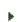Running an Audit and applying Remedies
Now that the Audit Definition has been defined, we will audit our systems against these Strategies, then view and remedy the results.
To run an audit
- In the Audit Definitions panel, choose option 6 next to the Audit Definition you would like to use.
- Choose option 1 next to the systems you want to audit. Since the purpose of this audit is to compare Powertech security settings on other systems with the settings on the management system, your selection should include at least one system other than the management system you are using.
- Press Enter. You return to the Audit Definitions panel.
The duration of an audit depends on the number of systems and user profiles, and may take several minutes or longer.
To view and remedy audit results
- Choose option 9 next to the Audit Definition you just ran.
- Choose option 6 next to the audit record. The Audit System Results panel appears.
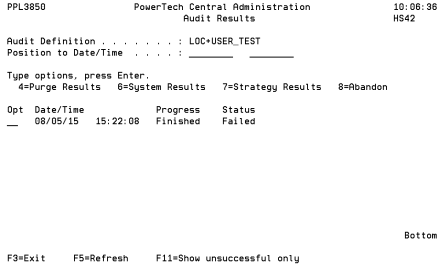
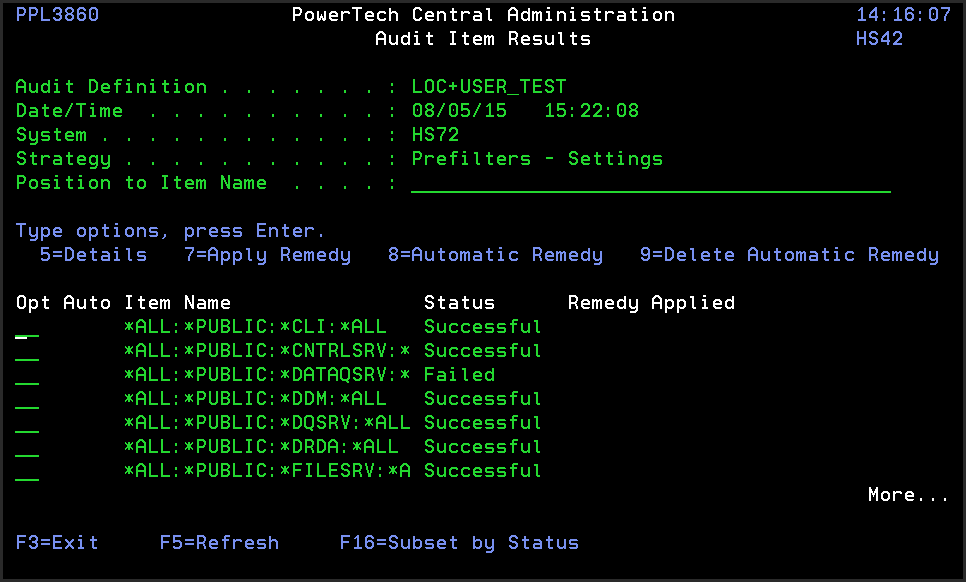
- Choose option 7 next to a system. A list of the Strategies included in the audit appears along with its status.
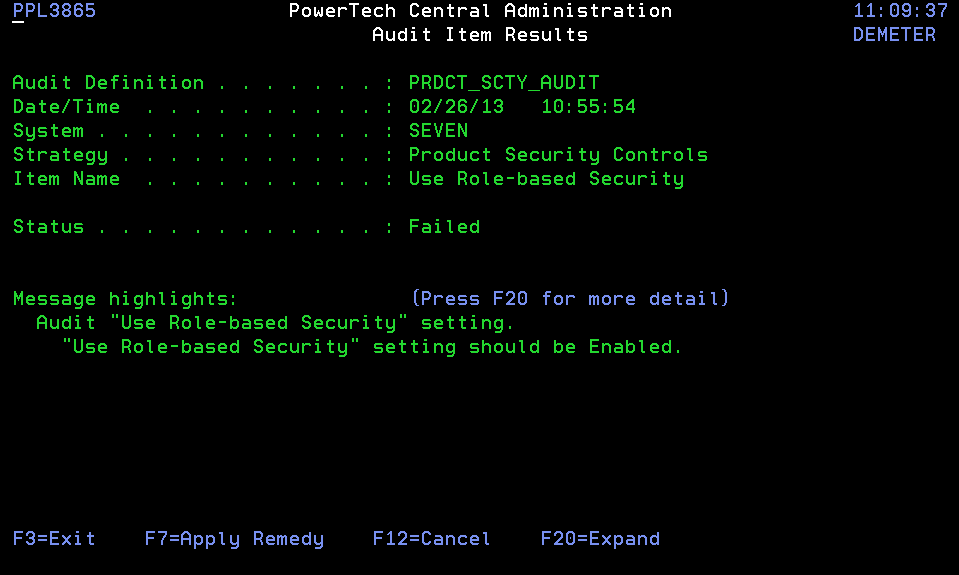
- Choose option 5 next to a failed strategy to view the results. In this case we will view the Product Security Controls Strategy.
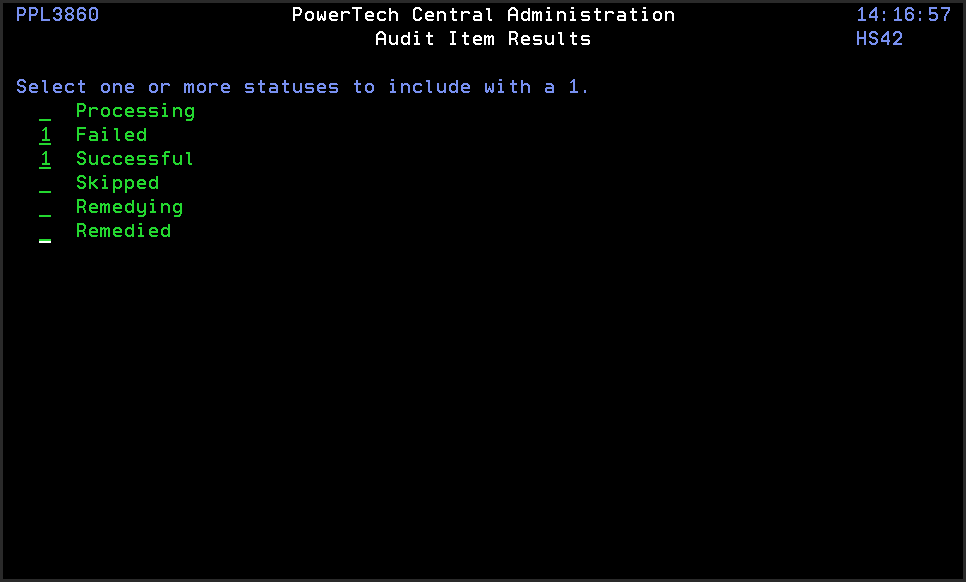
- Press F16 to sort the statuses by processing, failed, skipped, successful, or remedied.
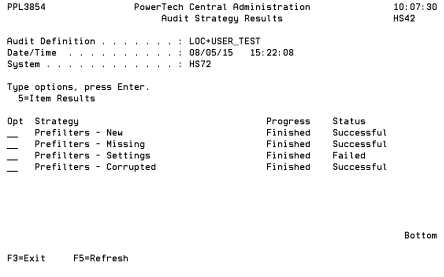
- Choose option 5 next to an item name to view the results.
- Press F7 to apply a Remedy.
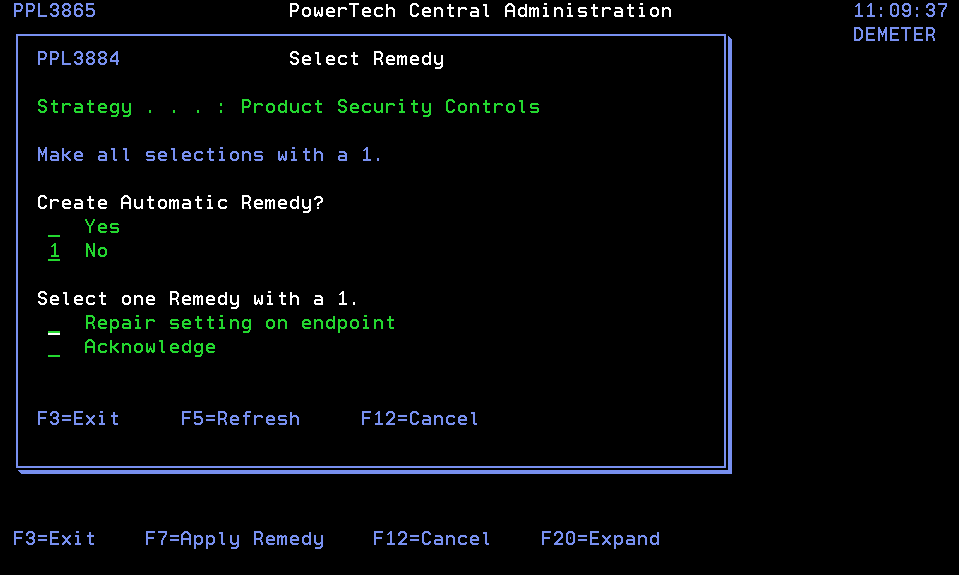
- A Remedy represents a corrective action to be taken when applied to an Item Result with a status of Failed. Remedies fall into three basic classes of actions:
- Acknowledge. Ignores the failure.
- Adjust user profile on endpoint.The value on the endpoint will be updated to the value record as defined in Central Administration.
- Accept new settings. The value record in Central Administration will be updated to reflect the value defined on the endpoint.
All three Remedies are not always available. In this case, for example, "Accept new settings" is omitted because turning off Role-based security is not allowed for the ADMINISTRATOR Role.
- Choose option 1 next to the Remedy you would like to apply.
For this audit, "Successful" means:
Role Integrity: The Role values on the audited systems matched the values defined in Central Administration.
Role User Integrity: The user profiles attached to Roles matched the attachments defined in Central Administration.
Access Right Integrity: The Access Rights of Roles on the audited systems matched the Access Rights defined in Central Administration.
Product Security Controls: The Use Role-based Security setting on the audited systems matched the setting defined in Central Administration.
Role Integrity: The Role values on the audited systems did not match the values defined in Central Administration.
Role User Integrity: The user profiles attached to Roles did not match the attachments defined in Central Administration.
Access Right Integrity: The Access Rights of Roles on the audited systems did not match the Access Rights defined in Central Administration.
Product Security Controls: The Use Role-based Security setting on the audited systems did not match the setting defined in Central Administration.

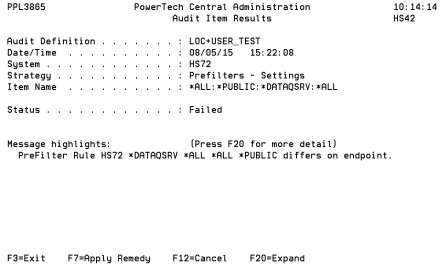
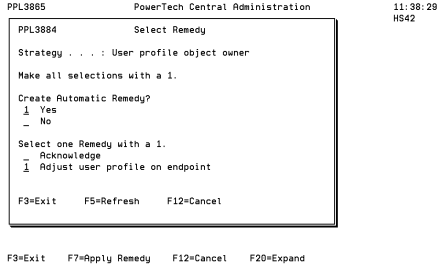
While this example demonstrates a Remedy for the Product Security Controls Strategy, the same basic procedure also applies for the other three Central Administration Strategies.
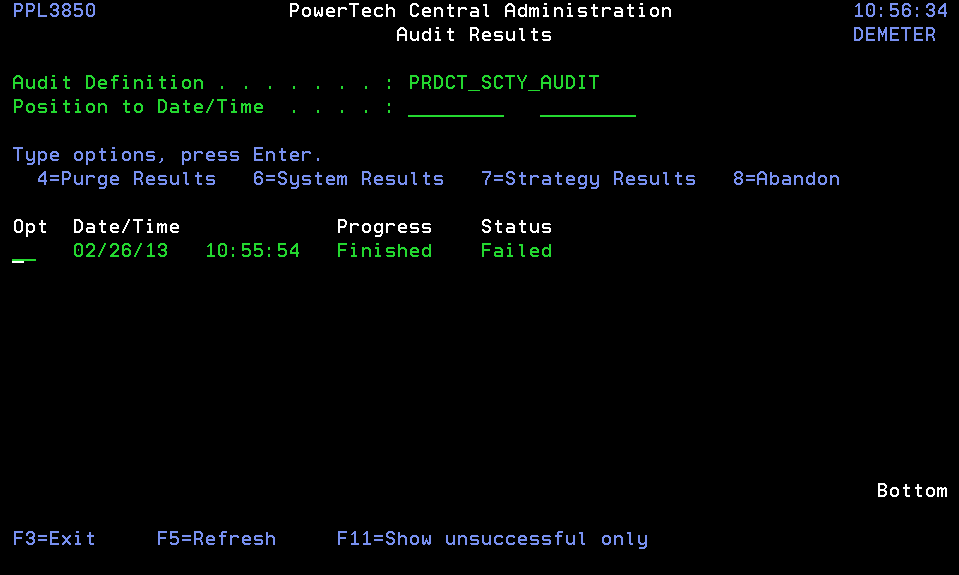
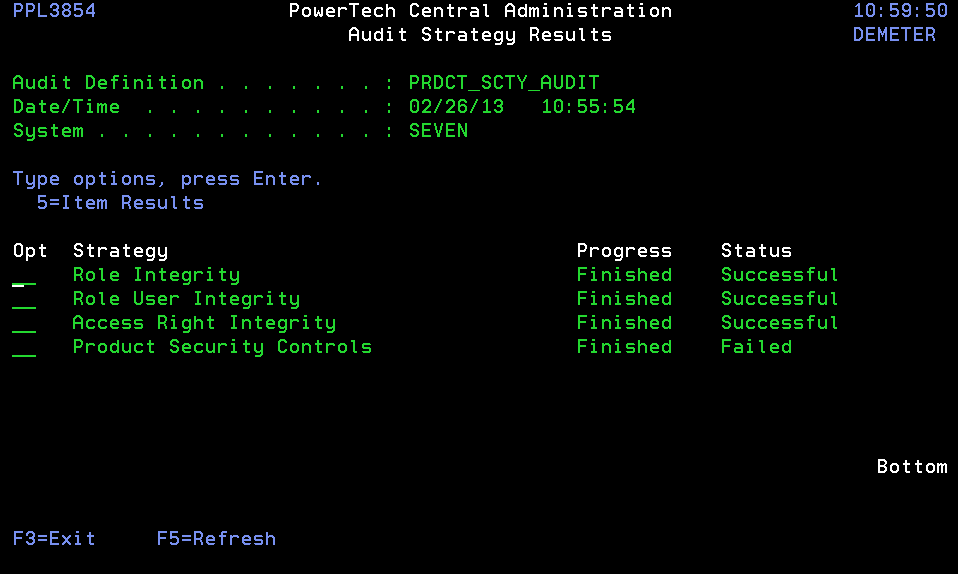
 Audit Strategies
Audit Strategies