High Availability Setup
Follow the steps below to set up Powertech Encryption for IBM i on a High Availability (HA) system and to replicate the Production settings and related user data properly.
Initial setup:
Install Powertech Encryption for IBM i onto the HA system. See the Powertech Encryption Installation Guide.
A license key for Powertech Encryption for IBM i is required on the HA system.
Manual replication:
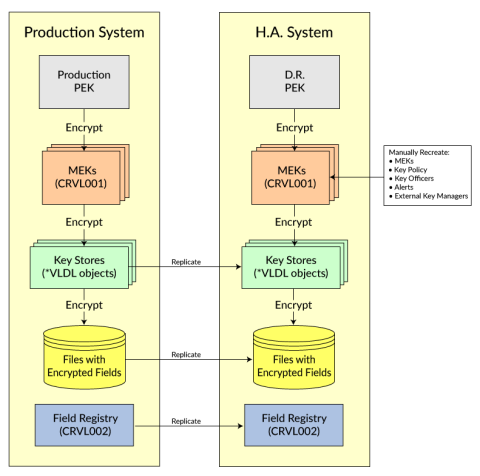
Powertech Encryption for IBM i’s Key Policy settings, Key Officer settings, Security Alert settings and Master Keys are stored in a Validation List (*VLDL) object named CRVL001. This CRVL001 *VLDL object is encrypted with a Product Encryption Key (PEK), which is unique to each IBM i serial number. Therefore, any changes to those settings on the Production system will need to be manually applied to the HA system using Powertech Encryption for IBM i’s commands and screens.
Follow the instructions below to manually apply those settings on the HA system:
Key Policy Settings
If Powertech Encryption for IBM i’s Key Policy settings are changed on the Production system, then those Key Policy settings need to be also changed on the HA system by following these steps:
- On the Production system, display the Key Policy settings using the command CRYPTO/DSPKEYPCY and record the values displayed.
- On the HA system, change the Key Policy settings using the command CRYPTO/CHGKEYPCY using the recorded values from the Production system.
Key Officers
If Powertech Encryption for IBM i’s Key Officers are added, changed or deleted on the Production system, then those changes need to be applied on the HA system by following these steps:
- On the Production system, display the Key Officer settings using the command CRYPTO/WRKKEYOFR and record the values displayed.
- On the HA system, configure the Key Officers by using the command CRYPTO/WRKKEYOFR using the recorded values from the Production system.
Security Alerts
If Powertech Encryption for IBM i’s Security Alerts are added, changed or deleted on the Production system, then those changes need to be applied on the HA system by following these steps:
- On the Production system, display the Security Alert settings using the command CRYPTO/WRKCCALR and record the values displayed.
- On the HA system, configure the Security Alerts by using the command CRYPTO/WRKCCALR using the recorded values from the Production system.
Master Keys
If Powertech Encryption for IBM i’s Master Keys are Set on the Production system, then those Master Keys must also be Set on the HA system by following these steps:
- On the HA system, enter the passphrase parts for each Master Encryption Key (MEK) using the LODMSTKEY (Load Master Key) command. These passphrase parts must be entered exactly as they were on the Production system.
- On the HA system, generate (set) each Master Encryption Key (MEK) using the SETMSTKEY (Set Master Key) command.
Automatic replication:
Configure your High Availability (HA) product to replicate the following objects on an ongoing basis:
- Your user-created Key Stores are created as Validation list (*VLDL) objects. The names (and library locations) of these *VLDL objects are those names that were specified on the CRTKEYSTR (Create Key Store) command, unless they were later moved or renamed. These *VLDL objects should be replicated by your HA product from the Production system to the HA system.
- Replicate the CRVL002 *VLDL object from the Production system to the HA system. This object contains the Field Encryption Registry. To avoid issues on the initial replication, ensure that CRVL002 Keystores, and any related Authorization Lists have been replicated to the Target HA system prior to any encrypted data arriving. To properly encrypt and decrypt data, the CRVL002 validation list object (and Authorization Lists) will be referenced as any encrypted data files are being replicated over to the Target system.
you use external files (instead of field procedures);
you have a high-volume environment with many new inserts occurring; and
the 'Last Index Number' is stored in CRVL002 (instead of the PF choice).
- If you use the Field Encryption Registry and are using external files to store encrypted database field values and if the ‘last index numbers used’ are stored in the physical file option [LSTINDSTG(*PF) parm on the Registry], then replicate the physical file named CRPF002.
- Replicate any IBM i Authorization Lists that may be used to secure Key Stores or to secure fields in the Field Encryption Registry. Add your replication software service profile to the full authorization object (*AUTL) used in the field encryption registry for each field in the files being replicated. NOTE: When using a replication product for automatic replication, the user profile running the Apply Job must be in the ‘Full’ authorization list that apply to any encrypted files being replicated.
- Replicate the Powertech Encryption for IBM i authorization lists PCRADMIN and PCRREPORT.
- DO NOT replicate the CRVL001 *VLDL object from the Production system to the HA system. The settings in CRVL001 are encrypted with the Product Encryption Key (PEK), which is unique per IBM i serial number.
- Field encryption is normally implemented using field procedures. However, in a legacy environment, field encryption entries may be using external files. In that case, replicate the external files from the Production system to the HA system. You can find the names of those external files by running the CRYPTO/WRKFLDENC command and placing an option 5 next to each *ACTIVE field entry.
- If you are using Field Procedures and the Decryption Accelerator (*YES) for any Field Registry Entries, upon initial replication using the Sync feature (not save/restore), perform the following command on the Target HA system before doing the initial sync:
CHGFCNUSG FCNID(QIBM_DB_SECADM) USER(APPLYJOBUSERID) USAGE(*ALLOWED).
This command needs to be executed by a user with SECADM or SECOFR authority. For more information, see Appendix G: Decryption Accelerator Prerequisites and Limitations or contact Powertech Technical Support.
High Availability Diagram