Symmetric Key Management
Symmetric Key Cryptology (also known as Secret Key or Private Key Cryptology) is a form of cryptology in which the same Key can be used to encrypt and decrypt data.
Symmetric Keys must be strong enough for the intended application. Because the strength of the Symmetric Key is determined by its length, the longer the key, the harder it is for high-speed computers to break the code. Within Powertech Encryption for IBM i, Symmetric Keys may be generated up to 256 bit lengths to provide a high level of protection.
The Symmetric Key values must be kept secret to prevent unauthorized decryption of sensitive data. Controls must therefore exist to protect the confidentiality and access to the Symmetric Keys. Powertech Encryption for IBM i provides an integrated and comprehensive Symmetric Key Management System to establish those controls.
A Cipher is a pair of algorithms (mathematical processes) used to encrypt and decrypt data.
A Key is the information needed to control the detailed operations of the Cipher. In contrast to human-generated passwords, Keys are more secure since they are computer-generated and are represented as an obscure series of bits (1001110…).
Powertech Encryption for IBM i’s Symmetric Key Management System allows organizations to:
- Establish policy settings on how Symmetric Keys can be created and utilized
- Indicate which users can create and manage Symmetric Keys
- Randomly generate strong Symmetric Keys
- Protect Symmetric Keys using Master Encryption Keys
- Protect the recreation of a Master Encryption Key by requiring passphrases from up to 8 users
- Organize Symmetric Keys into one or more Key Stores
- Restrict access to Key Stores using IBM i object authority
- Restrict the retrieval of the actual Symmetric Key values
- Provide separation of duties (e.g. the creator of a Symmetric Key can be restricted from using the Key to encrypt and/or decrypt data)
- Control which users can utilize Symmetric Keys to encrypt and decrypt data
- Produce detailed audit logs
Symmetric Key Hierarchy
Powertech Encryption for IBM i provides a multi-level security architecture to protect Symmetric keys on the IBM i. The diagram for this hierarchy is outlined below (with descriptive text following the diagram).
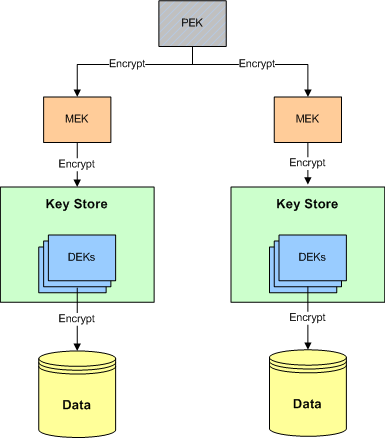
A Data Encryption Key (DEK) is a Symmetric Key which is used to encrypt and decrypt data. An organization can create one or more DEKs using Powertech Encryption for IBM i. For instance, a DEK could be created to encrypt/decrypt credit card numbers and a second DEK could be created to encrypt/decrypt social security numbers.
A DEK should be randomly generated by Powertech Encryption for IBM i in order to provide the highest degree of protection. Depending on your organization’s key policy, you can additionally have Powertech Encryption for IBM i generate a DEK which is based on a passphrase entered by the user.
Data Encryption Keys (DEK) are contained within Key Stores. You can create one or more Key Stores on the IBM i using Powertech Encryption for IBM i. For instance, one Key Store could be used to contain DEKs for protecting Order Entry data, and a second Key Store could be used to contain DEKs for protecting Payroll data.
A Key Store is created as a *VLDL (Validation List) object on the IBM i. You can control access to the Key Store *VLDL object using IBM i object security.
A Master Encryption Key (MEK) is a special Symmetric Key used to protect (encrypt) the Data Encryption Keys (DEKs) contained in a Key Store. An organization can create up to 8 MEKs per environment on the IBM i. For instance, a MEK could be used to encrypt the Order Entry DEKs contained in a Key Store, and a second MEK used to encrypt the Payroll DEKs contained in another Key Store.
A MEK is generated by Powertech Encryption for IBM i using passphrases entered by designated users. Depending on the organization’s key policy, up to 8 different passphrases can be required (by different users) in order to generate a MEK.
MEKs are stored in a *VLDL (Validation List) object on the IBM i called CRVL001.
A PEK is used by Powertech Encryption for IBM i to protect (encrypt) the Master Encryption Keys (MEKs) and user-defined settings (i.e. Key Policy, Key Officers, Security Alerts, etc).
Powertech Encryption for IBM i automatically generates the PEK using a combination of the IBM i serial number and a secret value. The PEK only resides in memory as-needed and is never stored.
Data Encryption Keys
A Data Encryption Key (DEK) is a Symmetric Key which is used to encrypt and decrypt data. An organization can create one or more DEKs using Powertech Encryption for IBM i. For instance, a DEK could be created to encrypt/decrypt credit card numbers and a second DEK could be created to encrypt/decrypt social security numbers.
A DEK should be randomly generated by Powertech Encryption for IBM i in order to provide the highest degree of protection. Depending on your organization’s key policy, you can additionally have Powertech Encryption for IBM i generate a DEK which is based on a passphrase entered by the user.