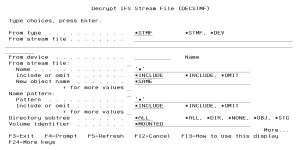
Decrypt IFS Stream File (DECSTMF)
The DECSTMF command allows authorized users to decrypt IFS stream files, which were encrypted with the ENCSTMF command. Files can be restored/decrypted from a device (physical or virtual) or the IFS. Either a Symmetric Key or a Password can be specified for the decryption.
Monitoring for Errors
When executing the DECSTMF command within a CL program, you can trap for errors by monitoring for message id CRE0701.
Auditing
If a Symmetric Key is used for the DECSTMF command and “Log decryption usage” is enabled for the Symmetric Key, then an audit log entry will be generated in the Powertech Encryption for IBM i journal file each time the Key is used for decryption.
Each audit entry will indicate the Label and Key Store of the Symmetric Key which was used, along with the user, date, time, job number and job name.
How to Get There
On the Library/Object/File Encryption Menu, choose option 6.
Options
From file type (FROMTYPE)
Indicate the type of file to decrypt.
The possible file values are:
*STMF Decrypt an IFS stream file.
*DEV Decrypt data from a device.
From stream file (FROMSTMF)
Specify the location of the stream (IFS) file that holds the stream (IFS) files to decrypt.
The possible values are:
ifs-file-name Specify the absolute path of the IFS file that holds the files to decrypt. For instance: '/ABCcompany/Files/Payroll.AES'
From Device (FROMDEV)
Indicate the name of the device to decrypt data from.
Objects (OBJ)
Specifies the objects to be restored. You can specify an object name pattern for the path name to be used. When a path name is specified that could match many objects, you can specify a value for the Name pattern (PATTERN) parameter to subset the objects that are to be saved. A maximum of 25 path names can be specified.
Element 1: Name
The possible values are:
'*' The objects in the current directory are saved.
path-name Specify an object path name or a pattern that can match many names.
Element 2: Include or omit
Specifies whether names that match the pattern should be included or omitted from the operation. Note that in determining whether a name matches a pattern, relative name patterns are always treated as relative to the current working directory.
The possible values are:
*INCLUDE The objects that match the object name pattern are to be saved, unless overridden by an *OMIT specification.
*OMIT The objects that match the object name pattern are not saved.
This overrides an *INCLUDE specification and is intended to be used to omit a subset of a previously selected pattern.
Element 3: New object name
Specifies the new path name of the object.
The possible values are:
*SAME The objects are to be restored with the same names they had when they were saved.
path-name Specify the path name with which to restore the object. If a pattern is specified in the first element, the new path name must be the directory into which to restore any objects that match the pattern. If an object name is specified in element 1, each component in the new path name must exist with the exception of the last component. If the object described in the last component doesn't exist, it will be restored as new.
Name pattern (PATTERN)
Specifies one or more object name patterns to be used to subset the objects to be saved. The Objects (OBJ) parameter defines the set of candidate objects. A maximum of 25 values can be specified for this parameter.
Element 1: Pattern
The possible values are:
'*' All objects which qualify for the operation are included or omitted.
character-value Specify an object name or a pattern that can match many names.
Element 2: Include or omit
Specifies whether names that match the pattern should be included or omitted from the operation.
The possible values are:
*INCLUDE Only objects which are included by the OBJ parameter to be saved, and match the PATTERN parameter are included in the save, unless overridden by an *OMIT specification.
*OMIT All objects which are included by the OBJ parameter are included in the save except those objects which match the PATTERN parameter. This overrides an *INCLUDE specification and is intended to be used to omit a subset of a previously selected pattern.
Directory subtree (SUBTREE)
Specifies whether directory subtrees are included in the restore operation.
The possible values are:
*ALL The entire subtree of each directory that matches the object name pattern is processed. The subtree includes all subdirectories and the objects within those subdirectories.
*DIR The objects in the first level of each directory that matches the object name pattern are processed. The subdirectories of each matching directory are included, but the objects in the subdirectories are not included.
*NONE No subtrees are included in the restore operation. If a directory matches the object name pattern specified, the objects in the directory are included. If the directory has subdirectories, neither the subdirectories nor the objects in the subdirectories are included.
*OBJ Only the objects that match the object name pattern will be processed. If the object name pattern specifies a directory, objects in the directory are not included.
*STG The objects that match the object name pattern are processed along with the storage for related objects. Objects can only be restored using this value if they were saved with SUBTREE(*STG).
Volume identifier (VOL)
Specifies the volume identifier on which the data is being restored.
The possible values are:
*NONE The data is restored from the volume placed in the device.
volume-identifier Specify the identifier of the volume for the restore operation.
Sequence number (SEQNBR)
Specifies the sequence number to use as the starting point for the restore operation.
The possible values are:
*NEXT Search for the encrypted data in the next sequence number on the tape.
sequence-number Specify the sequence number of the stored encrypted data. Valid values range from 1 through 16777215.
Label (LABEL)
Specifies the name that identifies the data file on the tape that is to be used for the restore operation.
The possible values are:
data-file-identifier Specify the data file identifier of the data file used for the save operation. A maximum of 17 characters can be used.
End of media option (ENDOPT)
Specifies the operation that is automatically done on the tape after the restore operation ends.
The possible values are:
*REWIND The tape is automatically rewound, but not unloaded, after the operation has ended.
*LEAVE The tape does not rewind or unload after the operation ends. It remains at the current position on the tape drive.
*UNLOAD The tape is automatically rewound and unloaded after the operation ends.
Allow object differences (ALWOBJDIF)
Specifies whether differences are allowed between the saved objects and the restored objects.
NOTE: 1. To use this parameter, you need all object (*ALLOBJ) special authority. 2. If differences are found, the final message for the restore operation is an escape message rather than the normal completion message.
The types of differences include:
- Authorization list: The authorization list of an object on the system is different than the authorization list of an object from the save operation. Or the system on which a new object with an authorization list is being restored is different from the system on which it was saved.
- Ownership: The owner of an object on the system is different than the owner of an object from the save operation.
- Primary Group: The primary group of an object on the system is different than the primary group of an object from the save operation.
The possible values are:
*NONE None of the differences listed above are allowed on the restore operation. See the description of each individual value to determine how differences are handled.
*ALL All of the differences listed above are allowed on the restore operation. See the description of each individual value to determine how differences are handled.
*AUTL Authorization list differences are allowed. If an object already exists on the system with a different authorization list than the saved object, the object is restored with the authorization list of the object on the system. New objects that are being restored to a system that is different from which they were saved are restored and linked to their authorization list. If the authorization list does not exist on the new system, the public authority is set to *EXCLUDE.
If this value is not specified, authorization list differences are not allowed. If an object already exists on the system with a different authorization list than the saved object, the object is not restored. New objects that are being restored to a system that is different from which they were saved are restored, but they are not linked to the authorization list, and the public authority is set to *EXCLUDE.
*OWNER Ownership differences are allowed. If an object already exists on the system with a different owner than the saved object, the object is restored with the owner of the object on the system. If this value is not specified, ownership differences are not allowed. If an object already exists on the system with a different owner than the saved object, the object is not restored.
*PGP Primary group differences are allowed. If an object already exists on the system with a different primary group than the saved object, the object is restored with the primary group of the object on the system. If this value is not specified, primary group differences are not allowed. If an object already exists on the system with a different primary group than the saved object, the object is not restored.
Use key or password (USEKEYPAS)
Indicate to use a either a key from a key store or a password to decrypt the file. The default is *KEY.
The possible values are:
*KEY Use a key from a key store to decrypt the file.
*PASS Use a password to decrypt the file.
Key label (KEYLABEL) Indicate the label of the key to use for decrypting the data.
The possible values are:
key-label Enter the name of a Key Label in the Key Store.
*AUTO Use the Key Label information stored in the data during encryption.
Key store name (KEYSTR)
Indicate the object name and library of the Key Store which contains the Symmetric Key to use for decryption of the data.
The possible values are:
key-store-name Enter the name of the Key Store.
*DEFAULT Use the default Key Store name specified at the Key Policy level.
The possible library values are:
library-name Enter the name of the library where the Key Store is located.
*LIBL Locate the Key Store within the library list.
Password (PASSWORD) Indicate the password to use to decrypt the data.