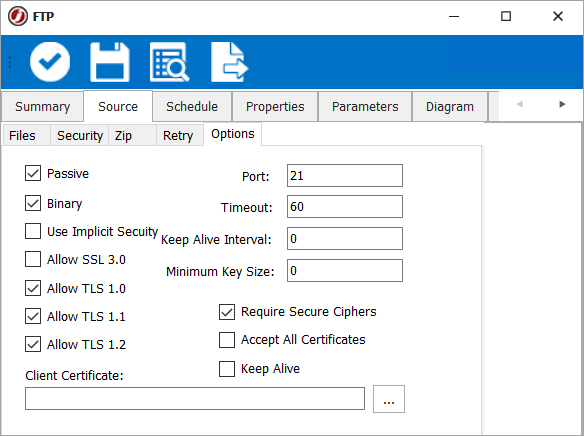
File Transfer using the FTPS File Type
In the File Transfer Job definition using the FTPS Transfer Type, the Options changes significantly from the previous two examples.
Similarly, the Minimum Key Size property functions in the same way as described in the above two sections.
The Allow TLS 1.1 and Allow TLS 1.2 options are also available. These, along with the Allow SSL 3.0 and Allow TLS 1.0 options, provide a fine-grained selection of the SSL algorithm used to authenticate with a remote machine. SSL 3.0 is now considered obsolete and should not be used unless absolutely necessary.
Ideally, TLS 1.2 should be used, but it may not be available on all servers. However, if none of these options are selected, the connection will attempt to negotiate the best available protocol on the particular server.
File Transfer from Workflow Jobs
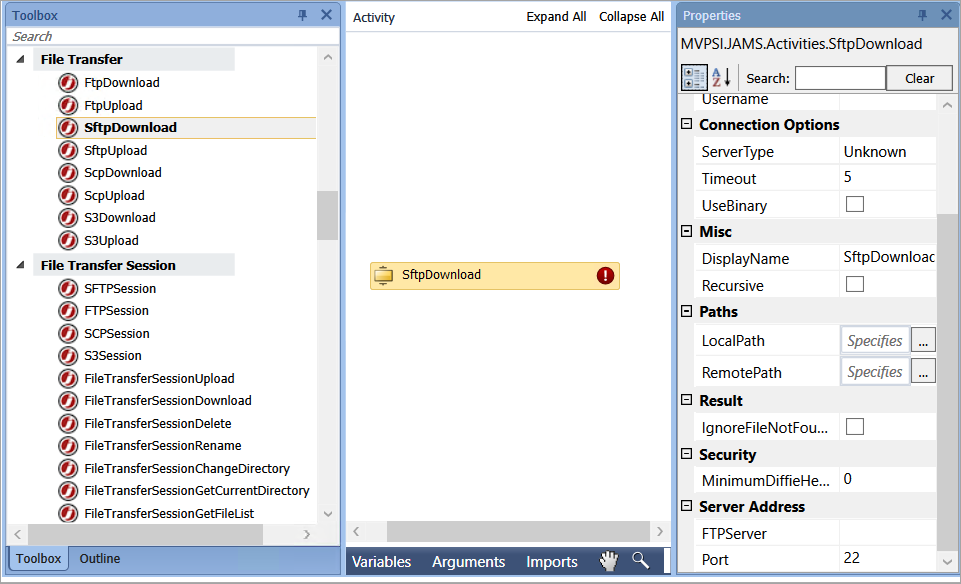
When setting up a Workflow Job, the File Transfer, File Transfer Session, and Mail Server Sessions groups have been also been updated with additional properties for FtpDownload, FtpUpload, and FTPSession shown in the example below:
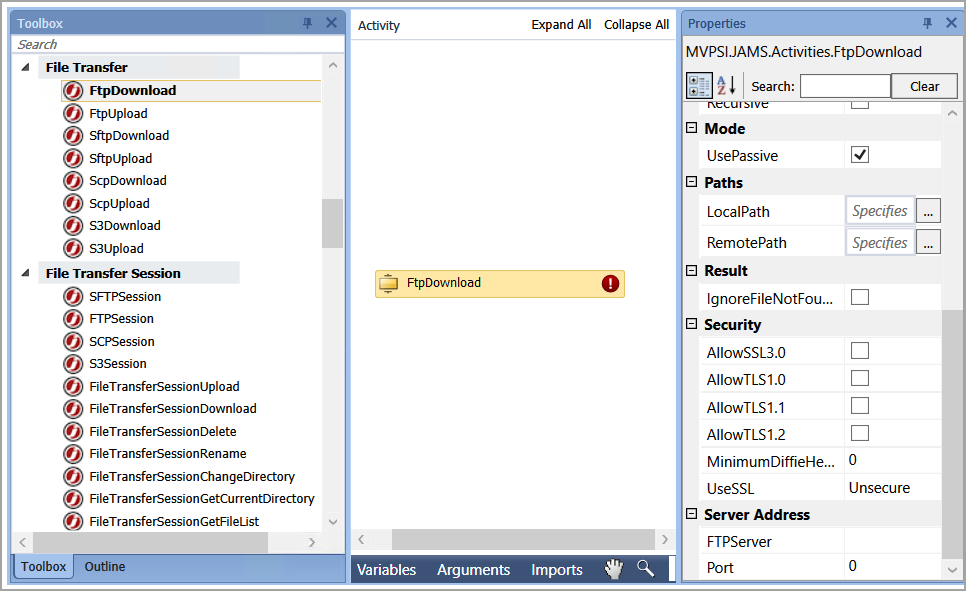
Connection security properties are grouped within the Security section. These options are the same as the previous descriptions for FileTransfer jobs. For FtpDownload specifically, the UseSSL property toggles the SSL connection security on or off.
For SftpDownload, SftpUpload, ScpDownload, ScpUpload, SFTPSession, and SCPSession activities, JAMS uses a new security property called MinimumDiffieHellmanKeySize, (or Minimum Key Size) as described in the previous sections.
For SSH-style connections using large key sizes will automatically disable insecure key algorithms that do not have high enough bit counts.
The IMAPSession, POPSession, ForEachMailMessage, and ForEachAttachment activities also incorporate the same security options from FTPS uploads and downloads.

JAMS PowerShell Plugin Updates for Connect-JFTPS, Connect-JIMAP, Connect-JPOP, and Connect-JSFTP Activities
The JAMS PowerShell also exposes similar parameters for Connect-JFTPS, Connect-JIMAP, Connect-JPOP, and Connect-JSFTP as shown in the series of screenshots below.
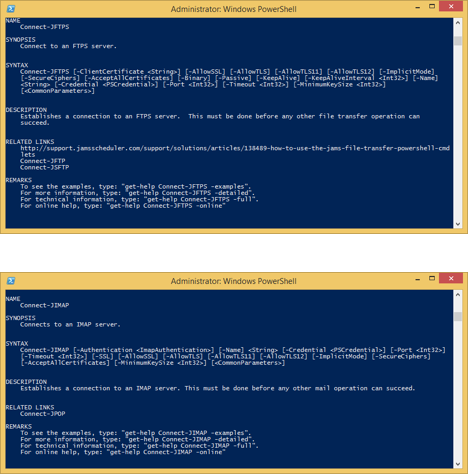
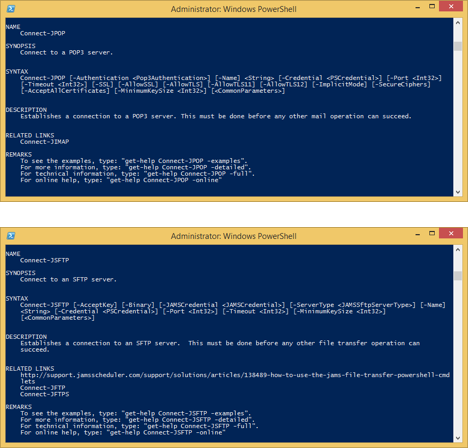
SSH Parameters for SSH Activities
SSH-based FileTransfer (SCP, SFTP) Jobs and WorkFlow Jobs that use SSH activities (ScpDownload, ScpUpload, SftpDownload, SftpUpload, SCPSession, SFTPSession) also add the SSH parameters listed below.
JAMSSshMinimumKeySize - Decimal minimum Diffie-Hellman key size. The default is 1024.
JAMSRsaMinimumSize - Decimal minimum RSA key size. The default is 1023.
JAMSSshCompression - To use compression, select true or false. The default is false.
JAMSSshCompressionLevel - To set the compression level to use, select 0 to 9. The default is 5.
JAMSSshEncryption - Comma separated list of Encryption Algorithms. Select one or more from the list:
- RC4
- TripleDES
- AES
- Blowfish
- Twofish
- ChaCha20Poly1305
JAMSSshHostKey - SSH Host Key Algorithm. Select one or more from the list:
- RSA
- DSS
- Certificate
- ED25519
- ECDsaNistP256
- ECDsaNistP384
- ECDsaNistP521
JAMSSshKeyExchange- SSH Key Exchange Algorithm. Select one or more from the list:
- DiffieHellmanGroup1SHA1
- DiffieHellmanGroup14SHA1
- DiffieHellmanGroupExchangeSHA1
- DiffieHellmanGroupExchangeSHA25
- ECDiffieHellmanNistP256
- ECDiffieHellmanNistP384
- ECDiffieHellmanNistP521
- Curve25519
- DiffieHellmanOakleyGroupSHA256
- DiffieHellmanOakleyGroupSHA512
JAMSSshMacAlgorithm- SSH Mac Algorithm. Select one or more from the list:
- MD5
- SHA1
- SHA256
- SHA512
SSL Parameters for SSL/TLS Activities
SSL-based File Transfer (FTPS) Jobs and Workflow Jobs that use SSL/TLS activities (FtpDownload, FtpUpload, FTPSession, IMAPSession, POPSession, ForEachAttachment, ForEachMailMessage) add the SSL parameters listed below:
JAMSSslMinimumKeySize- Decimal minimum Diffie-Hellman key size. The default is 1024.
JAMSSslCipherSuite - Comma separated list of Ssl Cipher Suites.
- DHE_DSS_EXPORT1024_WITH_DES_CBC_SHA [Vulnerable]
- DHE_DSS_EXPORT1024_WITH_RC4_56_SHA [Vulnerable]
- DHE_DSS_EXPORT_WITH_DES40_CBC_SHA [Vulnerable]
- DHE_DSS_WITH_3DES_EDE_CBC_SHA [Weak]
- DHE_DSS_WITH_AES_128_CBC_SHA [Weak]
- DHE_DSS_WITH_AES_128_CBC_SHA256 [Weak]
- DHE_DSS_WITH_AES_128_GCM_SHA256 [Weak]
- DHE_DSS_WITH_AES_256_CBC_SHA [Weak]
- DHE_DSS_WITH_AES_256_CBC_SHA256 [Weak]
- DHE_DSS_WITH_AES_256_GCM_SHA384 [Weak]
- DHE_DSS_WITH_DES_CBC_SHA [Vulnerable]
- DHE_DSS_WITH_RC4_128_SHA [Vulnerable]
- DHE_RSA_EXPORT_WITH_DES40_CBC_SHA [Vulnerable]
- DHE_RSA_WITH_3DES_EDE_CBC_SHA [Weak]
- DHE_RSA_WITH_AES_128_CBC_SHA [Weak]
- DHE_RSA_WITH_AES_128_CBC_SHA256 [Secure]
- DHE_RSA_WITH_AES_128_GCM_SHA256 [Secure]
- DHE_RSA_WITH_AES_256_CBC_SHA [Weak]
- DHE_RSA_WITH_AES_256_CBC_SHA256 [Secure]
- DHE_RSA_WITH_AES_256_GCM_SHA384 [Secure]
- DHE_RSA_WITH_CHACHA20_POLY1305_SHA256 [Secure]
- DHE_RSA_WITH_DES_CBC_SHA [Vulnerable]
- DH_anon_WITH_3DES_EDE_CBC_SHA [Anonymous]
- DH_anon_WITH_AES_128_CBC_SHA [Anonymous]
- DH_anon_WITH_AES_128_CBC_SHA256 [Anonymous]
- DH_anon_WITH_AES_256_CBC_SHA [Anonymous]
- DH_anon_WITH_AES_256_CBC_SHA256 [Anonymous]
- DH_anon_WITH_DES_CBC_SHA [Anonymous]
- DH_anon_WITH_RC4_128_MD5 [Anonymous]
- ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA [Weak]
- ECDHE_ECDSA_WITH_AES_128_CBC_SHA [Weak]
- ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 [Fast Secure]
- ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 [Fast Secure]
- ECDHE_ECDSA_WITH_AES_256_CBC_SHA [Weak]
- ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 [Fast Secure]
- ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 [Fast Secure]
- ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 [Secure]
- ECDHE_ECDSA_WITH_RC4_128_SHA [Vulnerable]
- ECDHE_RSA_WITH_3DES_EDE_CBC_SHA [Weak]
- ECDHE_RSA_WITH_AES_128_CBC_SHA [Weak]
- ECDHE_RSA_WITH_AES_128_CBC_SHA256 [Fast Secure]
- ECDHE_RSA_WITH_AES_128_GCM_SHA256 [Fast Secure]
- ECDHE_RSA_WITH_AES_256_CBC_SHA [Weak]
- ECDHE_RSA_WITH_AES_256_CBC_SHA384 [Fast Secure]
- ECDHE_RSA_WITH_AES_256_GCM_SHA384 [Fast Secure]
- ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 [Secure]
- ECDHE_RSA_WITH_RC4_128_SHA [Vulnerable]
- RSA_EXPORT1024_WITH_DES_CBC_SHA [Vulnerable]
- RSA_EXPORT1024_WITH_RC4_56_SHA [Vulnerable]
- RSA_EXPORT_WITH_DES40_CBC_SHA [Vulnerable]
- RSA_EXPORT_WITH_RC2_CBC_40_MD5 [Vulnerable]
- RSA_EXPORT_WITH_RC4_40_MD5 [Vulnerable]
- RSA_WITH_3DES_EDE_CBC_SHA [Weak]
- RSA_WITH_AES_128_CBC_SHA [Weak]
- RSA_WITH_AES_128_CBC_SHA256 [Fast Secure]
- RSA_WITH_AES_128_GCM_SHA256 [Fast Secure]
- RSA_WITH_AES_256_CBC_SHA [Weak]
- RSA_WITH_AES_256_CBC_SHA256 [Fast Secure]
- RSA_WITH_AES_256_GCM_SHA384 [Fast Secure]
- RSA_WITH_DES_CBC_SHA [Vulnerable]
- RSA_WITH_RC4_128_MD5 [Vulnerable]
- RSA_WITH_RC4_128_SHA [Vulnerable]
JAMSSslEllipticCurve - Comma separated list of TLS Elliptic Curves.
- NistP256
- NistP384
- NistP521
- BrainpoolP256R1
- BrainpoolP384R1
- BrainpoolP512R1
- Curve25519
JAMSSslVersion- Comma separated list of SSL Versions.
- SSL30
- TLS10 [Any]
- TLS11 [Any]
- TLS12 [Any]